[Pierre Dandumont] just finished up a little project that will give Google Maps’ location feature a run for its money. It’s a technique that spoofs WiFi networks in order to relocate the positional data reported via WiFi networks.
He starts with an explanation of the different ways modern devices acquire location data. GPS is the obvious, and mobile network triangulation is pretty well know. But using WiFi networks may be a new trick for you. We’re not 100% certain but we think Google is able to look up location data based on known IP addresses for WiFi access points (this would be a good comments discussion). To trick the system all you have to do is feed some captured AP data into the computer before Google Maps tried to lock onto a location. The video after the break shows Maps with the legit location displayed. After running a quick script whose output is shown above the map position is changed to the spoofed location.

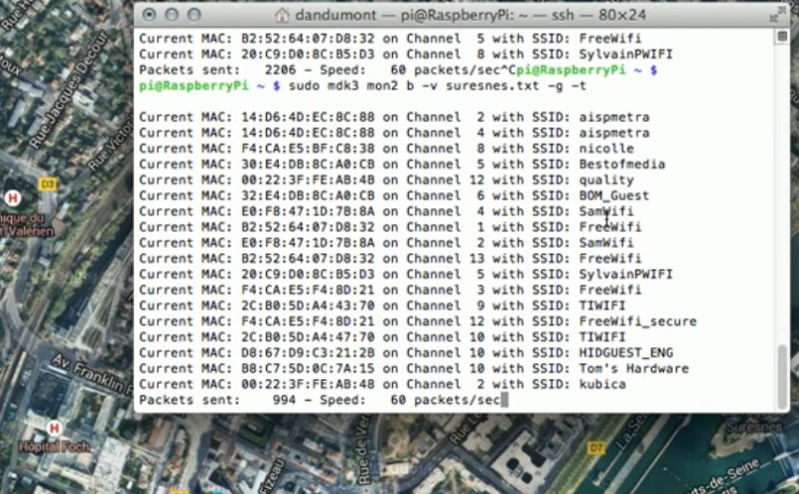














It’s simple. Whoever sees wifi’s mac address with GPS position fixed sooner or later sends this combination to Google. Next time someone sees this mac it will query google and google will know you are at that location.
Google doesn’t look up location from IP address. At least not that precisely.
Besides IP’s change. It looks it up from the Wireless access point MAC address. It gathers the location of Wifi MAC’s using Android phones and Google Street View cars.
Apple gathers MAC locations using iPhone. (And I bet that Microsoft does it using Windows Phone.)
There is also a community based MAC address geotaging project: https://wigle.net/
??? Android phones spy for Google!? I knew they were connecting Wifi hosts to physical location through the Streetview cars, for which they rightfully got a lot of criticism in the press. But my phone’s spying for “don’t be evil”? Cos that’s pretty evil!
Can this be disabled? I’m pissed off enough that the network thinks it’s ok to send my location to any website that wants to know.
FWIW there is already an app that does something like this. It spoofs location, on your phone. Not sure how low-level it is, how completely it solves the problem. If I were a spy I’d probably be searching Ebay right now for a 30 yr old briefcase phone.
The first time you run android it asks you if you wanna contribute giving anonymous info like this. And you can enable/disable it later in the settings if you want.
No. It’s off by default, and it asks for your permission and notifies you every single time you turn on that feature.
OTOH you can’t opt out of collecting and just getting its benefits: either you use network location (and collect info occasionally) or not.
When Google first introduced that feature it was a horrible battery drain because they kept enabling wifi in the background to scan for APs.
You might be pleasantly surprised by the speed at which a smartphone can obtain a GPS lock. From a cold start my phone will obtain a GPS fix in under 45s. It might be using AGPS to assist it in getting the lock, but no data is ever going to Google, and my battery life is much better now.
Every mobile phone is a tracking device within about 3 meters to the mobile telephone companies. Based on the speed of light and how long it takes for your mobile to send signals to nearby base stations. Don’t even have to be in a call to be tracked, mobiles send and receive data the whole time. Being annoyed about “don’t be evil” tracking you, when your telephone company already can (They do record the signal information for quality purposes, and to help figure out where new base stations should go to improve future coverage).
your logic is fail, instead you should be saying ‘phonecompanies are equally bad and it sucks’.
And this is about wifi, obviously if you use a wifi device you can disable the phone radio (airplane mode) and then the pnonecompaniy doesn’t know.. Not to mention all the android devices like tablets without a damn phone radio.
So when the software tells you that you are in airplane mode, you believe what it is telling you is true ?
Just like when there are no lights on your phone you know and trust that it is actually powered off.
Most of the time it is true, but with phone companies having the ability to remotely (and silently) upgrading firmware on devices, it all comes down to who do you trust.
