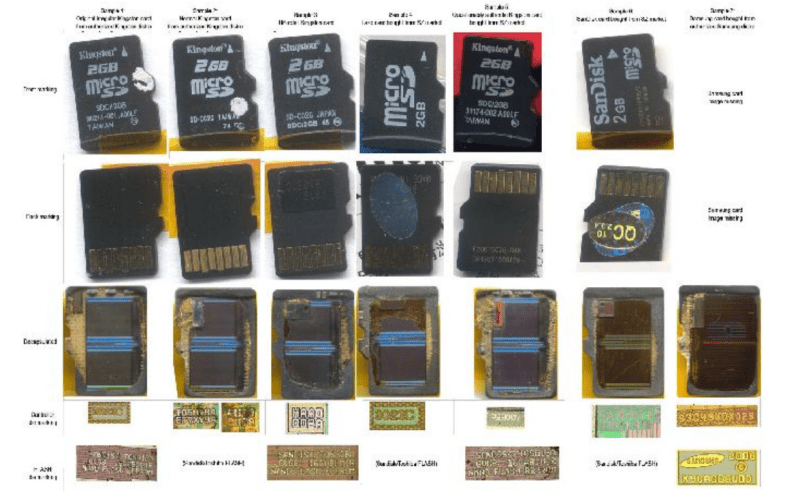
We hope that some of our readers are currently at this year’s Chaos Communication Congress (schedule can be found here and live streams here), as many interesting talks are happening. One of them addressed hacking the memory controllers embedded in all memory cards that you may have. As memory storage density increases, it’s more likely that some sectors inside the embedded flash are defective. Therefore, all manufacturers add a small microcontroller to their cards (along with extra memory) to invisibly ‘replace’ the defective sectors to the operating system.
[Bunnie] and [xobs] went around buying many different microSD cards in order to find a hackable one. In their talk at 30C3 (slides here), they reported their findings on a particular microcontroller brand, Appotech, and its AX211/AX215. By reverse engineering the firmware code they found online, they discovered a simple “knock” sequence transmitted over manufacturer-reserved commands that dropped the controller into a firmware loading mode. From there, they were able to reverse engineer most of the 8051 microcontroller function-specific registers, allowing them to develop novel applications for it. Some of the initial work was done using a FPGA/i.MX6-based platform that the team developed named Novena, which we hope may be available for purchase some day. It was, among others, used to simulate the FLASH memory chip that the team had previously removed. A video of the talk is embedded below.
















These guys have too much time on their hands, but I applaud their work, it makes the world a little better.
wouldn’t it be great being paid doing this kind of stuff? :)
Are you suggesting some sort of crowd-funding arrangement where you find a project you would like to see more of and chip in a few dollars, regardless if you get anything useful out of it or not?
I hear the NSA is hiring… lots of time to tinker and hack, little to no oversight.
>little to no oversight
After Snowdengate? I don’t think so.
who was fired over that? no one. what change has actually been made? nothing. all snowdongate has shown is that they can continue doing what they feel like because they will get away with it
Rewrite the firmware to allocate a portion of the card as “hidden”. It wouldn’t show up on a normal directory listing (or sector dump – returns contents as “empty”) unless unlocked by special program and password. Password stored on chip, so even if the wrong people get the card and program they still can’t unlock it.
You could rewrite the firmware to execute internal loops for the ones and zeroes on the card, which could be picked up by a nearby FM receiver. The card would function as a normal card, but when sent a special command would silently “sing” its contents to an eavesdropper.
Yeah – too much time on their hands. None of these uses is even potentially interesting.
That is a stupid preposition. FM receiver? God. Remove your last line and you sound like a normal person with a wild idea, add it and you become this idiot savant who has no idea what they are talking about. If you listen to the talk and read the talkback and just comprehend the simplest physics, electronics, and computer topics – you’d know that.
busy-loop effected fsk bandwidth would be extremely low and can’t think of a scenario where introducing a hacked sd card into your target environment would be a preferable alternative, but you never know…
Awesome work though and very much looking forward to documented register maps and extended op-codes to be able to make use of an ultra cheep super beefed up 8051 dev board with many Gb of n/v storage. Pity the appotech manuals aren’t PD, or are they? How did bunnie get his hands on the oem firmware bootloader?
