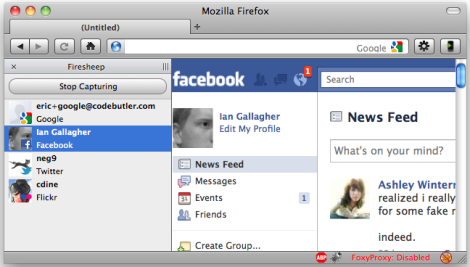
Often, software hackers are the activists that push software giants towards updating vulnerable applications. In todays example, [Eric Butler] is pushing Facebook, Twitter, Flickr, and more all at the same time. By creating a user script-kiddie friendly extension for Firefox, he has allowed just about anyone to sniff unsecured connections on public Wi-Fi access points and log into these unprotected accounts.
Right now the extension is available for Windows and Mac, with a Linux port coming soon. Temporarily, the best way for a user to avoid getting taken advantage of would be to not use these social networking sites on a public connection, or to implement a secure proxy for these connections that would keep your data safe. Hopefully these websites will have a quick rebuttal that allows for security without workarounds. With all of the bad press they are recieving, they certainly have incentive to.
Are there any software or security buffs out there? We would love to see someone port this to an iPhone or Android app that could check and log open Wi-Fi points. We’ll leave the foot work to the experts out there, but do be sure to give us a heads up if anyone manages to make it happen, okay?
















“By creating a user script-kiddie friendly extension for Firefox, he has allowed just about anyone to sniff unsecured connections on public Wi-Fi access points and log into these unprotected accounts.”
“We would love to see someone port this to an iPhone or Android app that could check and log open Wi-Fi points.We’ll leave the foot work to the experts out there, but do be sure to give us a heads up if anyone manages to make it happen, okay? ”
Wait are you complaining about people writing scripts in one paragraph enabling “any one” (more like those that dont know how) to do things in one paragraph, and then taking the high ground in the next saying youll leave the foot work to the experts as you publicly admit your one of the people you just complained about programmers writing scripts , and ports of said scripts for.
Im confused , did i miss the punch line?
Installed!
What version of firefox is this for?
firefox 3.6.12 and 3.6.11 in that virsion firesheep is suporrted.
LOL, I like kiernan’s comment :)
Not sure about Facebook, but I know Twitter’s API supports SSL sessions. Echofon has an option to use SSL for all communications, not just login, which would seem to circumvent the cookie sniffing.
I do believe my coworkers and I will be playing with this tomorrow on the new AP we are setting up.
@kiernan Double that.
I really hope this will also capture wired LAN packets if you are on the same router as the wifi AP (I assume it does ARP poisoning)…
It does not do ARP poisoning, but there are tons of tools out there
:( won’t install on Firefox 3.6.8…
What do we have to do to provide these individuals with enough INTERESTING things to play with so that they don’t bother repeating this boring old shit over and over again?
Oh WOW! You’ve noticed my updates about my CAT aren’t encrypted! You’re so CLEVER! Clearly now we should all waste processor cycles (and therefore battery life) and export regulator’s time and debugging time (ever tried to debug a protocol that uses SSL? No? It isn’t fun.) and encrypt it all! Whew. Close one there! Thanks for pointing out our collective stupidity in not encrypting all this crap.
We really need a how-to for this thing. Got it installed along with that other packet sniffer that it says the windows users need and I’m on a network where i can plainly see people on the book of faces and I’ve got nothing. My computer says that the network is unsecured too.
First thing it does on OSX is ask for an admin password. So do you type it in like a good little sheep?
“First thing it does on OSX is ask for an admin password. So do you type it in like a good little sheep?”
Well, if you were stupid enough to pay over the odds for a second rate computer which cant run applications of any real use, you may as well just end it all and give your password out anyway.
Downloaded!
@stib.
I have no usage for this application, but am a Mac user. Obviously the application needs access to system files, like 99.9% of OS X applications do, and require your admin password.
@Audin
Allow me to enlighten you. Sit in a cafe for a few hours during lunch, or near a hotel in the evening, sniffing packets. You will collect vast amounts of data.
