Recently, Google discovered that a certificate authority (CA) issued forged certificates for Google domains. This compromises the trust provided by Transport Layer Security (TLS) and Secure HTTP (HTTPS), allowing the holder of the forged certificates to perform a man-in-the-middle attack.
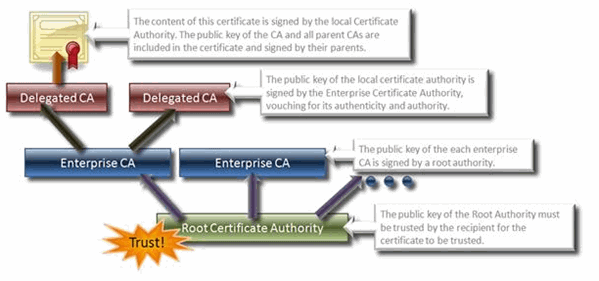
To validate that the website you’re visiting is actually who they claim to be, your browser ensures that the certificate presented by the server you’re accessing was signed by a trusted CA. When someone requests a certificate from a CA, they should verify the identity of the person making the request. Your browser, and operating system, have a set of ultimately trusted CAs (called root CAs). If the certificate was issued by one of them, or a intermediate CA that they trust, you will trust the connection. This whole structure of trust is called a Chain of Trust.
With a forged certificate, you can convince a client that your server is actually http://www.google.com. You can use this to sit between a client’s connection and the actual Google server, eavesdropping their session.
In this case, an intermediate CA did just that. This is scary, because it undermines the security that we all rely on daily for all secure transactions on the internet. Certificate pinning is one tool that can be used to resist this type of attack. It works by associating a host with a specific certificate. If it changes, the connection will not be trusted.
The centralized nature of TLS doesn’t work if you can’t trust the authorities. Unfortunately, we can’t.















Though I think I’ve seen this elsewhere, it would probably be helpful to post the CA in question so we can all set them to untrusted.
i kinda wish hackaday had a like button so i could show appreciation for the sentiment for the last line.
Seconded. At the risk of sounding like a tin foil hat wearing werido……Trusting any authority should be done at your own risk/stupidity.
I frequently find myself in need of a like/upvote button when I find and insightful comment. Rather than clutter the commentfields with a reply, I tend only to post if I have something meaningful to add. (Aparently this is also a valid reason not to respond to my girlfriend’s “happy anniversary” text.)
Case in point: you all could be spared from having to read this comment if I could have just clicked “like” on rusty’s comment! :p
Why aren’t the public keys stored in DNS with the CERT RR? Combined with DNSSEC you can check the certificates against the one presented.
Because turtles all the way down. How can you trust the DNS server?
That is why they implemented DNSSEC on the root servers.
I don’t think you know what problem that solves.
To change the chain of trust in DNS with DNSSEC enabled, you need to get the TLD to alter the NS records for the target, so that a CERT RR (and *all* other RRs, including subordinate domains) would be served from the rogue server. Once any TLD gets caught altering the DNS that way, you will have a /global/ problem and the DNS system would collapse as completely untrustworthy and unusable.
Why is no mention made of this particular incident having been perpetrated by the French Ministère de l’Economie et des Finances, aided and abetted by ANSSI, seemingly to spy on their employees?
These buggers will continue getting away with this shit if no one ever calls them out. Google did, and even UK media and web sites covered it.
I thought you Merkins are the ones that are free? Shame on you HaD
Helluva way to spin something into bigotry via nationalism.
Oh, re-read it and try to understand it this time. Clue: Google is a Merkin company…
What they did is illegal under French law, which is why it is currently all over the French media like a rash. When a legislature, or its supporting Ministries, decides that it’s exempt from the laws it sticks down everyone else’s throats, then it’s the very definition of corruption.
“even the UK media” is hard to construe as a compliment, and a good example of the pusillanimous nature of much of the UK media would be theregister.co.uk, which seems to have a bunch of lawyers weighing every comment, lest it attract litigation, or discomfort our government, yet “El Reg”, as they call themselves, is as trivial as they come.
Nevertheless, to feed your sense of outrage at any apparent slight, even if solely caused by your own muddle-headedness, I still maintain that the likes of HaD should provide the context underlying the articles that it publishes. It actually does matter, and failure to do so when that context demonstrates an organised and deliberate policy of breaking both French and European law is hardly the act of those who are proudly, and genuinely, free, rather than just paying lip service to something that was stolen decades ago, whilst avoiding the attention of some hired fatmouths.
This stuff actually DOES matter. Ever hear of a guy called Ed Snowden?
Thanks for the information, I was wondering who had did that? You’re right it is important to know that. But I’m guessing N.S.A. and the like all over the world are doing the same wrong.
http://en.wikipedia.org/wiki/Merkin
Thank you so much for pointing this out. Unfortunately it is not “currently all over the French media like a rash” and I had to dig the news from few sources.
http://pro.01net.com/editorial/609928/le-ministere-des-finances-a-falsifie-des-certificats-google/ (in french) does not reveal why the certificates were forged. To them this is just a human error of no consequence.
If I was spying on my employees’ SSL connections, I’d just push a self-signed cert out over Active Directory. No need to hijack a CA.
That doesn’t help if your employees use macs, Firefox, or phones.
Certificate pinning is impossible with Google. I was using Certificate Patrol and Google uses hundreds of different certificates, possibly one per server, and had to basically disable it on Google. Also, they recently changed CAs.
What frightens me is that the attacker could have used the certificates to impersonate the update servers for Chrome and distribute their own, code-signed, version chock-full of spyware without raising a single red-flag.
Not true, Chrome does certificate pinning for their own update servers.
what if the attacker already distributed their payload via update servers for chrome; and the end resulted in letting the readers of HaD know he compromised the CA(s) :) btw I’m using firefox and see the article.
I recently bought a couple of Android tablets (cheapies), I’ve avoided many of the Google apps, just because they want more of my private information than such an app would really need. And now this… yecchh! I don’t think I’ve entered any credit card information over those tablets, nor have I done any online banking with them, for reasons such as this…
Namecoin solves that trust problem