We love seeing hard-core firmware reverse engineering projects, but the number of hackers who can pull those off is relatively small. It’s possible to grow the ranks of the hacker elite though. A hackerspace is a great place to have a little challenge like this one. [Nicolas Oberli] put together a capture the flag game that requires the contestants to reverse engineer Teensy 3.0 firmware.
He developed this piece of hardware for the Insomni’hack 2013 event. It uses the Teensy 3.0 capacitive touch capabilities to form a nine-digit keypad with a character LCD screen for feedback. When the correct code is entered the screen will display instructions on how to retrieve the ‘flag’.
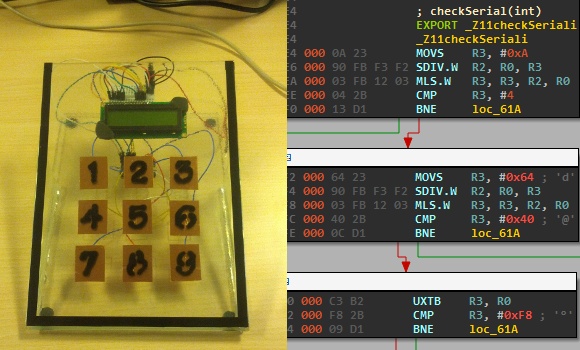
To the right you can see the disassembly of the .elf file generated by the Arduino IDE. This is what [Nicolas] gave to the contestants, which gets them past the barrier of figuring out how to dump the code from the chip itself. But it does get them thinking in assembly and eventually leads to figuring out what the secret code is for the device. This may be just enough of a shove in the right direction that one needs to get elbow deep into picking apart embedded hardware as a hobby.















…But, can’t they just find the flag as a string literal in the binary? It’s a shame the checkSerial routine is adequately obfuscated, yet the goal is right out there in the open. I hope to see more projects like this though.
Unless, they actually compiled two versions. Gave out the binary to the contestants where it actually says “XXXX…” and load the binary where it has the correct string.
This is the easy part. Getting the code out of a “fused” device, not so much :/
whats the color scheme in the code?
consonance
wait no I lied, it’s something else. I dunno.
Is not exactly the same but it look great, thanks
Closest I can find is Desert http://www.vim.org/scripts/script.php?script_id=105
Looks like Monokai to me. In fact, the whole editor looks like Sublime Text 2.
Featured in an wikipedia:MIT_Mystery_Hunt of years of yore:
http://web.mit.edu/puzzle/www/2003/www.acme-corp.com/teamGuest/R/7_175/gnireenigne/
Involves reverse-engineering PIC firmware just to figure out the puzzle.
ok, how do I get started on projects like this? In other words, how do I start picking apart embedded hardware?
Did you ever find anything on this? I’m curious, too, as I’ve been keen to get involved with reverse-engineering embedded devices for some time now. There doesn’t seem to be many resources or books on the matter, though :/
Cheapest and easiest way to start would be on a widely available, cheap, well documented platform. I recommend the Gameboy Classic. Check out http://www.bennvenn.com/mx.html as an example