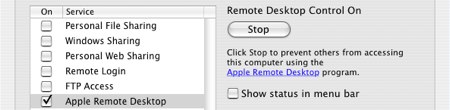
Yesterday, Slashdot reported a privilege escalation vulnerability in OSX. Using AppleScript you can tell the ARDAgent to execute arbitrary shell script. Since, ARDAgent is running as root, all child processes inherit root privleges. Intego points out that if the user has activated Apple Remote Desktop sharing the ARDAgent can’t be exploited in this fashion. So, the short term solution is to turn on ARD, which you can do without giving any accounts access privileges. TUAW has an illustrated guide to doing this in 10.4 and 10.5.
5 thoughts on “Neutering The Apple Remote Desktop Exploit”
Leave a Reply
Please be kind and respectful to help make the comments section excellent. (Comment Policy)















BREAKING NEWS: APPLE NOT AS SECURE AS IT’S MORONIC USERS ASSUMED!
Preston:
1) The company’s name is Apple. The OS name is Mac OS X.
2) Who the hell in their right minds would claim a system is impenetrable? There will always be faults; only non-technical people would say such a thing — and if you’re referring to such people, then you’re basically making fun of people for their technical illiteracy (== not good).
3) Not all Mac^H^H^HApple users are moronic. In fact, most of them know grammar.
4) The genitive of “it” is “its,” not “it’s.”
Might want to point out that this is a local and not remote exploit.
This is a pretty simple flaw – direct execution of script. Any brief look at the design could’ve spotted that one. I wonder how many more complex vunrabilities will show up when the experts really dig into it? Hopefully apple will design system wide security features like address randomisation and the NX bit to eliminate lots of vunrabilities all at once.
I’m so lucky to have found this blog. You literally told me exactly what I wanted to hear and then some. Beautiful writing and thanks again for making this free!