With big data, it is cheaper to track everyone and look patterns than to do the right thing.
http://www.reddit.com/r/worldnews/comments/1jlf84/the_fbi_can_remotely_activate_the_microphones_for/
http://news.cnet.com/2100-1029-6140191.html
Yes, turn off wifi and never turn it on again.
Google has been using the wigle.net DB for sometime now. When street-view was barred from continuing to collect AP MAC addresses what do you think they turned too? Try this: ‘wardrive’ a remote location that has not been sent to wigle, (use the wigle android app or your favorite Linux or windows app) upload the data. Turn on location access from wifi networks feature on your smartphone (Android or apple).
Now watch as your location that would have displayed nothing before appears out of thin air. ;)
Street View cars collect the information?
They certainly used to. There was a big hubbub about streetview cars recording wifi signal strength and how it used to be publicly available(albeit slightly obscured). It got taken off the web/encrypted a couple years ago but the capability is there.
The issue was about they also grabbing more detailed info including packets with passwords, since they were doing it for the damn NSA as we can now conclude by what we now know.
when are you uploading your tin foil hat project :3
NSA projects are their own doing.. not Googles.
Are you being held hostage without access to ANY news?
If not..
Here’s something to read http://thestringer.com.au/google-and-the-nsa-whos-holding-the-shit-bag-now/
They used to use the streetview cars for this, but don’t anymore. They don’t need to anyway when they have every android phone correlating access points with gps location. You’re supposed to be able to opt out your AP by adding “_nomap” to the end of the SSID, iirc. Also, google says if you have a hidden network it won’t be included.
[sarcasm] Google certainly seems to claim they use WiFi with far more accuracy than any of these methods describe. When in range of 3 or more GPS signals, my phone tells me it is accurate to within 2KM (I guess it is just by accident that my blip is always exactly where I actually am), and that to get better accuracy I need WiFi. Even if I’m in the middle of nowhere with no WiFi at all, turning it on makes google maps claim I am accurate within 3 meters. They must be using some kind of alien super-wifi-with-no-signal that covers the whole planet, but destroys GPS accuracy, at least in google maps, but oddly not in any other GPS apps. [/sarcasm]
Personally, this whole MAC address geotagging thing seems to be a joke. MAC addresses are only slightly more stable than IP addresses, they are often duplicated in multiple locations, and they even move (I have a Linksys in my truck…they might be smart enough to filter out mobile hotspots, but what about actual routers…isn’t mapping those the whole point?) Google actually got sued for collecting such data with their streetview cars, and yet they still do it with Android…insane!
It works, doesn’t it? Try moving about with your GPS disabled, and you will likely find that (though choppy) your location is fairly accurately measured.
Yes, APs move about, but honestly it’s not very frequently, and with a little sanity checking on Google’s part you won’t find yourself in Australia every time you drive past that new guy’s house.
No, MAC addresses are pretty stable, as they were meant to be unique. IP adresses are not unique, and I bet 90% of the readers with an hotspot at home will get and IP in the 192.168.x.y range.
Even if the MAC are duplicates, they will have a unique set of neigboors. So Google can know with a high degree of confidence where in the world you are. They have a big database full of MAC/coordinates, and they are very good at correlating data.
Google got sued for capturing actual data traffic with their cars. They sniffed web traffic, not MAC addresses.
MAC duplication is not a real problem, unless you only have a single router visible and no other means of approximate geolocation, since it can just filter them out (e.g., if the GSM antenna is in Spain, the router it’s seeing can’t be in Japan).
Non-fixed hotspots can be marked as such as soon as they’re logged in different locations on a short period of time. If an Android phone sees your Linksys in your driveway in the morning, and another sees it in the afternoon 30 miles away, that’s easy to identify.
And no, Google got sued for collection actual data packages, not this kind of information (MACs and their location). It was a stupid blunder from people who should know better, but it doesn’t invalidate their Wi-Fi tagging project.
Google also collects this (but not only) type of information through Ingress (their own game, developed by Nyantic Project, a branch of Google).
BTW, if needed, i have some invitations to use ;)
this is old news. everyone does it since ages. apple, google, microsoft…
their phones collect the MAC adresses of wifi hotspots and combine them with gps location data and store them online.
there was even a website, (i think it was apple), where you could enter a MAC address of a wifi hotspot and it would show you on a map where it is located.
(funny stuff happens when someone moves and takes his router with him, takes a few weeks until the new location is updated, until then the map service of your phone might get the wrong position.)
and google did not get sued for doing this.
people check your facts.
they got sued because their streetview cars did not only log the mac address, they
actually logged the whole wifi traffic. in case of an unprotected wifi, they had all the passwords, files, datas and so on logged. and even with protected wifi this is not ok, someone could try to crack it.
