It had been requested that we make a short video covering the top worst hacks in movies. Being the community that we are, it seemed like an interesting request. We asked for your input, and you were happy to deliver! However, the proposition of creating a “top 10” list turned out to be quite difficult. There were just SO MANY horrible scenes that I started thinking about how to even categorize them. We could probably to a “top 10” in any of the following categories without even having to dig too deeply:
- hacker lingo
- mocked up interfaces
- fake input devices
- virus screen-takeover moments
- access denied messages
- hardware taped together
Honestly, after breaking it down in such a manner, making the top 10 movie hacking failures, felt painfully general. It is like making a list of “top 10 animals that ever existed”. The state of technology portrayal in movies is frankly abysmal. It is obvious that the only people who know less about tech than “hollywood” are the people making laws about it.
So, lets take a look at this list and see what we ended up with.
10. The Core
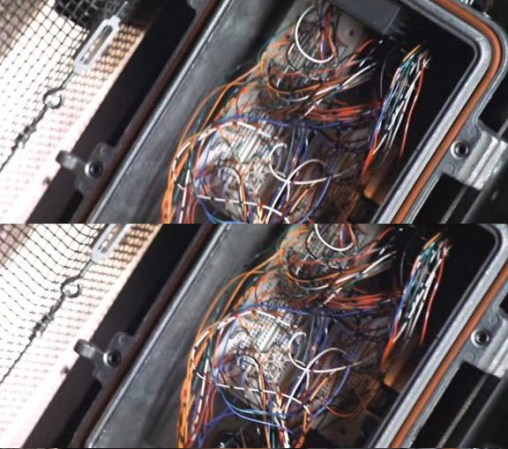
There’s a scene where they have to get through a door and it won’t budge. To open it, they’re going to have to crack into the control panel and hotwire the the thing. What do they find inside? A breadboard. Ok, well, we all know that in that environment, you wouldn’t be finding any breadboards. Then again, I’ve seen some duct taped together networks in large corporations that might convince me that this one isn’t a failure at all.
I’ve heard so many people point out this scene as a failure, and it is usually for the wrong reason all together. The young woman sits down at a computer and announces to everyone “hey, I know this, it is unix!”, while the camera switches to a 3d rendering that looks like a physical layout of a neighborhood.
“aha! that’s not a real interface!” is usually what I hear from people, but they’re wrong. It was called FSN and did actually exist. No one really used it though because, while neat, it wasn’t a great way to actually work. Tons of people loaded it up and played with it, but it never really caught on. I actually wouldn’t have been surprised to see a super gratuitously funded IT department loading stuff like this in their spare time because they had convinced the boss man that they totally needed that SGI for… uh… network security or something.
The real hack failure is the fact that her simply recognizing the operating system means that she now has full control over EVERYTHING in the Jurassic park network.
8. Firewall
This one is fun because it gets into a little hardware hacking. I LOVE improvised devices, so it caught my interest. It turned out pretty silly though. In the movie Firewall, [Harrison Ford] needs to get data off his screen to someone far away. To pull this off, he rips the scanner head from his fax machine and attaches it to an ipod. He remarks that the ipod won’t know the difference between “10,000 files or 10,000 songs”.
This is where the hackaday crowd really comes into play. Many will recognize that it is wrong, but only here will you find people that might actually figure out how it would have to really work.
First, you need something to read the data from the scanner head. Then, it needs to be converted to an actual file that is compatible with the ipod. Then you would have to initialize the transfer onto said ipod. That means that there’s got to be a decent amount of hardware and code going on in between the two items. To be fair though, they do show something there as an interface, so maybe I should have left it off the list. However, I challenge anyone to pull this off as fast as he did.
