It’s time to do your best impression of [Comic Book Guy] as you make your case for trash or triumph in big screen hacking scenes. We watch a lot of movies, and it’s hard not to groan when the filmmakers cut corners by doing zero research into what using a computer actually looks like. But then once in a great while you have a team that does its due diligence and puts up a scene that makes sense to those of us in the know. So we’re wondering, what movies do you think have the best hacking scenes, and which ones are the worst offenders? Leave your opinion on the topic in the comments section.
We realize that you can come up with tons of poorly done ones, what we would really like to hear about is who did it right. We’ll get you started with a couple of examples. The image on the upper left is a scene from Tron: Legacy which we think did a fantastic job of portraying actual computer usage. You can read more about the huge amount of work that went into it in this article (via Reddit).
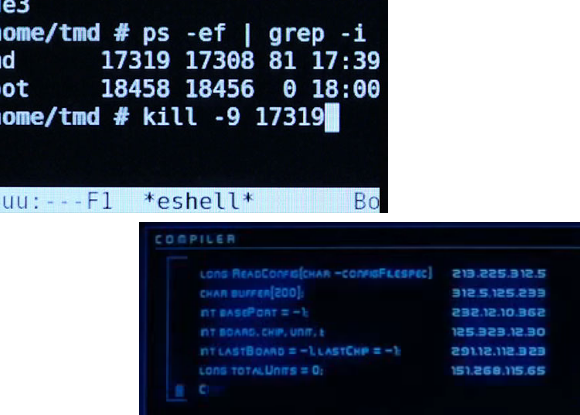
In the lower right is one of the most shady movies scenes that comes to mind. [Hugh Jackman] is compelled to do some ‘hacking’ by [John Travolta] in the movie Swordfish. The caption at the top of the screen is “COMPILER”, and who the heck knows what the rest of that is supposed to be?
On the hardware hacking side, it gets a little more difficult, we would LOVE some examples of hardware hacks or mods done right.















not Hackers.
Yeah, there are so many things wrong with that movie:
1) You can’t just dial a number and talk to the internet.
2) The phone he was using had wires connecting it to stuff, which is just ridiculous.
3) It’s pronounced “new-kya-lur”.
3 – “new-clear”
Regarding 3:
http://www.merriam-webster.com/dictionary/nuclear
http://en.wikipedia.org/wiki/Nucular
No, it’s pronounced ‘Nu-clear’ silly. The ‘S’ is silent.
I didn’t actually finish that movie because it was so bad. I do remember some semi realistic phreaking though. I know in one scene a guy gets a free payphone call using pre-recorded tones. This was possible at one time. Can’t remember anything else of note though.
It’s called redboxing. $20 and a trip to (or a minitape recorder and some luck.) RadioShack (pre-suck) and you’d have free payphone calls for life. Or until the phone companies caught on and stopped it. Then the boxers figured out that you could bypass the new security with an unbent paperclip (in true MacGyver fashion). Phone companies caught on again and invented cell phones so there wouldn’t be any more need for payphones. You have me to thank for your iPhones and Androids.
I thought it was phreaking.
phreaking was the general term for phone hacking while redboxing was one of the techniques.
I do love bent paperclips.
Mel Brooks claims to have invented the first cell phone (in “Get Smart”).
Never saw Swordfish, but the code example looks a bit like APL or even HPL
Sure, if you can assign IP addresses outside of a legitimate IPv4 range to a 200-char buffer and actually accomplish something. Still, the worst I have seen is a CSI episode where they actually had too many DIGITS in the IP address octets(which was what they used to track down and find a guy, somehow).
those aren’t even ips. some of the values are > 255.
Which is why it’s wrong, and why I said “outside of a legitimate IPv4 range”.
Yeah I watched NCIS the other day, and they used a 192.168.x.x address to track down the enemy!
Atleast it was a valid IP ;)
HE’S IN THE BUILDING WITH US!
I’m pretty sure they would do this for the same reason you don’t use real telephone numbers.
That’s probably like using 555 phones numbers so the audience doesn’t call someone just because they saw it on tv
It’s better than using 127.x.x.x
192.168.x.x is the 555-1212 of the movie internet
http://xkcd.com/742/
Probably done for the same reason that all phone numbers use 555
I thought Invalid IP addresses were merely the modern day equivalent of 555-XXXX phone numbers. Producers don’t want to be sued by someone because their IP address was displayed in a movie which resulted in their connection being flooded/hacked. Same with web addresses with invalid (at the time) TLDs. Although now if you pay enough money you could actually create that invalid TLD. Has ICANN designated a top-level domain which the media could use for such a purpose? http://www.target.computer.555 perhaps? :)
It looks like someone took some variable declarations and put IP addresses next to them. That’s what hollywood does, they pick random things and blend it up hoping the result is plausible but failing most of the time.
