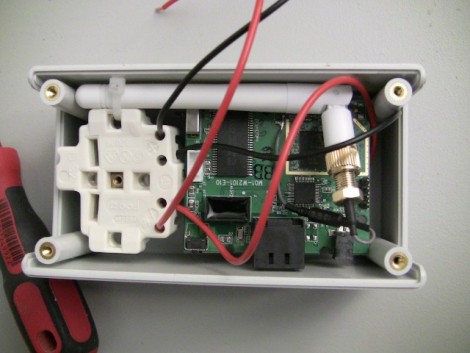
[Mike] sent in a tip about Newstweek, and we’re turning to our readers to tell us if this is real or if we’re being trolled. The link he sent us points to a well-written news-ish article about a device that plugs into the wall near an open WiFi hotspot and performs something of a man-in-the-middle attack on devices connected to the access point. The article describes the device above as it observes, then spoofs the ARP table of the wireless network in order to inject fake news stories in pages you are reading. Apparently once it boots, the small box phones home for commands from its maker over a TOR connection.
The box reminds us of the Sheevaplug so it’s not the hardware that makes us question the possibility of the device. But look at the Linux terminal screen readout. It shows a prompt with the word ‘newstweek’ in it. That’s the address of the site the article is hosted on, giving us a strong sense of being trolled.
What do you think, real or fake? Let us know (and why you think that) in the comments.















GUYS!
GUYS!
GUYS!!!!!
Has anyone simply tried going to http://newstweek.com and observing that every story they have is fake?
Newstweek was created by two artists trying to prove you cant trust everything you read online and so was the mysterious plug-in module, apparently.
http://www.imperica.com/features/newstweek
so where is the power supply in all this? I seriously doubt mains power is going straight to that board. looks like someone just crammed an old wireless AP PCB in a new enclosure and added some fake wires.
If the article submitter words the OP as ‘the earth might be flat’ it’s inevitable you’d have people in here blindly arguing about it. This is almost as bad as the misunderstood ad campaign for the free NXP dev boards, which caused countless people to crusade the comments with evangelical boycotts and nonsense.
internet: serious business.
I think that most of us here know of Darren Kitchen’s efforts to make this kind attack more well known.
He has been doing this for a while but with a Fan router (custom firmware)stuffed inside a novelty pineapple cup. Hell he even made a ‘physical’ version disguised as a teddy bear that could be used in an office setting possibly to fool a receptionist or secretary.
this reminds me of a program called air-pwn, which used 2 wifi cards, and then injected a false http reply for certain requests
the example youtube video showed it as a defcon, replacing all images with goatse and other images
I think one of these was used at a local coffee shop near me. I could tell because the old Gizmodo layout was being used on the american website.
@Joe Catts and others,
You asked “As far as making changes to a page, what good is this even if it were true?”
The value of injecting into peoples’ pages at a wi-fi hot spot is that it can be used for a form of malicious attack called “cache injection”. What the attacker does is to create a proxy that tacks on a bit of javascript at the bottom of every page that it delivers AND it sets the cache-control max-age to something like a million seconds on each infected page, so the browser is happy storing it for years. Maybe some of the pages it infects are sites they’ll never return to, but some may be the victim’s home page or another commonly used script such as google analytics.
The idea is that the victim will carry his or her PC from the hotspot back inside their firewall, power up their PC, and return to one of the pages they visited at the hot spot, such as their home page or google, but which is now retrieved from cache complete with infection. At this point the browser has the full authority of the logged-in user, and the javascript begins its really evil work, uploading secret documents from inside the corporate network, or doing whatever else it’s designed to do.
http://www.hak5.org/store/wifi-pineapple-version-2
dude, its real. You can buy one here, or make one yourself.
Real or not, if I found one of these ‘news-spoof’ boxes, I’d just take it home with me.