7. Goldeneye
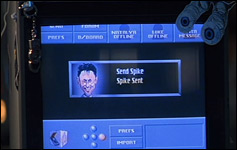
In the beginning of the movie Goldeneye, they are establishing just how fantastic [Boris] the hacker is. After an “access denied” screen that could easily be part of another list, [Boris] proceeds to hop into the network of the CIA. When he’s caught, he simply issues this magical command: SEND SPIKE. The nasty security guy who caught him is immediately disconnected. Wow. I don’t even know where they were going with this. I guess it was just supposed to be another notch on the “[Borris] is amazing ” tally sheet.
6. Hackers
This movie always comes up when talking about hacking. Some people love it, some hate it. The accuracy of the movie is about as divided as the fan base as well. They do a decent job of showing how tedious and silly hacking can actually be, but when they show the 3d renderings of the data, it all falls apart. However, this movie was released in 1995, and at that time we really had high hopes for the immediate future of 3d interfaces (see FSN). It is like our generations version of “jet pack disappointment”. I was promised spacial file navigation and I’m not upset that it hasn’t been delivered.
5. Swordfish
Swordfish came out in 2001. It has no excuse for 3d renderings of data. By this time we knew that the 3d interface of the future wasn’t really very usable (again, see FSN). Not to mention the gratuitous blow job/ gunpoint uber hacker scene that made my beverage attempt a quick escape out my nasal passage.
4. Skyfall
In this latest installment of the James bond series, I was incredibly let down. As a child, I found [Q] to be one of the coolest things ever. I wanted that job, bad (this job is slowly turning into that actually). When I heard that the actor who played him passed away, I thought they would take this as an opportunity to do a resurgence of gadgetry with the new [Q]. Unfortunately they continued their slow slide toward an entire 2 hours of sullen looks and knees to the ribs.
The scene that really almost caused an aneurism was where [Q] proclaims that the only way to look at the data on the computer is to attach it to their network (wow, really?). Then they proceed to look at the encrypted data as a giant 3d sphere. This trope is already bad, I mean why would you look at encrypted code as a sphere? On top of that, [James Bond] recognizes a word in plain text. This somehow unlocks all the encryption.
What comes next is the really painful part. We are looking at encrypted CODE. When you decrypt code, you get code. Sure, you might be able to then RUN that code to get some kind of a visualization, I guess. What you don’t get is your encrypted code morphing into a visualization of a map.
Hackers don’t put bombs in peoples computers. If they did, they wouldn’t set them to initialize using a keystroke. I mean if you can remotely make their screen go all wiggly, can’t you just detonate your damn bomb?
I’m not exaggerating when I say that I didn’t know if this was a joke. [Jack Black] does that bit where you rotate an image in a direction that is physically impossible. [Jack Black] is a comedian. Admittedly I didn’t see this movie till after [Jack’s] career was more established, so maybe it wasn’t as obvious back then.
1. Stupid Crime shows on tv like NCIS, CSI, BONES, etc.
Yes, I know it isn’t a movie. They’re just so amazingly horrible that I couldn’t leave them out. It has become this massive joke just how horribly incorrect they are. It has actually gotten to the point that I’m convinced they’re doing it on purpose. While I can understand a tiny bit of writing being targeted for audiences that aren’t familiar with the technology, some of it is simply too much.
The example of “two idiots one keyboard” is one that stands out. It is conceivable that you or your audience may not be familiar with hacking, or don’t know what a believable game would look like, but every one of you has used a keyboard. The script was probably written in a word processor using a keyboard. Hell, this is older than computers themselves, typewriters have them. Two people can not type on a keyboard simultaneously. It doesn’t work and everyone on the planet knows it.
























Got to put primer up at the top of “realistic” hacks… Since I assume that the nominee must be “fiction” this movie comes as close to the real portrayal of hacking (or just science and engineering) in a fictional setting as I have ever seen.
How about top 10 tech hardware fails? In “Executive Decision” it’s bloody obvious the stuff on top of the bomb is fake because the cover is off the hard drive and the head arm is bent up so the head is way above the platter.
