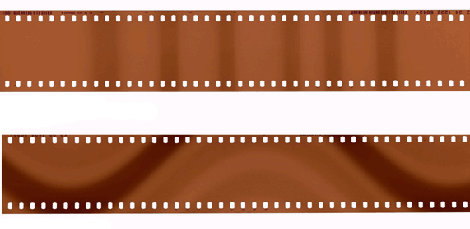
With all the talk of radiation in the media today [freddysam] posted a quick Instructable about using standard camera film as a radiation dosimeter. Film is sensitive to other forms of radiation other than visible light, and high speed films are even more susceptible due to their chemistry, which has caused all sorts of headaches to travelers before most people went digital. This uses that headache as a simple way to see if you have been exposed to abnormal amounts of radiation in a 3 step process.
- Get some film. Yes they still sell it, it can still be found just about anywhere.
- In a dark room unroll a little out of the metal can and put it back in its black plastic container.
- Develop it if you think you have been exposed.
The idea is to let a few frames of film to be exposed to normal background radiation and develop it so you have something to compare with in the future, then you can unroll a bit more, and if you think your going into a hot area you can develop that newly exposed film to see roughly how much more radiation there was, maybe helping you sleep better at night.