What this tool allows you to do is hijack a session. What’s that mean? Well, once you’ve hijacked their session on their cat’s facebook account, you can see all the private data within. Probably an address, phone number, etc. You’re half way to identity theft, or just major harassment. Lolcats need privacy too!
Seriously though, debugging things with SSL is not that difficult (which is irrelevant anyway, we’re not talking about a new PROTOCOL, we’re talking about using HTTPS, which is trivial to enable), and this attack is quite legitimate given the amount of personal information people keep in places like this.
Works on 3.6.11, for those that are wondering (64 Bit Windows 7)
Oct 31st?
“We would love to see someone port this to an iPhone or Android app that could check and log open Wi-Fi points.We’ll leave the foot work to the experts out there, but do be sure to give us a heads up if anyone manages to make it happen, okay? ”
How far up (and into what?) did you want to stick your head? This functionality is already built into “commercial” android devices. Google uses it to determine your position. Apple is doing this as well now. The information is correlated with GPS and cell-tower statistics, and i assure you, each and every open AP that has been accessed by an android phone has been reported back to the folks at “Do no Evil(tm)” land; In many cases, open access points are a faster and better source of (~200′ range) location information than GPS.
Privacy is not quite dead yet, but I assure you that anonymity is long past pining for the fjords. The public is just catching on, but this has already become SOP for microsoft, apple and goofle. The phone companies already had cell-tower fixes from the E911 legislation.
And if anyone thinks that SSL accomplishes anything more than making it hard to read your data while sniffing on the fly, you’re out of date, mate. Go ahead, look at all the certs installed on your browser. HTTPS is about as secure as a yale lockset.
Got IPV6? I’ll bet you have it even if you think you have it turned off. It’s magic! Well, I’ll just stop here. No sense in letting all of the cats out of the bag in one sitting. It sort of wrecks it for the tinfoil hat crowd…
Very nice implementation of a very simple concept.
I love it! a user friendly graphical UI for packet filtering, and it filters just what you want! :D I’ve already used wireshark before for this kind of stuff, but this is great! now I can steal your amazon password with little work at all! ship everything to an empty house with an alias’s name and then drive by to pick up my free package!
So, let check it out …
I don’t get it – how the fuck do I use this? Open it in Firefox 3.6.11. Configured for Airport in the preference pane and … nothing.
Installed on FF 3.6.11 on W7x64
You have to start the sidebar in FF otherwise it looks like it doesn’t install but it does.
Now lets start some ARP spoofing in the Company and fire up that baby :)
@bilbao bob
First, those lazy bastards must implement HTTPS. Afterwards there will be hacks aimed at why it still allows reading data on the fly. And — surprise! — this time online banking will automatically become a convenient target (due to same certificates in browser), therefore the pressure to make things work at last will be way, way stronger.
Uh hum, Perhaps best not to upload your personal info to social networking sites? My address is 46 Acacia Avenue and my social security number is 987-65-4320 DOB 08/12/73 Oh wait i must be banana man!
@bilbao bob
I really shouldn’t lower myself to respond to you but my morning caffeine hit hasn’t kicked in yet so I’m half the man I normally am.
The location-awareness functionality offered by Android handsets is very different to the WiFi sniffing James was writing about in this article.
Android merely looks at the access point names and triangulates your location back at their HQ based on the visible SSIDs which they collected when they were snapping up Street View imagery. This works irrespective of the security settings of the hotspots in question since no connection is made to them. The lsit of SSIDs is sent back and forth via your 3G connection if you are not connected to a WiFi network.
Meanwhile, James was suggesting an app which scans for unsecured hotspots, connects to them, sniffs for Facebook authentication data and logs it for later exploitation.
Hope that’s cleared it up for you, old timer ;)
Can I just confirm something: are you saying that google has actually bothered to gather a list of SSID’s and Lat / Long positions? Doesnt everyone else change their SSID regularly, and doesnt half the world have either “BT HOME HUB” or “Linksys” or “Netgear” as their SSID?
A x
@alex
They’re talking about MAC addresses maybe (BSSID), they are relatively static. Otherwise it’s like you said.
Though google is still telling me I’m at my previous apartment, because I took my AP with me.. so a few drawbacks.