Google Maps API has a manditory “sensor” perameter. If your device has a GPS sensor it sends “&sensor=true” and the data is submitted into the system and weighed against other data. Otherwise your device would send “&sensor=false” and no data would be submitted.
As others said it’s known fact the big 3 are collecting info on WiFi AP’s and cross-referencing this against location data. One AP probably isn’t enough to definitively nail down a location, but when you have 2 or more you can normally rule out duplicated MAC id’s(this hack being the exception to this). There was even a point in time when you could query a server with a MAC ID and obtain estimated coordinates – I’m sure it’s still doable but not as easily.
I personally don’t like anyone keeping tabs on my network and location like this, but there’s nothing you can do – even if you spoof your own MAC and disable location services on your phone, your neighbors are still collecting all of that info and blindly sending it all off for cataloging.
Great, there goes all my portals. Ingress was meant (not really) to get us fat nerds off the couch and in to the world (to collect location data for the big G). Now with freely avaliable wifi spoofing, most hardcore players will now be on the couch again.
For those that don’t want their AP to be used for google’s location service, they have a horrible opt out method. Simply change your AP’s SSID to include “_nomap”. So if it is “linksys” change it to “linksys_nomap”…. Then go ahead and update every single wifi connected device in your house with the new AP info. Simple.
That’ll stop them acknowledging publicly, not from storing and gathering and disseminating and sharing with the governments.
Then you’re just on a “special” list of people who are suspicious by virtue of not wanting to be included in projects for “the common good”. Yeah… that’s not getting you out of anything but surface level lists.
Sharing _what_ with governments? That a router with a certain MAC exists in a certain location? Why the hell would any government be interested in that?
Is that a joke? That question.
It seems to be but sometimes appearances can deceive.
Or better yet, use a linux router OS and make it change the MAC address every 15 minutes to something random to screw with their data.
I once took my Access Point to the beach. My android phone (While indoors) was sure that I was at home(50 miles away). Simple as that.
Hm. My phone is my access point. Have to try borrowing a friend’s phone and try Wifi each from the other. See if I get a time paradox, or it just explodes.
I just don’t see why anyone would want to spoof the geolocation data. It really makes google services better, and we all benefit from that.
It’s a clever way of adding another layer of accuracy to the geolocation.
I have to agree with you. A lot of needlessly paranoid people it seems, does anyone here actually have a valid and specific reason to obscure the location of their AP?
Ironically, this even makes a case for capturing packets; which is what Google got in “trouble” for.
Especially back when it occurred, and it was exclusively a non-realtime process using only Streetview vehicles, there was genuine utility in capturing all information available in the limited window when a vehicle was present; so that later an automated script could potentially reanalyze the data and immediately filter out or correct erroneous conditions that were not originally anticipated. So while I cannot vouch for Google’s exact motives, I can say there is a valid reason for them doing so. And if it were me in charge of the project at that point in time, I would have chosen to capture packets as well.
That’s not so much of an issue now that it’s a more realtime process. But it appears that the hack described here not only has the potential to falsify the location of a single AP, but also make that AP look like multiple AP’s. What’s the limit? Hundreds? Thousands of AP’s, all at false locations? Can it also mimic other AP’s and disrupt their proper location? And what if hundreds or thousands of people are doing this simultaneously? There is malicious potential for an attack on Google’s service here. How would they filter it out? By gathering more information, possibly including packet capture and analysis again. Or by manufacturers starting to include an unchangeable and unique ID on every device. Or maybe something else, but any solution would ultimately be a greater setback to privacy than merely having the location of your AP correctly known.
I’ve lived long enough to witness that paranoid people tend to make what they fear a reality, by their own actions. And then, rather than realizing this, they claim the end result was justification for their paranoia in the first place.
“I just don’t see why anyone would want to spoof the geolocation data”
OK; Some I know of has been selling not-exactly-government-sanctioned goods and services for quite a while. All of his traffic is relayed through multiple APs each 1-3.5 miles away. (In a heavily urban area that gives you several 1000s of geolocations.) He has many, many APs – >100. (Including pwnd Adnroid ssh servers – mobile.)
So far a fair number of those unsuspecting (see: dumb) individuals – whose geolocation Google actually has – had their doors kicked down and hauled away on Federal charges. He still has more than enough “remote links” to stay in business ohh, for about the next 15-20 years. (But I’m sure he would thank you personally for your starry-eyed urging not to worry about geolocation :-)
You were saying?…
the “Packetbruecke” project seems to be an earlier realisation of the mischief..
http://www.aksioma.org/packetbruecke/
How many of you folk that say Google does this, or Google can’t do that, actually work at Google and know what they are talking about?