IP address? Ping 293.12.112.393 and tell me who’s at the other end :-)
I was about to point that one… McGee trying to track down an IP like 293.xxx.xxx.xxx… Come on dudes! At least 192.xxx.xxx.xxx may be valid addresses (even if it’s not an Internet address).
Not aboult films but about a reason why they use false IPs or phone numbers : a french music band named Tryo included a mobile phone number in one of their song’s lyrics, and they didn’t check if the phone number was assigned or not. It turned out it WAS assigned to a plumber. The guy was harassed by people calling him ^^
Sources (in French) : http://next.liberation.fr/musique/2012/08/28/harcele-au-telephone-a-cause-de-tryo_842351
Don’t we all forgive Hackers, though? The depiction of “hacking” is so bad it’s good, and the rest of the movie is so much fun that it hardly matters.
That and it has one realistic hacking scene. The one where the one guy stares at a computer for hours, trying to work out what a virus does, while the other two eat pizza and lay around.
Lets not forget the scenes where you can see Angelina’s tits. The dream sequence where she’s in the tight leathers and hacking competition where the camera rolls over her while shes working in the black shirt (that if you look closely at is see through and she’s not wearing a bra).
i learn about trangulation i am life firewall with old laptop where is the laptop agent smith dosent know
Jurassic Park, the words don’t even match up to what he is typing.
http://youtu.be/RfiQYRn7fBg
dammit, i was about to post this, lol
There is also the scene where Dennis talks to the guy in the docks… and it’s a video file being played back.
“This is a UNIX system. I know this!”
*plays QuickTime movie*
That was actually FSN. It’s a real (yes, even in ’93) 3D filesystem viewer for IRIX systems.
Watch the clip again. It may have been a video OF that system, but you can clearly see the playhead moving along in the QuickTime player.
Dvorak? Colemak?
but i liked hackers, lol
I’m gonna be hated for this, but I love the way the hacking is done in “The social Network”. Every detail seems right to me. At a certain point you see “Mark” writing FaceMash and you see him working on a KDE desktop and hear him talking about wget, grep, perl webscraper…
Also the part in the basement where they are “beerhacking” a server and first one to get in gets a job at FB is pretty darn close to how a real security would be set up..
But that’s just my 2 cents..
Thats right
I’ll second this. I’m pretty sure I saw a bash script with wget in there (or they mentioned it), the hacking description was boring as hell, and pretty much right on the money.
i laughed out loud when he was setting up that face comparison site and got to the one server that actually had some kind of security measures and said “uhhh…I’ll come back to that one.”
Yeah, “The Social Network” was indeed great in this aspect. Older versions of KDE, no Compiz, No MacBook but greyish Dell and Vaio… One of my favorite scene in the movie is when Mark logs out of a thin client in university library. He apparently force-closed the session with keystrokes, Ctrl-Alt-Bksp-Bksp or something, but that sounded so like the real thing. The exact, natural sound and motion anyone would make… That struck me so much better than seeing a random tough guy reloading scavenged handgun in super-smooth motion :)
Yeah. Actually, the entire text of that scene was taken from Mark’s own blog posts. Also, mark uses KDE during the film. The only thing I protest is that mark wanted an Apache and SQL “box”. Knowing how money was tight(er), why he get an nginx or lighttpd box?
The girl with the dragon tattoo had a reasonable hacking scene. Not sure if that was the 2009 or 2011 version.
In the second (or third?) Matrix movie Trinity uses a real exploit.
http://www.youtube.com/watch?v=ojFFS_T3UQk
http://www.theregister.co.uk/2003/05/16/matrix_sequel_has_hacker_cred/
Yeah, that was great
RTF Control
More like ROTFL control
I’m gonna be hated for this, but I love the way the hacking is done in “The social Network”. Every detail seems right to me. At a certain point you see “Mark” writing FaceMash and you see him working on a KDE desktop and hear him talking about wget, grep, perl webscraper…
Also the part in the basement where they are “beerhacking” a server and first one to get in gets a job at FB is pretty darn close to how a real security would be set up..
But that’s just my 2 cents..
you are not the only one who liked that scene woutervddn. I ove the movie cause of those two scenes
Not the virus creation scene from swordfish:
http://www.youtube.com/watch?v=rjGbvpr_dB8
Swordfish sucked pretty much all around. I would even go as far as to say it was Travolting.
Hahaha, brilliant.
Even the part that shows Halle Berry’s boobs?
Yeah, because setting aside for a second the fact that a pair of boobs shown for 2.5 seconds do not make for a riveting film, the boobs in question weren’t even that great. Rumor is that she was paid several million dollars for that scene alone; they could have spent that on more 3d virus effects instead of that scene and the movie would still be improved.