There’s an episode of “Numb3rs” where a company building an autonomous attack drone has a bit of a problem where the drone likes to blast its own control site. There’s an almost neat pile of tech-junk in the middle of the blasted van, one of the characters makes a comment about highly advanced technology – but sitting on top of the pile is an old 286 or 386 motherboard with all ISA slots and 30 pin SIMM memory. No wonder the drone went gaga… “Try to control *me* with a 30 year old PC?! Take that!” *BRZZZAAAP!*
Did you know that ironman suit uses HTML in it’s console. Go watch second movie and zoom-in when Natasha Romanoff is “hacking” into Rowdy’s suit. xD
Speaking of movies, Caleb looks kind of like The Dude.
I always enjoyed how movie/TV hackers can access any system, no matter how secure, with one or two line of code.
What’s the definition if irony again?
I liked the scene in the new Dredd movie. They are tracing a call and trying to figure out where it comes from (or trying to open a door I believe).
Uses nmap in a very reasonable looking shell. Even featured on their website!
http://nmap.org/movies/
The Tron legacy hacking scene is pretty cool, the guy used emacs for the looks and some cool commands.
http://jtnimoy.net/workviewer.php?q=178
I wish my computer could beep funny sounds when i’m typing…
https://www.youtube.com/watch?v=hkDD03yeLnU
http://www.youtube.com/watch?v=KUFkb0d1kbU
People complain that movies and in particular TV shows don’t have enough of a certain minority class (gays, blacks, women, aliens, etc) and need to reflect a perfect world.
Wake up! With all the logos and adverts onscreen we need one more on all the time on every channel.
This is not real. Noneducational.
For entertainment purposes only.
Holeywood only varies by orders of magnitude of non reality, agreed.
Macgyver!!!
In Goldeneye Boris could have been using the fabled “+++ATH0” ICMP
Hacking win, Red Dwarf.
http://www.youtube.com/watch?v=KUFkb0d1kbU
Uncrop!
So well done, I had forgotten about this. Much better put than my rant.
Why has nobody mentioned, “The Girl With The Dragon Tattoo”? Although they don’t focus in any significant detail her process of surveillance and hacking, what was depicted is quite accurate IMHO.
every ultra security hacking scene should be a timelapse of the hacker in his chair with remains of junkfood stacking on the desk with the hair of the hacker growing and stuff,, and then the typical day night cicle ,which shows that time has passed XD
Uh? I dont remember the name of the movie even, but the one with the bomb to go off with a keystroke, did you even watch the movie? they were sitting outside with a remote detonator to “arm” the bomb so it wouldn’t go of prematurely.
Not mentioned previously, but one I use regularly with starting engineers. “This isn’t Ironman” referring to the scene when Stark, after utilizing his “brilliance” and 3D holographic CAD system effectively presses the print button to have his designs sent off to some fabricator who will have it ready to suit up in a few days. http://www.youtube.com/watch?v=GwmPfp1yWNY
Today so much of kids novel interactions with design are experienced through media with its idealized rendering of the way the world works, when exposed to engineering in the real world the experience can be underwhelming in its slickness and overwhelming in its complexity.
Yeah, but the flipside of that is those kids who are underwhelmed with the way things are sometimes make strides toward fulfilling their desires. Would we have awesome stuff like multi-touch touchscreens, portable projectors, Kinect, etc.? Perhaps in time, but I think without the influence of optimistic and unrealistic sci-fi, many advancements would be much slower to come to be.
Guys, seems that you never use your right hemisphere brain…take care with the film “Dumbo” …there is an elephant capable of flying by using his ears as wings….argh!!
Didnt they use the in store cameras in enemy of the state? Id like to believe that there is some crazy software that will virtualize what is suspects to be a different angle when given enough points of data.. all the other stuff was rubbish, lol. I can’t hate on Hackers though, that is my fav movie of all time and is probably responsible for my interest in computers in the first place.. HACK THE PLANET!!!!!!!!!
Agreed on CSI.
