
[Nathan McFeters] and [Rob Carter] gave a presentation on the problems with URI handling. URIs are used to send commands to external applications from a web browser. itms:// for iTunes for example. Any application that registers a URI has the potential to be abused through this route. For their first example they showed a stack overflow in Trillian’s AIM handling. The next demo created a “Critical Update Available” button on Picasa’s interface. When the user clicked it, their photos would be uploaded to the attacker’s server. They even display a “download progress” bar to encourage the user to keep the connection open. You can read about the attack on cocontributor Billy Rios’s blog.
Month: October 2007
ToorCon 9: CDMA Unlocking And Modification

[Alexander Lash] gave a short overview of what you need to unlock a CDMA phone. He strongly recommended Howard Forums for finding most of the info you need. You’ll probably need BitPim and the Qualcomm PST (product support tools). Using the PST you can flash your new carrier’s firmware and then activate the phone on their network.
Verizon offers two ways to get unlimited EVDO data. $59 for a data plan or $15 for VCast. You’re not supposed to be able to use your VCast phone as an EVDO modem and it sends a different network access identifier (NAI) if you tether the phone. Using the PST you can change the NAI and use the cheaper VCast plan for data access. Here is a forum post detailing the process.
Drive Bay PoE Adapter

Sure, we’ve seen Power over Ethernet before – I even whipped up a simple adapter for my modded wrt54gs. This is a nice clean setup, and it’ll save you from yet another power brick. (I’ve got a power strip dedicated to the things in my tiny home data center.)
ToorCon 9: Real World Fuzzing

We dropped in on [Charlie Miller]’s fuzzing seminar at the end of the day yesterday. Fuzzing become a fairly popular topic in the last year and essentially involves giving a program garbage input, hoping that it will break. If it can’t handle the fake data and fails in a non-graceful fashion, you could have found a potentially exploitable bug. Fuzzing is a fairly simple idea, but as Charlie points out, without some thinking while you’re doing it it’s unlikely to be very productive.
ToorCon 9: Crypto Boot Camp

[Rodney Thayer] gave a 2 hour seminar on cryptographic technology. It was designed to give the audience a working knowledge for dealing with vendors. He gave some rules of thumb for choosing encryption. In order of preference, when doing symmetric key crypto: use AES with a minimum 128bit key, if not that 3-key Triple-DES, or last RC4 with 128bit key. For hashing: SHA 256 preferred, SHA 1 if you can’t do any better, and MD5 if you can’t SHA. For public key: RSA using at least a 2048bit key. The top choices in these lists were picked because they’ve stood up to years of scrutiny. One major theme of talk was to never roll your own crypto algorithm or buy someone elses. Proprietary algorithms get broken all the time, like the GSM A5 crypto we talked about earlier this year.
Optical Headphone Amp

It looks like this one’s been out there for a while, but it doesn’t make it any less awesome. [Andrija] built this combination portable DAC/headphone amp. It takes optical audio input, feeds it through an analog devices AD1866 16bit/96khz decoder. After that, the audio is brought up to volume by an op-amp style headphone amp circuit.
Side note: I wrote up a few short notes on the Sidekick LX I got today, if you dig that sort of thing.
Speaker Power Detection Circuit
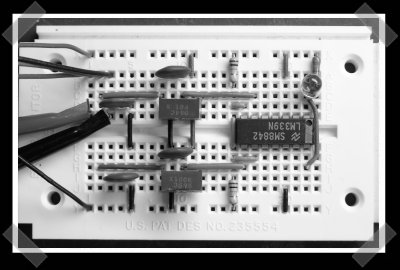
This is an interesting way to monitor your speakers. [Keith] put together this speaker line monitor after a commenter requested it on his blog. It’s designed to check for power on the speaker line and drive a logic/led output. Apparently there’s some risk of shorting your amp, so he’s planning to redesign the input stage. Still, it’s neat little hack to keep an eye on things. Personally, I’d just put em on their own class A amp and automate the power switching, but there are plenty of situations where this could be useful.