So the answer to your question is: yes, all parts of that movie sucked.
not to mention that the scene was the very definition of gratuitous; it had no bearing on the plot, or even the characters in it, IIRC she drops her book and no one in the scene even acknowledges it; other than the audience missed a few lines of dialog.
the opening scene of swordfish was great, too bad it had to be wasted on such a shitty film,
IIRC, she said in an interview she was paid 1/2 million to do that scene.
Which in today’s dollars is probably equal to “several million” B^)
Full Disclosure: I haven’t seen the scene, nor have I seen anything except a trailer of the movie.
This is actually the scene I use to explain what viruses are to non-techies. It represents a core product (of sorts) with layers of products / activities / services that make the virus have legs and run. As we all know…sometimes the hack is easy, but just getting it to run in the right place at the right time on the right environment is a challenge all on its own.
It makes me think of script kiddies though…
Yea the hacking and gui sucked! However the frustration of the thing just not compiling while it should (obviously not because you made an error) and the exitement when the stupit trivial error had been found are things I recognize.
When I watch these movies I dial my brains to level -2 and look at the pretty pictures.
No wait, maybe Wolverine designed his own GUI specialized for his hacking needs? He so many monitors, and it’s just a little one that has the cute polyhydra, in some of the shots you see the other screens have data strings, and really that trippy stuff in the beginning is just camerawork, the computer is not displaying any sort of fly-through, it’s cinematic technique to activate the animation for a scene which would otherwise not seem quite as interesting.
WHY WERE THE MONITORS LAID OUT LIKE THAT?????
Not entirely accurate, but I loved the way the reeves did it in the first matrix movie. Weird optical disc/memory card hybrids, terminals with only one blinking line etc. Thats how real hackers work- the terminal console is cleaned after every line and runs fullscreen.
I believe you’re talking about MiniDiscs.
matrix, trinity hacking http://nmap.org/movies/matrix/trinity-nmapscreen-hd-crop-1200×728.jpg
I think it is more relevant that she used sshnuke after nmap.
If you look closely at the edit window for sshnuke, it’s assembly code… not that you cannot write an exploit in assembly, but it’s not that realistic.
I liked Seth Green’s “phreaker” scene in The Italian Job.
For hardware hacking, it’s kinda hard to beat the original A-Team. Many of their designs would actually work in real life.
Everything in Skyfall was “Hackers”-grade terrible. Can’t the writers even ask the IT guy around the corner “Hey man, could you give this a quick look and tell us if it’s total bullshit, maybe suggest some fixes? Thanks!”
I suspect they DO ask the tech people, who then come up with the craziest goddamn thing they can think of just for shits and giggles.
The “tech” on Skyfall sucked hard enough to pull a golf ball through a hose pipe!
It’s a TV series, not a movie, but it is so bad it has to be mentioned: NCIS. Really everything computer related on there is painfully cringe-worthy wrong.
[youtube https://www.youtube.com/watch?v=u8qgehH3kEQ&w=560&h=315%5D
Well that embedded like crap… regardless, here you go!
Wow that is the worst I’ve ever seen!
Good thing he unplugged the monitor, that could have been bad.
There’s a scene in NCIS somewhere where they shoot the monitor to stop the computer working. Thoroughly awful, I’ll grant you.
However, the “2 idiots, one keyboard” scene simply must be forgiven because it has Abbie in it and she’s amazing.
At least the actual solution made sense.
just pull the plug …
Two people using the same but different halves of a keyboard to prevent a hacker from getting past their firewalls in real time. OMFG NO.
Pair programming at its best!
Red Dwarf CSI piss-take – awesome
http://www.youtube.com/watch?v=JMIHNiR3CP8
I thought they were referencing blade runner with that episode. Guess it can apply to a few shows/films though…
Although NCIS’s writers do that on purpose – they compete with writers on a few other shows to get the most bogus IT dialogue/action on screen possible.
+1 The Matrix for Trinity hacking for best
+1 Hackers for everything wrong with Hollywood and technical details
Every single movie with “A C C E S S D E N I E D” in large blinking red letters when a password is incorrectly entered. I kinda wish ssh would do this every time I mistype mine.
I turned on the “offensive” use flag in Gentoo and now when I screw up my passwords on the command line it gives me random quips. Some of them are dumb, some of them are insults and others are just plain funny.
Wargames: War dialing.
http://www.youtube.com/watch?v=AByemfK_qD4
^= this.
WarGames is the quintessential hackers movie. Why? Because it is the ONLY movie to get the personalities correct. The kid that just wants to have harmless fun, the oppressive government response… and the two IT guys that Lightman talks to… MR. POTATO HEAD!!! Seriously, it’s the only movie I would ever call authentic. Nevermind that it is overly-optimistic about what AI can do, but it made an awful lot of people imagine possibilities and that’s what good story-telling is supposed to do.
The german movie 23 (http://en.wikipedia.org/wiki/23_%28film%29) is pretty nice as well and also revolves much around one hackers spirit/personality.