Regarding NCIS I feel like much of the “hacking” scenes are humorous (I hope so)
I think Girl With The Dragon Tattoo did some things well. I can’t remember which version though. She definitely did a bunch of things through her investigation that were very realistic.
war games…. all day……
Because showing real hacking in movies would be visually stunning, yeah command prompts are real eye candy. It’s representational, not literal.
As 0.zer0 mentioned, Takedown is probably one of the best hacking movies out there, although it is mainly about social hacking (about Kevin Mitnick).
I’m also surprised not to see “The Net” being mentioned (with Sandra Bullock) it’s a decent movie albeit a bit dated by now. Don’t bother with The Net 2 though…
I saw that CSI show when it aired, and my jaw just fell open when the two actors crowded in and both started typing furiously trying to out hack the bad guy. I hadn’t considered that it may be a joke, but that gives me some hope for humanity. Honestly, how could something so utterly idiotic have gone all the way from a writer to the actors without someone somewhere saying THIS IS TYPING, NOT PLAYING A DUET ON A PIANO!
I just watched enemy of the state the other day lol, I think that the image rotation as you call it could be done being that its a video file and the get several angles from the different frames but not what they need they then have the computer speculize what the other side would look like I have seen head scanner programs do that with 2 images to create a 3d model I know head shapes are much easier to pull off but hey it was the nsa!
‘I’ll create a GUI interface using Visual Basic. See if I can track an IP address.’
Cloudy with a chance of meatballs has the best, most accurate incorporation of computers into the script and execution was masterfully done. http://youtu.be/jtIFbCj5ndI
One thing that I’ve learned from movies is that you always guess the password on the third try.
This reminds me of how they show/showed receiving e-mail in movies and TV shows, it went from totally ridiculous to normally ridiculous to sometimes realistic now.
I guess once every single person including senators used e-mail they had to relent in their insanity.
As for it being needed for ‘dramatic purposes’, have you ever seen how they portray being shot in old movies from the 50’s and earlier? They felt they had to act it that way, but really it was silly.
In reality a more realistic depiction of things can be done and in a way that is much more dramatic, you just need a decent director who gives it some thought.
Pretty sure the last Q (john cleese) is still alive :)
I will not doubt that governments have some VERY neat toys. Take the case of this information:
http://www.rootsecure.net/content/downloads/pdf/optical_tempest_crt.pdf
http://www.nsa.gov/public_info/_files/cryptologic_spectrum/tempest.pdf
http://dev.inversepath.com/download/tempest/blackhat_df-whitepaper.txt
I will summarize the material as best I can,
1) light even diffuse reflected light can give be used to see whats on a monitor without direct line of sight to the display
2) signals can be transmitted even by accident in such a way a useful signal can be recovered from distance or in truly unbelievable circumstances.
Now given some of this data is decades old, using a form of “security” moors law one can reasonably anticipate that while Hollywood has made some ENORMOUS blunders (2 at one keyboard etc) things like Enemy of the State can are are very-much closer then you would like to believe. I think it deserves a bit more credit then given here.
second
http://www.oceansystems.com/forensic/forensic-Photoshop-Plugins/examples.php
This is the first link in Google that I pulled up for the term “image enhancement government evidence”
Something to note is that its while again Hollywood has taken GREAT liberty in the amount of recoverable information from very poor quality image sources. The fact is that it can be done, and today its cheep and easy. It comes down to case by case.
One must give a reasonably leeway to entertainment companies for “trying” to be both entertaining and not bogging one down in the mind numbing detail/time it takes to pull off a successful hack.
