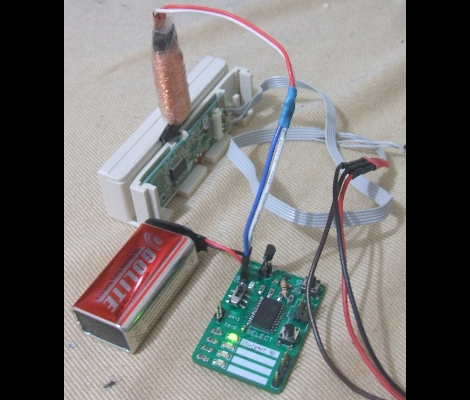
[Craig’s] magnetic card spoofer is both simple and brilliant. There are two parts to spoofing these cards and he took care of both of them. The first part is getting the actual card data. He designed the spoofer board with a header that connects to a card reader for doing this. The second part is the spoofing itself, which is done with an electromagnet. As with past spoofers, he wrapped a shim with enamel-coated magnet wire. An old knife blade was picked for its thickness and ferromagnetism. This magnet is driven by an ATtiny2313 which stores the data, and is protected by a transistor driving the coil. There were a few design flaws in his board, but [Craig] was able to get the same track data out of the spoof as the original card despite the LED being used as a protection diode and an ‘aftermarket’ resistor on the transistor base.















Now this would be interesting to see as a business card…
a business card to hand to daniel ocean?
Little John Connor had one of those years ago :)
The thing john connor had brute forced CCN+PIN on the mag-bank reading slot, which wasn’t ever possible cause their was no way to control authentication cycling from the slot and it has always been custom protocols over leased lines that controlled the firmware.
Every bank in the world has been using a MagnePrint authentication protocol for decades now which is why this hardware isn’t a problem.
This is at least the second mag card spoofer I’ve seen that uses a “shim” wrapped in transformer wire. I STILL don’t see how this could spoof the multiple tracks of data on a mag strip.