B.t.w. did anyone also like sneakers? =)
You do know that was a thing right? It is some random made up program and some audio to visually describe how it works. Toneloc was always the way to go….the program not the rapper.
One of the worst things I’ve ever seen in a movie was in X-Men Origins Wolverine. The movie was horrible to begin with, but at the end when Deadpool is all of a sudden a Unix controlled robot, he gets issues the command “./decapitate/”. I literally rolled on the floor and started crying I was laughing so hard.
Everyone knows it’s
/sbin/decapitate
or maybe
xman –help | head | cut –characters=$DEADPOOL
Now when you mentioned it. This is some kind of social hacking. To get into some ones head. Kind of.
https://www.youtube.com/watch?v=zz-tkhBJJY8
Click on the transcript button to understand damn anything.
I have two problems with the Tron: Legacy scene.
1) The terminal running top shows that Xorg is running. Xorg didn’t exist in the 1980s or early 1990s, which is when that machine would have been set up.
2) It’s running Xorg, which means THAT WINDOWMANAGER EXISTS AND I WANT IT.
second that, I saw an article a while ago about how they made it. Anyone has a link to it
http://jtnimoy.net/?q=178
Incase anyone wants to read it, pretty intresting.
Yeah, any info?
Actually that scene was from the opening scene when the Board of Director’s meeting is crashed by Sam as he stole their latest OS and made it freely available for anyone to download. An ENCOM employee then uses the kill command to stop a video of Sam’s dog playing on the main screen, which I believe was part of a feed for the press conference.
Ah true. I refer to the old table system in the lab underneath Flynn’s.
He means this one
http://i.imgur.com/FoB38.jpg
Bingo.
Even funnier – is it SuperSPARC I/II (sun4m), or is it i386!?
They had to do that, as well as call it “SolarOS” or risk the litigious wrath of whOracle.
I’ve got a couple sun4m systems here for kicks :D awesome movie!
From top: “up 8 days(…)” …wait, wasn’t the machine on for years?
Some older unixen have a limited number of bits in this counter, it just flips after a year or so. If I remember correct. It was definitely said about old Linux.
Iron Man 2 has one of the worst. They don’t show the screen, but Ivan Vanko hacks a computer in 2 seconds by jamming the keyboard.
Apparently in Russia physicists know electrical engineer, advanced control theory, AND hacking. (insert Yakov joke here)
I disagree on that. The scene was meant to show what an asshat Hammer is, more than what a genius Vanko is. I kind of assumed he did something stupidly simple that Hammer did’t protect against like alt-F4 out of the security program or something.
I’ve seen a cat bring down a whole POS (point of sale, not piece of ….) network by simply jumping on the keyboard. No idea how it did it.
http://youtu.be/BjD54lKM8jU
Cat vs computer. Yep I’ve had that problem. Finally fixed a clients PC, after hours of frustration. Had left a windows7 boot disk in the machine (BAD move) got up to get some air. Came back to cat on keyboard and newly installed copy of win7 WTF! Glad I backup BEFORE I fix. Meow!
Seriously? It took you 45 minutes to get some air? 30 if it’s an SSD machine. Not to mention, you backup what? No technician with any amount of skill or clientele has time to backup every machine they work on. Not to mention the legal implications of copying every customers data and the amount of space required. Even with compression you’d chew up a 1/2TB drive in no time.
I hope you realize not every computer belongs to a person. Try working in the automation field some time. I have to backup every computer I work on. Yes I do have TB worth of data but that’s cheap compared to loosing data and causing massive downtime for multimillion dollar automated systems. People tend to get mad when you have to spend hours recalibrating equipment because someone loaded the wrong config file into a machine.
I’ve been on the wrong end of the ” legal implications” of NOT backing up before working on a computer. Losing someone’s wedding pictures does not equal a good day at the office.
I create a backup on a cheap external drive, turn the drive over to the customer when I’m done, and charge for the drive.
Really? Then the 6TB backup array sitting on the bench across from me must be my imagination.
We back up EVERY drive that comes in before we do anything else unless the customer specifically declined the backup and signed the extra waiver.
Every backup is encrypted with the private key of the technician who is working on the system, and all backups are wiped after the system is returned unless the customer pays for archival. ( at which point a separate backup is made after the system is repaired ) The entire backup is automated, and the backups are tested immediately.
We literally just plug set the system on the shelf, plug it in, and trigger a PXE boot from a usb key.
( instead of it sitting idle on the “in” shelf for a few hours waiting to hit a bench )
Total additional labor: 2 minutes.
The expense of setting up and maintaining the backup system is less than the cost of having the lawyer draft a response letter twice a year, and the archival services actually came out to a profit. That’s not even accounting for the expense of a lost customer when a tech makes a mistake.
Point-of-sale, Piece-of-s**t; both terms define the same thing.
>Apparently in Russia physicists know electrical engineer, advanced control theory, AND hacking.
