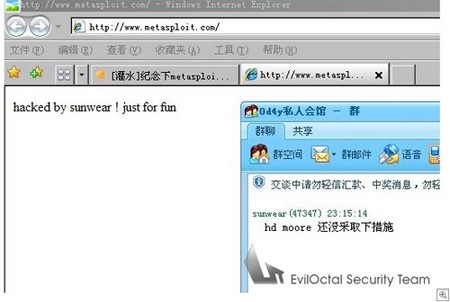
You’ve no doubt heard that the site hosting Metasploit, the exploit framework, was hacked earlier this week, but what you may not have heard is that it was done using a layer 2 attack. Though Metasploit.com was not actually cracked, a server on the same VLAN was compromised and used to ARP poison the gateway. ARP poisoning is a method of sniffing data by sending a false ARP message to an Ethernet router to associate the hacker’s MAC address with a valid IP address from a genuine network node. From there the hackers were able to mount their MITM attack and show the image above instead of Metasploit’s website. This problem could have been avoided if the ISP was using fixed ARP entries, which is what [HD Moore] had to do to get the site back online. [Richard Bejtlich] points out that even though most people have been focusing on application security lately, fundamental attacks like this still happen. If you’re doing a good job protecting yourself, you can still be at the mercy of the security of 3rd parties when operating in shared hosting environments.
5 thoughts on “ARP Poisoning Is Still A Problem”
Leave a Reply
Please be kind and respectful to help make the comments section excellent. (Comment Policy)















Man, it blows me away how much we keep learning about this stuff!
-Taylor
Thats pretty intense
yeah…..like you can learn a lot about hacking from a news article.
Taylor, does hackaday pay you to make positive comments about their crappy submissions? All i ever see you write is positive happy quippets about how much we are learning…..when obviously nobody has hacked anything.
no writeup?
no schematic?
NO HACK!
If i wanted to read news, i would have gone to newsaday.
Man, it blows me away how much we keep forgetting about this stuff! The ARP poisoning attack is old enough to vote, and the only OS I know of that’s hardened against it is OpenBSD. Ohwell…. back to the drawing board.
Well that was a pretty clever way for them to do that. Everything on a lan is only as secure as the lan’s weakest link.