@Ax
because WPA hashes are salted with the SSID, most broadband providers now append a 5 or so digit number to the end of each SSID, so it’s unique and people can’t use the cowpatty WPA ‘rainbow’ tables or realistically generate generic ones. this uniqeness is also helpful for when google does a drive by on unsecured ones and accidentally saves the information they gather.
i dont think manufacturers do this yet though, so there are probably loads of ‘netgear’ and ‘linksys’ SSIDs even if there are no longer plain old BT HOME HUB and O2Wireless ones.
@SD
Adding to what you said, it’s also a feature that YOU TURN ON.
With Android, pretty much everything privacy related is asked of you before installation. Google asks if it’s ok to collect certain data, apps say that they need GPS locations, etc…
Privacy isn’t dead. We’re willingly giving it away in some cases & in others we choose to hold onto it for dear life. Like anything else in life, it’s all about the context.
@SD –
The drive around stuff was before they realized that android users could do it for them much better than rolling around their little cars… which are being redone to be much less noticeable, btw. This caused no small amount of friction between verizon and google, largely because verizon hadn’t made much money off the data yet.
BTW, the access point triangulation is still in beta stage. The data is being gathered very quickly by using cell tower fixes, even if this is somewhat behind the scenes.
…and you knew that Google is in the process of doing UAV evaluations, right? Google was founded by a couple of bright guys, but that wasn’t how they succeeded in becoming the biggest thing since sliced bread. They succeeded because the guys who work behind the door marked “THEY” had some serious money available [pallets of it, evidently], in exchange for a big piece of the action and access to all that raw information.
I’m not a tinfoil hat guy – this stuff is all common sense, and as I said, I’m all for it… I just want it to be common knowledge to everyone not paying attention.
Apple has recently embraced this – you cannot connect to the mother ship in itunes without acknowledging that you explicitly give them the right to track and use your location information. Why does apple make you agree [even though you lose access to the apple world if you decline] by checking a box when google just presumes?
And the google privacy stuff you’re agreeing to? Look closely – that’s just you agreeing to give your data to third parties and apps. Google still gets and keeps everything, regardless of your settings. Oh, it may split into separate tables, but it can be associated with a single query.
@piipi – yes, basically wireless protocol mac addresses. Rename as you like – the info stays the same.
Well, from the smell of it, I’ve spread enough FUD on the garden for one day. :)
Caution: Everything I write is obviously fictional, and any resemblance to actual people, places or activities which are going on as I write this, is pure coincidence.
Of course, the fact that you can comb the rulings and legislation of your own state(s) and the feds/DOJ websites and discover that legislation is already in place to protect these applications from SCOTUS review should be no cause for alarm.
And as they say, only shoplifters turn their heads up to look for the cameras.
hi,
when i try to use this extension this error is shown:
ReferenceError: Cc is not defined
the ReferenceError:Cc is not defined occurs when you dont have winpcap installed
Nurse! I think Bob needs his dosage increasing…
I already installed it but it seems like it doesn’t work because it does capture any interface in my network!!! any suggestions!!!??
I already installed it but it seems like it doesn’t work because it does NOT capture any interface in my network!!! any suggestions!!!??
“ReferenceError: Cc is not defined” appears when I want to change preferences even if Winpcap is installed before or after Firesheep on a Windows XP SP3 Netbook.
Maybe it’s because it’s because of WIFI card drivers?
Please can someone give solutions it’s a problem that occured on a lot of discussion.
how do i install the application?
how do i insall the application for windows 7 64bit ?
This is how to install Firesheep to hack Facebook or Twitter accounts. This is disseminated for educational purposes only and not recommended for general use. However, I have posted already earlier how to protect your account information from this hacking software that can hack Facebook, Twitter or other accounts.
Source: http://www.bazics.net/2010/10/how-to-install-firesheep-that-can-hack.html
Hello, It wont install on my Firefox 3.6.8 (Im Using the newest Mac OS X) Please help
Given that most people dont know jack squat about arp spoofing, this tool wont do them much good, its still going to get the media, at least online hyped up when they dont know anything about how it works and they’ll be scream omg we are being haxxored. /sigh
Hi,
I installed the plugin, set up WINPCAP (rebooted to be sure), opened Firefox and started capturing. It works! Unfortunately it only captured sessions when they were logged into on this computer :(
Can anyone explain how to do? I’m a bit new to all this :)
Thanks!