Well, they actually might know it. Russian (post-Soviet) educational system is a bit overboard on stuff. I am nuclear engineer myself, and they did taught me programming and electrical engineering. Well, it was basic but more than enough to get you started. And a lot of us did get into it.
That’s what called here (Poland) “a good educational system”. Engineer should have basics of most of the fields and ability to learn new easily – you newer know what your next task will require.
From my side of the planet, some physicists do get into hacking and electrical engineering.
I am a Physics major in europe and I agree with aklan_alray. (also, got 3 projects featured on HaD :D)
Is this sort of thing even possible
> Apparently in Russia physicists know electrical engineer, advanced control theory,
> AND hacking. (insert Yakov joke here)
Yes, but everyone knows people in colder climates tend to hack more than
people in warmer climates. :)
the 3D “UNIX” Scene from Jurrasic Park: “This is UNIX, I know this!”
http://www.siliconbunny.com/fsn-the-irix-3d-file-system-tool-from-jurassic-park/
@Anne Nonymous, I agree that Jurassic Park is definitely not a realistic portrayal of hacking, but the 3D scene was actually a real file system explorer called FSN (http://en.wikipedia.org/wiki/Fsn). Now what they were doing using IRIX to run their industrial automation is anyone’s guess, I’m sure it had something to do with the Thinking Machine CM-5 blinking away in the background.
We tried to replicate this at our office on the big SGI box.
Got fsn built, but the machine was a headless compute box, had no graphics card, and no modern non-SGI Xserver supports remote DGL.
Why would you try to use a 3d rendered filesystem on a headless machine?
We were exporting the display back to a local X server.
Jurassic Park:
A custom system with millions of lines of code
controlling a multimillion dollar theme park can be operated by a 13 year
old who has seen a Unix system before. Seeing an operating system means you
know how to run any application on that system, even custom apps.
Note: What OS was it really running?
(1) “These are super computers”. A CrayOS?
(2) “Quicktime movie, Apple logo, trash can.” MacOS?
(3) “Reboot. System ready. C:\” DOS?
(4) “Hey, this is Unix. I know this” Unix?
The computers in Jurassic Park were Cray supercomputers running the MacOS as a graphical shell of DOS all layered on top of a Unix base.
These people patched fossilized dino DNA with that of a frog. Clearly they like to make things difficult for themselves.
1) In the book they were Cray X-MP. In the movie that is a Thinking Machines CM-5 blinking in the background. In reality they were empty frames with just the blinking lights, according to Google.
2) The Macs were merely Xservers into the frontend processor in the same way we use our Windows PCs today merely as web clients or terminals into much larger systems. Although someone else has posted that the Macs were just playing quicktime videos of what we were supposed to think were terminal sessions.
3) Back in the day, I used to do silly things like set my OpenVMS and DEC UNIX/OSF/Tru64 shell prompts to C:\> . People watching over my shoulder would be like “WTH?!?!” and I’d be all “LOL”.
4) Yeah, I cringe at that point as well.
Actually, the supercomputer in Jurassic Park was a Thinking Machines CM 5.
I nominate Wargames, definitely one of the most inaccurate portrayals of computer hacking ever.
How old are you? Because war dialing, unsecured modem terminal ports, and phreaking as portrayed in WarGames was almost exactly what the hacking scene was like in the early ’80s. Hell, this movie is where the name “war dialer” came from.
They got the line short payphone trick right such that by the early ’90s it was impossible to find a payphone with a mouthpiece that wasn’t glued in. Of course you could always drive a sharpened nail through the diaphragm…
The moment they published the BASIC program they used to simulate key strokes was the moment I was put off of that movie forever. Not to mention the fact that the AI was totally unrealistic for the time period.
As for my age, I am old enough to have had my first computing experience with a then-current Altair 8800. I saw Wargames in the theater.
“AI totally unrealistic for the time period” … It sounds like you actually expected the movie to be about hacking into a speak-and-spell. You apparently haven’t figured out that Wargames was not intended to be a documentary.
I nominate your nomination for the worst nomination in this thread.
What, were you expecting WOPR to be Eliza, and for all the actors to accurately hit 80WPM?
I was expecting a modicum of realism given 1983 technology limitations (both civilian and military).
Apparently I can only nominate movies that you people agree with?
Yes, because all secret goverment computers are at or below public levels of technology. Currently NSA doesn’t have anything you couldn’t buy given infinite resources. Sure.
The war dialing was exactly as we did it then. The payphone hack completely accurate. I was even still able to do a similar hack payphone hack until the mid 90s with a paperclip and the coinbox keyslot.
The conversations with Joshua were of course unrealistic but then again this was supposed to be an advanced military AI created by a world genius…. so suspension of disbelief is required.
