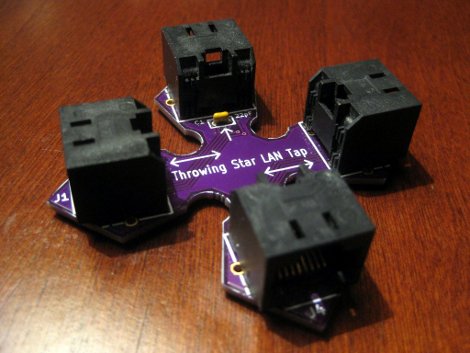
[Michael Ossmann] came up with a nifty little device that arranges RJ45 plugs into a plus shape for the intent of sniffing Ethernet packets, and named it the “Throwing Star LAN Tap”. While the original design worked fine it does suffer some limitations such as being limited to 10/100 base networks, and one way only. This new version of the “Throwing Star LAN Tap” fixes those and adds some much needed convenience.
Gone are the male plugs, which requires couplers and are prone to break, and fiddly splices in favor of a throwing star shaped pcb, and female sockets. 1000 base networks are supported, but due to the workings of 1000 base and wanting to keep the device passive, capacitors are added to filter out the signal and force the network to drop down to 100 base. Sure, it may be an ugly hack, but it’s an ugly hack that fits in your pocket.















Born is the age of the Hacker-Ninjas.
it seams like a board design that would brake easily expecally with cables on all sides but i love the idea XD
odd, but not entirely incorrect that you identified this device as using RJ48, usaully RJ48 usses STP, and is for T1’s and the like, not what the device is used for, should be RJ45, no?
@Bergo
It’s easier to skip the whole RJ-whatever mess and just describe them as 8P8C modular sockets, since that’s what they physically are.
Registered Jack standards are wiring standards.
an ugly hack that breaks in your pocket. now post a video of you effectively utilizing this throwing star for anything. my hack would be using it as a coaster for some Maruchan Instant Lunch, which i microwaved, with blatant disregard for the instructions on its packaging.
Actually, i thought sniffing was a wireless thing. like, if i be sniffing glue, little ‘packets’ of glue are coming through the air, up my nose, and killing brain cells. is this some special technique for making wired things wireless? should i arrange 4 identical, non-wireless household telephones on a ninja star board in such a configurations, have i just created a wireless wiretap?? if so, then you, sir, are a genius!
@Jeditalian
If you are on a switch style router, you are not able to see other people’s packets like you are with a unsecure wifi access point. The switch knows what packets go where, so it knows not to send certain packets to you, and therefore you would not see any of the other computers traffic. A common way around this is ARP poisoning (in which you trick other machines to think you’re the router), but that’s very “loud” on the network. This allows for a passive tap so you can see exactly what is going through that line without creating a ton of ARP traffic that will be very noticeable on the digital side.
Personally, I think it’s a cool idea. It has limited applications, but is still very neat. I saw a video with Ossmann on Hak5, and his Bluetooth sniffer is really awesome idea as well.
Bergo is correct, it should be 45, i really don’t know where 48 came from =)
Ok, so you put this in between a machine and a switch… and unless you can make the switch fail over into a hub-like mode you would only see the traffic going between the machine and the switch.. so you could have just used tcpdump, wireshark etc on the machine itself?
Oh, and real switches have monitor/mirror port functionality..
“Despite its limitations, the device has come in handy countless times over the years.”
I really don’t see how. You could have got an old fast ethernet hub from a junk shop, or just two nics on your monitoring machine and bridging (USB nics are crazy cheap, and setting up a bridge is like 3 commands max for any sensible OS).
This is my tap, I made it to test some propagation delays at work.
http://saimhe.avita.lt/hw/passive_tap/passive-tap-4.jpg
A bit sturdier :)
Not for GbE, though. That solution about downgrading to 100BASE-TX is a true hack, I like it.
and why the forth connector?
Should have made it a 3-pointed shuriken.
I still remember the days when I could bring down the entire University library network by just connecting a cross-over cable between two network sockets (belonging to a crappy switch).
Using ettercap to MITM other people there and replace the images and text with NSFW stuff was fun too!
The best of all was when we spoofed their access points with our fake WPA-PEAP radius authenticator. Believe it or not, the university didn’t even provide us the CA certificate and obviously windows didn’t care to ask for one either! Ahhh … good times!
@cantido:
Maybe you don’t have access to the target machine, or don’t want to install invasive software on it?
A hub is a far larger/heavier/less convenient/non-passive solution. I’m not sure why you think it’s better. Also difficult to just go to the shop and pick one up these days. This you can just toss in your toolbag and you have it when you need it.
Setting up a virtual switch is just a pain in the ass in comparison.
My throwing star lan adapter has come in very handy. As far as all of the comments about sniffing glue and wireless, well… don’t know what to say to that. perhaps, if one was really smart, they’d put this inbetween an AP and the upstream switch… then you get to sniff all of the traffic without the WiFi protocol overhead…
I’m going to be layering mine with acrylic shortly, and hopefully will post some pictures.