Closing thoughts. I knew a gentleman who’s job it was to work for a three letter agency his job was to provide silent electrical power from a gas generator in the 1960’s spying on the Russians in and around Germany. The effective distance of the signal equipment used necessitated getting within only a few tens of meters of the target, usually much closer. The system he operated had to be quiet enough that his team was not discovered while running said gas electrical generator. One can imagine a “silenced” engine. This was 50 years ago. He did his job, was the only member of his crew to survive and to this day we (at least in the US) owe him a great deal. He and his team pulled off a great number of field hacks as well as implementing the “technical” and “theoretical” hacks you and I could only imagine. One of my personal favorites that come to mind from some of his stories, a “mouse trap” for a Jeep. (yes a full size snap trap)
http://www.youtube.com/watch?v=QGxNyaXfJsA
Argus-IS demo video
http://en.wikipedia.org/wiki/ARGUS-IS
This is considered unclassified, one can imagine what is still classified as far as capabilities.
I truly think some of the videos on this list are much better given the brevity of the medium then we as more “educated” audience members give credit.
My personal faves for decent hack flicks, with the above latitude given, no order
1) War Games
2) Enemy of the State (why did you blow up the building?, Because you made a phone call!@”
3) Sneakers
4) Matrix – (Search “holographic universe” :)
What about ‘antitrust’ (startup) – I like that movie (html code in the intro – ok, maybe invalid but who cares – and some *nix cli action ;-)
I feel the latest episode of Dr Who (BBC) falls happily within the realms of poor hacking viability. Also not a movie but hey.
Cracked.com called, they want their article back…
I’m going to have to call you out on the Jurassic Park example and give back some credit to Crichton/Spielberg. They covered their tracks; making sure to presage Lex’s interest in hacking earlier on in the film (at around 1hr 26mins in):
Lex: “I’m a hacker!”
Tim: “That’s what I said: you’re a nerd.”
Lex: “I am not a computer nerd. I prefer to be called a hacker!”
So, as a self-proclaimed young hacker, she may very-well have been very skilled in navigating the OS…
yeah, I otherwise enjoyed that movie – so I explain the capability of her “hacking” as: the guy who put in all the “security” systems was depicted as a neurotic, spoiled, incompetent asshole. So even a 12 year old girl with passing linux familliarity could get in, and enable the door locks.
I really like this collection and agree that there are so many bad examples that it is hard to judge them. BUT I strongly disagree on “Enemy Of State”. Overall the movie execellently depicts the dangers of institutional data collection and combination. You could say it tends to be a little paranoid. From my point of view: One should be, but YMMV.
With regards to the 3D reconstruction from 2D imagery you are several years behind the current research in computer graphics, e.g. http://tinyurl.com/cymgqaw (and that is not even SOTA today). And with me being a little paranoid, I really think that the more scary 3 letter agencies do in fact have a head start on the current publically accessible scientific research. As have many of the big international companies with their R&D departments.
To add something constructive: From my point of view you could swap the second place for “Independence Day”; hacking an alien space ship with an Apple laptop was my personal all time candidate for failure in depicting hacking for many years. But I have to give you NCIS etc. They are downright failing epically and just make me want to scream all the time.
Kind regards & Happy Easter!
Carsten
Nice roundup. My personal rage inducing rant is when CSI et al take a grainy video image and magically enhance a detailed image of a suspect out of a reflection. “It’s ok sarge, we can take a low res image and enhance it to get facial recognition off the reflection in the teaspoon on the table in the background”. Damn you Blade Runner for starting this tripe.
so i was watching the latest episode of doctor who (bells of st john), and robots invade britan and upload peoples minds if they connect to this wifi network (bandwidth, huh :D). so, the mind of the chick is partially uploaded and the doctor grabs the laptop she used to connect to this network. he starts to randomly press keys and werid gibberish lines of code starts to appear, and the upload reverses and puts her mind back in her brain.
well, he is the doctor, so its probably legit.