After installing WinPcap, the Preferences dialog box seems to be working. That is I no longer have the “Cc is not defined” messages. I also see my WiFi card in the Capture Interface
Good to see idiots making more tools for script kiddies. I hope the thing has Zeus embedded in it.
@SD –
The drive around stuff was before they realized that android users could do it for them much better than rolling around their little cars… which are being redone to be much less noticeable, btw. This caused no small amount of friction between verizon and google, largely because verizon hadn’t made much money off the data yet.
BTW, the access point triangulation is still in beta stage. The data is being gathered very quickly by using cell tower fixes, even if this is somewhat behind the scenes.
…and you knew that Google is in the process of doing UAV evaluations, right? Google was founded by a couple of bright guys, but that wasn’t how they succeeded in becoming the biggest thing since sliced bread. They succeeded because the guys who work behind the door marked “THEY” had some serious money available [pallets of it, evidently], in exchange for a big piece of the action and access to all that raw information.
I’m not a tinfoil hat guy – this stuff is all common sense, and as I said, I’m all for it… I just want it to be common knowledge to everyone not paying attention.
Apple has recently embraced this – you cannot connect to the mother ship in itunes without acknowledging that you explicitly give them the right to track and use your location information. Why does apple make you agree [even though you lose access to the apple world if you decline] by checking a box when google just presumes?
And the google privacy stuff you’re agreeing to? Look closely – that’s just you agreeing to give your data to third parties and apps. Google still gets and keeps everything, regardless of your settings. Oh, it may split into separate tables, but it can be associated with a single query.
@piipi – yes, basically wireless protocol mac addresses. Rename as you like – the info stays the same.
Well, from the smell of it, I’ve spread enough FUD on the garden for one day. :)
Caution: Everything I write is obviously fictional, and any resemblance to actual people, places or activities which are going on as I write this, is pure coincidence.
Of course, the fact that you can comb the rulings and legislation of your own state(s) and the feds/DOJ websites and discover that legislation is already in place to protect these applications from SCOTUS review should be no cause for alarm.
And as they say, only shoplifters turn their heads up to look for the cameras.
“Oh WOW! You’ve noticed my updates about my CAT aren’t encrypted! You’re so CLEVER! Clearly now we should all waste processor cycles (and therefore battery life) and export regulator’s time and debugging time (ever tried to debug a protocol that uses SSL? No? It isn’t fun.) and encrypt it all! Whew. Close one there! Thanks for pointing out our collective stupidity in not encrypting all this crap.”
The point is more that people shouldn’t by any means think stuff like Facebook is secure, and should run a mile from using it as their email.
kenny mayne
“And the google privacy stuff you’re agreeing to? Look closely – that’s just you agreeing to give your data to third parties and apps. Google still gets and keeps everything, regardless of your settings. ”
It doesnt and they dont, actualy.
Google makes an absolute killing from associative adverts, but they dont sale any data to third partys, they dont have too. They simply use it themselves.
(or, rather, their algorithms do).
“I’m not a tinfoil hat guy ”
Yes you are.
Being worried about your privacy is fine. Thinking a secret society is really behind googles success isn’t. The smart guys made a smart system and a clean website, it delivered the goods better then everyone else, and thats why it was so used.
With large numbers of user’s advertising can give you a lot of money.
Theres no secret “they”.
Hell, if you actualy look at the structure of google they still run themselves far differently to most big companys, and are rather rare to still have mostly technical coders as their highest ranking staff.
I fixed up a working version for linux here
http://deauththis.com/forum/index.php?action=downloads;sa=view;down=5
Just be sure to run it in firefox earlier than 4.0 and start up ettercap with arp poisoning and your in business
Hi guys i am fairly new to this so please go easy on me..I am using (Mac O S X 10.6.8)Installed firefox&firesheep,unable to capture anything?With Winpcap being used for windows what is the alternative for mac users?Any help/advice would be appreciated..