Hacking in movies/TV is almost always asinine. It is much easier for screenwriters to try to write the emotions (or imagined emotions) of hacking than to write the mechanics of something they don’t understand. Thus hacking scenes often devolve into a fancy screensaver, or “cool” fast moving hex code scroll (sometimes even sideways).
The funny thing is that livecoding interfaces have started to copy some of the cheesy “hacking” text effects from movies, so perhaps some day people really will just hack by squinting intensely at pretty pictures on a 10 foot screen in front of them and spouting cliched lines like “almost there”, “I’m in” and “got you”.
Okay, as a screenwriter who happens to have a MS in Network Security, I need to come to all those screenwriters’ defense:
The script of a movie is mainly just the dialog, with some very rough outlines of what’s going on. A hacker scene in the script looks something like this:
INT. Dark Basement Room
L33T HACKER, is sitting in front of computer typing away furiously. He switches rapidly between windows, until suddenly
HACKER
(excitedly)
I’m in!
There really isn’t much room beyond that in the script. It’s mostly what people are saying. What shows up on the screens is the graphic designer’s job, and ultimately the director’s. Writers really don’t have much to say unless someone directly talks about how they hacked (not very likely, as it is boring to non-techies). There can be a very realistic script, but it fall very flat in the final product.
I would recommend re-watching Hackers without watching what they’re doing. It’s surprisingly closer to accurate, at least in the first part of the movie before all that DaVinci nonsense.
Now really. I’ll recommend you to watch The Matrix Revisited about the level of screen writing of Wachowski (still then) brothers.
The Matrix Revisited was also written AND directed by the Wachowski starship. Having control over the entire process, they knew/did their research when writing the script, and were in the fairly uncommon position to be able to enforce that level of minute detail in the final product.
Unfortunately, that’s rare that a writer has that level of control over the process. Most of the time, a writer writes a script on spec (prior to being paid), and tries to option it off to the studios (sell it). A lot of times, once the script is sold, the writer doesn’t have much say in what the director does, often times they’re booted out and a second writer is hired to tweak things to the director’s liking and the first writer has no part in the process until they see their name on the big screen.
How many movie executives does it take to change a lightbulb?
Movie executive: “Does it *have* to be a light bulb?”
(Heard John Cleese tell it.)
I have to agree with you on hackers if you ignore ALL of the 3D graphics, and focus solely on the dialogue. For it’s day the dialogue is pretty accurate.
keycheck -o “keychecks off”, safety -o “he’s turning the safety systems off, he doesn’t want anyone to see what he’s about to do”
I’ll just leave this here: http://nmap.org/movies/
You’re in. Order it to disarm the missiles.
Burn notice. It is about 40 % how to hack together spy equipment. Most is pretty odvious, But much of their hardware is placed in the relm of plausable,
true, burn notice is plausible in it’s hardware hacks, about 90% of the time. nice show, can’t wait for the next season this summer!
And then Fiona makes some C4 from the household chemicals under the sink -_-;
In movieland, a 6502 provides enough processing power to run a Terminator.
An Atari Portfolio bruteforces ATM and security card numbers!
Considering you can break APCO P25 encryption with an IM-Me toy it’s plausible.
I thought the IM-Me just jammed the encrypted traffic so the victim has to switch to unencrypted comms(?)
Yeah that’s what it does. But it just goes to show that an inexpensive toy can be used to render your encryption useless.
you could always get lucky.
Ah, but an 8086 runs the bug picking robots in the beginning of Runaway!
not hacking, but the terminator uses real assembler code whenever they show his view.
The designers left a gratuitous easter egg. Hey wouldn’t it be fun to have a virtual 6502 looking like its controlling the show on the videolog? Awesome, but only do it if some fool sets the clock back to the 80’s otherwise the boss would get pissed, LOL
Yeah, but so does Bender even in the year 3000
I know the intent of this article is about hacking the software security systems. But, if you will allow me some latitude…The only real computer hacking scene in movies is the Apollo 13 computer power up hack.
Everyone’s picking on Hackers. I think it’s a great movie, and here’s why – it’s not meant to be serious. The whole thing is a farcical joke about how bad Hollywood is at portraying technology. It was just not done obviously, and the joke was a little ahead of it’s time, so it’s hard to tell if they’re trying to be serious. Watch it again with that in mind. Well, that and Angelina Jolie…
To me, the ‘hacking’ scenes looked a lot like the hacking sequences in Neuromancer. I don’t know which came first, the book or that kind of cinematographical shorthand, but it seems to me that Hollywood was influenced a lot by that book.
The only two good parts of Hackers.
http://free-nude-chicks.com/celebs/AngelinaJolie3/AngelinaJolie_Hackers_02.jpg
For hardware hacking nothing beats the scene in Apollo 13 – “We gotta find a way to make this fit into the hole for this using nothing but that.”
the scene in Apollo 13? I’ll say the real-life version of that event. Just proves the rule that Duct Tape fixes anything…
That and the “rig up a coulomb counter on the power input to the simulator” to figure out a bare-minumum power up sequence.