In The Matrix, Trinity uses NMap to port-scan a PC, and a remote root exploit to reset the password, which she then uses to log in – The one and only time I have ever seen real hacking in a movie :D
http://nmap.org/movies/matrix/trinity-nmapscreen-hd-crop-1200×728.jpg
except they faked her scorpion kick. :(
Excellent post. BTW, most of TV programming is designed to condition the public to except or treat as normal/everyday, things that would otherwise be viewed as strange if not unreasonable and or totally ridiculous like a zombie outbreak. No I’m not kidding. As ridiculous as it sounds a sizeable percentage of the population is now conditioned to believe that a zombie or zombie like outbreak is feasibly possible. Not only that but many believe that the only way to kill such infected persons is by shooting them in the head as all zombie films have taught them to do. So what? No big deal right? The issue with this and societal conditioning is that you can subliminally program the public to react in specific ways to specific stimuli.
If there were an outbreak of some bio-weapon that resulted in symptoms including
a) lost their skin color (turning a dead like color
b) Inability to speak clearly (mumbling)
c) Disorientation and inability to walk properly (stumbling around)
It would be easy to see the public freaking out and with the push of some media, believing that a real zombie outbreak had occurred. While this would most likely be cleared up in a few days, one could easily see a large number of persons being killed by the un-infected who believed they were zombies and were doing as they had been conditioned and shooting these people in the head before they could infect or attack the rest. If you were to add some power outages and or loss of communications in to that you would have the makings of mass murder and all by nothing more than letting loose a bio-weapon and then turning of the power and phones for a few days.
While the idea of a true zombie apocalypse is ridiculous there is nothing impossible or improbable about bringing about a fake zombie apocalypse just as I described if you have the power/resources to create and then distribute a bio-weapon and disable public utilities for at least a few days.
TV and film are about conditioning the public to react in as specific manner and these ridiculous hacking examples on TV and flm are about getting the public to believe that hacking is really as easy as made to look on TV & film.
“The state of technology portrayal in movies is frankly abysmal. It is obvious that the only people who know less about tech than “hollywood” are the people making laws about it.”
It’s funny because they’re the same people.
SNAP
The movie hackers 1995 was made when all that “stuff” was fairly new. You’re joking, right? You freaking kids…
That two idiots on a keyboard vid was more ridiculous than it appears. Here’s a few more issues with it. Guaranteed intrusion detection. Every enemy access and operation is caught in real-time. Every access that’s caught displays the entire target file on screen in a new window. Typical buzzword dialogue. They have the enemy’s source code (not binary or assembler) in seconds and it’s on screen.
The epic conclusion: the guy saves the *network and servers* by pulling the power on the *client* terminal. In reality, he would have stopped the analysts and attacker’s would have extra bandwidth.
Tangent conclusion: they didn’t use a UPS. ;)
Nick P
Security Researcher
Also with the crime shows is the flashy UIs…don’t complain about the time it takes for a fingerprint search to come up if you insist on having each fingerprint and face flash across the screen while it is searching…sure a black screen would return the same result in 10% the time :)
Ha Ha. Yeah or even faster.
Leave it to Hollywood to show the govt. having all programs have guis and nice eye candy apps and wallpapers.
Most government places still use win XP.
you missed all the fun in Swordfish. he hacks while getting BJ – this can’t be true with computer nerds :)
you missed all the fun in Swordfish. he hacks while getting BJ – this can’t be true with computer nerds :)
http://www.youtube.com/watch?v=zfy5dFhw3ik
Another from those NCIS/CSI/etc. fiasco’s which really irkes the b-j-sus out of me:
Why does the IAFIS need to download the entire bio and mug-shot of each and every person it’s searching through? Flipping through each one in turn while “searching” for the fingerprint match ….
If that were the case then the internet would probably die every time some cop in a backwater town want’s to find out who swiped the can of soda in the local mart.
Not knowing entirely how the actual search works, I’m sure it uses some form of hashcoding instead of searching each and every item in the database graphically like depicted in these shows.
For that matter, the hand-held scanner might be a lot closer to the truth, though is it perhaps overly so? Tending to give reults within a few seconds, whereas the one run from a PC takes hours if not days!
Whoa no Weird Science on there.
Yeah – last time someone asked me to “hack their iPhone” for them (this was just a few weeks ago – literally the day after the law went into effect); I told him to google it.