I agree, that was awesome
The most dumbest is this one: http://www.youtube.com/watch?v=hkDD03yeLnU
^ agreed. Do you even computer?
^This.
Yes!
I totally forgot about that one! I saw that episode when it aired and I cracked up for a good while when I heard it…
“I’ll create a GUI interface using Visual Basic… see if I can track an IP address”.
It’s as if the writers knew that an IP address would be helpful for tracking the killer (and this is the only thing they got right), but they had no idea what that meant and threw some random computer jargon in there to achieve the goal. Sounds like a lot of work to track and IP address!
The movie “Sneakers” irritated me the least; does that count for anything?
Sneakers is awesome! It doesn’t try to be overtly technical with its scenes, but it covers phreaking, social engineering and physical penetration testing. Beyond the silly plot about a magical black box, it’s a solid movie.
Been a while since I saw it, so I could be wrong but I seem to remember Firewall (2006) with Harrison Ford having some impressively accurate portrayals of hacking and network security in general.
Yup, it shows Emacs (xEmacs?) a few times, IIRC.
Firewall bugged me. Apparently they hadn’t created ACL 1 yet, but he does finally create it to stop a single attacker that is coming from three different Asian countries whose IP addresses all fall in privately defined address space 172.16.4.0/24:
https://www.youtube.com/watch?v=D92hau35NyY
And that scene where he puts an analog scanner on a monitor to copy the information scrolling on the screen terminal, Forget the screen light reflection, that still isn’t going to work like you think it will work.
Gotta give them props for using legit looking software though, Wireshark and Cisco IOS.
In this movie there is also a scene were he talks to his son about shielding some onboard
cameras from an RC cars motors to provent rfi.
Harrison Fail2ban
This is probably going to bug you even more. The ip range is invalid. That ip address and subnet mask is for *.*.*.0 not 172.16.4.*
Are you serious???? He hacked a scanner together with an ipod to scan the screen of the computer… This movie made me LMAO when I saw that.
I don’t remember this, now I have to re-watch it.
Sneakers was awesome, its a little dated, but still great. Dan Akroyd, hell yea!
Best: WarGames http://www.imdb.com/title/tt0086567/
Worst: NCIS (Original)… NCIS LA is ok.
The hacking scene in goldeneye looks okay. The terminal screen seems weird to me but it could be an old version of a Unix terminal I have not seen.
What I like in this movie is that he actually disconnects the OS disk drives to make it fail, he doesn’t just punch the screen like it has been seen in so many other movies.
Not strictly a hacking scene, but the best computer/IT scene is probably from Breach (yes, the one about Robert Hanssen).
Robert Hanssen is at the IT department, talking with the guys there, and the jargon is all correct, used correctly, and as far as I can tell, the advice given is actually good advice for the time.
Holy crap, MacGuyver????? Regardless of the audacity of some of his…well….”MacGuyvers”, his name has become somewhat synonymous with hardware hacks. Also, some of it was actually feasible.
The early seasons, yes. But as the series aged (and the mullet grew out) they got lazy. Picking a lock became inserting the Swiss army knife blade into any lock and turning, or taking a bunch of torn fabric and metal bars and in less than 15-minutes have a fully functional hang glider.
“MacGuyverisms” started to become a Deus Ex Machina.
It was pure magic while I was growing up, but going back and watching them as an adult was disillusioning.
Having said that, I still think he’s awesome.
+1
The early seasons were better. There was a lot more science. As the show progressed, the only real tricks revolved around the ever so handy bottle of “compressed gas.”
sad thing is i have picked a lock with just a swiss army knife blade, although it only works against the cheapest of locks
The movie untraceable wasn’t horrible. Some things were put in place to keep the story alive but the hax weren’t too bad.
I mean, the movie itself was a crapfest but they did ip tracing and what not. However the FBI did completely fail at shutting down his website which was rather far fetched.
Trust me when I say, I have no idea how the writer got any of that right. I have personally met Dr. Brinker(Look it up if you don’t believe me), the man can not even use an iPhone without help. So honestly I have no idea how he got any of those details even that close.
Independence Day. Aliens travel across the galaxy with shields and laser weapons, but forget a firewall/anti virus program to protect the mother ship from being blown up by a virus. Really, what are they running, Windows 95?
“Independence Day. Aliens travel across the galaxy with shields and laser weapons, but forget a firewall/anti virus program to protect the mother ship from being blown up by a virus. Really, what are they running, Windows 95?”
Right. Aliens travel across the galaxy and by golly, their computer is code compatible with a PC?
werent they analyzing the system on the found ship? i beleve aliens support rs32, since serial connection is somwhant evolutionary necessary for computers, like the humanoid shape of the body in order to use tools
Actually, the scientists in “independence Day” supposedly had studied the alien technology for several years (Roswell incident) but on the other hand, they only had a few days to study the intact ufo.
Yes. Don’t forget, our computers were developed significantly after that crash. There are also several conspiracy theories that claim that aliens started sharing technology with us via Area 51 after that timeframe. In the real world, many things we have started out as military or government projects. It’s entirely plausable that in the ID4 universe our computers were developed starting with a base of the aliens computers.
The alien technology was Mac compatible.
http://www.youtube.com/watch?v=fmWzBtJ9o7E
I seem to remember a deleted scene available on the DVD where they made some mention of having reverse engineered the computer system, found it to be a lot slower than you might think (sorta like how your average calculator is more powerful than the flight computer on the space shuttle) and wrote an emulator.
I believe CERT released a (humorous) Virus alert shortly after the show hit the theatres warning aliens a:)not to use the enemies satellites against the enemy b.) turn off Javascript…
Also love that they somehow knew a compatible language in order to write the virus.
http://www.cracked.com/photoplasty_8_30-error-messages-you-never-want-to-see_p32/#9
Awesome!
Real Genius FTW!
+1
real genius….. I was talking about that yesterday. How about “my science project?”
Oh, god, how about Sandra Bullock in “The Net” — nobody’s going to find that tag on that web page that’s the key to the whole secret network, are they?
And I have to nominate every hollywood movie where some teenager sticks a card with a bunch of wires hanging off of it into an ATM and twenties start pouring out.
We had a programmer leave a 2 pixel gap between some Xwindows in a full screen display, Otherwise filling the screen. A client quickly found it and was able to open other Xterms.
Oh, god, how about Sandra Bullock in “The Net” — nobody’s going to find that >a> tag on that web page that’s the key to the whole secret network, are they?
And I have to nominate every hollywood movie where some teenager sticks a card with a bunch of wires hanging off of it into an ATM and twenties start pouring out.
The series 24 has a lot of really bad computer stuff. Also, the movie Antitrust. Where the compiler keeps telling them how many percent complete a module is in coding. And HTML is the language of choice.
They did use java and overall the message from the movie was great.
Many of the terminology they used was pretty good.
The one thing that has always bothered me about 24 was the goddamned digital counter font they used between scenes and intro/outtros. 7-seg digits do not bounce around, having variable spacing between, say, a 1 and 0, the digits should be fixed in place! Also the 1 had a serif that didn’t fill the entire top segment on an obviously-not-alpha display.
For hardware hacking I must say I am fond of the CCTV gadget in NATIONAL TREASURE. Still very fictional, but it looked just like something you’d find on HaD. Riley was a great character, and it made me so happy to see a hacked-up WRT :)
Though not perfect, I also approve of the soldering, sand casting, and wheel-grinding in IRON MAN 1 & 2, and BATMAN BEGINS. Downey and Rourke actually look like they’ve soldered before…
Hackers of course is bad but in a funny way. There is also Office Space, Control-Alt-Delete and Live Free or Die Hard just to name a few. It not really intended to be taken seriously, but its still funny to watch. I have to agree that Wargames was actually pretty realistic for the 80’s. On the hacking side, I’m going to have to say MacGyver is the greatest. That is one name that always comes to mind when someone hacks together hardware (or at least a rubber band, paper clip and a drinking straw) lol.
over 250 comments and just one mention of Die Hard 4 (Live Free or Die Hard). ?
a cool movie in my opinion, with some flaws. but i won’t list them all ;-)
and another movie, which hasn’t been mentioned, is eagle eye.
AntiTrust has a scene where he Hacks a PC and manages to get it to play live feeds from a ton of sources just with %showall. I found the whole movie’s code wasn’t too bad. HTML in relevant places and syntax that looks like something you would use in CMD etc.
Yeah, that scene in AntiTrust where he’s viewing the security feeds immediately came to mind when I saw this. I wonder if that’s available in HD… I haven’t seen it in forever.
Only thing I didn’t like about it was the very end, it seemed painfully so forced… Especially how, if I remember correctly, it ended like “WELL SHUCKS, one of our friends got horribly murdered and we were involved in a dangerous conspiracy and whatnot, but hey, WE’RE ON TEEVEE! AWESOME!”
But it gets points for actually keeping me in suspense at a couple points, not many movies can do that.
Nobody mentioned Antitrust yet? Sure, the end where they type in the ip addresses was amusing, but the part about the protagonist hacking in was quite realistic. He used real unix commands. But that’s about it. Other than that, The Social Network throws some words around, which are in some connection with hacking.
I enjoyed Hackers. Sure it was not realistic, but laughing at all of the pathetic mistakes, weather they are serious or not, was the fun part for me.
GUYS
GUYS
I HACKED* THE GIBSON
* guessing the persons 3 letter password after hearing it from your friendos
Is it a high-end supercomputer or a high-end guitar?
Hack the planet!!! Hack the planet!!!