You’re right, Appotech’s manuals are not normally in the PD.. That said, Appotech make (and have made) some awesome 8052 variants in the past. For example, I’ve used an AX-2005 MCU (i.e. a really fast 8052 with on-chip 32K ROM and 32K SRAM) to emulate an entire x86-based computer: http://www.fleasystems.com/flea86.html
Regards,
Valentin Angelovski
Re: Valentin’s Flea, ….. wow! I still can’t believe it’s possible! Very good work, and from a crazy idea, like all the best.
kalfjd, I’m sorry my post got you angry.
You will probably be getting angry more often as you grow up. You’ll find that taking a more positive approach will work better in the long run, but you’ll discover this for yourself.
For an experiment, try writing some code with internal loops and play around with an FM receiver next to your computer. See if you can get the code to make different noises on the receiver.
Be sure to get your parents’ permission, though – playing around with electric things can be dangerous.
That’s how the first computer generated music was done. Tech noticed that radios close to the huge systems made noises that varied depending on what the computer was doing. Someone then got the idea to write a program to deliberately make the computer produce a discernible scale of notes in it’s RFI output, then from there the next step was arranging those noise producing pieces of code into musical scales.
Computer music would have taken a very different path, perhaps have had a much later start, had the EMI/RFI shielding of the early, room filling computers been much better.
Wow. Just have a look at this:
and *please* be a little less complacent. Side channels are nasty. Much nastier than your (or my) phantasy.
For those too lazy to follow the link: those researchers were able to recover a RSA key by just *listening* (yes, acoustics!) to a motherboard repeatedly GPG encrypting some known plaintext.
Yes, a patched GPG is now available — phew!
dude
you should read scientific journals on cryptology and you would know that such a thing is possible, that from the sound created by a cpu or current drawn by a cpu things like that could heurestically be analyzed to great success,
Few years ago there were studies with WLAN to scan environments (much like a body scanner, or the car mounted ones) these days the first wlan gesture appliances are out (control light’s with gestures etc) obviously this could be used to scan living behaviour and other shit
Hey Joseph, you know I think they were waiting for your acknowledgement about their work. I’m sure they are super happy now. What have you done? Created anything? No, that’s okay. Those guys with “too much time” on their hands will continue trying things just because so that you can feel better.
The write-up that went along with the talk can be found on [bunnie]’s site: http://www.bunniestudios.com/blog/?p=3554
Been looking forward to this talk for a while, was happy to stay up until 6AM watching it. :D
This brings up a question I have about making a card identify itself as having a lower capacity than what’s actually there.
My reason for asking is an older camera
that will only handle a maximum of 2 gig memory card.
Also I would like to use the micro SD cards as they
are a lot easier to pack into a small camera bag.
Plus the newer, faster class cards always
seem to be only available in larger than two gigs,
So there’s another hurdle.
Just for giggles, I’ve tried formatting at a lower capacity
or using a partition manager utility to set the size smaller.
But as was expected, neither method works. :(
Try using a more low level partition manager to format it, hopefully not as two partitions but as one with a null space.
Your camera only accepts SD cards, and not SDHC or SDXC cards. Reformatting them to a lower capacity won’t solve your problem, since the communication protocol between the card and host differs.
No Joke!!! Plenty of open source datalogger firmware for FAT16 and FAT32 file systems…. but more and more it’s getting harder to find cards that size or smaller!!! Wouldn’t it be cool to take a 32 gig card and make it emulate (16) 2 Gig cards???
Open source you say? Then add support for bigger cards…
Camera firmware are not open source, they are peronatery (proprietary). It would take the same amount of energy these guys put into hacking the SD card in order to hack a given camera unless the manufacturer built it with the intention of allowing it’s functionality to be modified with firmware loaded from the SD card.
A camera is not an open source datalogger…
What’s your problem with his comment? Doing this kind of stuff requires a lot of time, too much for some people. He accknowleged their work and even said it makes the world a better place. That is totally true but isn’t for people overreacting on a unfortunately worded comments. I know this is useless but: turn down your hate a little bit.
But have they cracked the supposedly un-resettable permanent write protect bit?
Its as unresettablew and permanent as ATA Security Passwords, Spiegel.de had an article yesterday listing companies that have products with NSA backdoors, and surprise surprise
Western Digital, Seagate, Maxtor and Samsung are all listed
what a coinsidence, HDDs made by all those companies have “bugs” that let you bypass or read back ATA security password.
Well, shit! Still there’s proper stegasaurus and cryptkeeper software out there already, so this isn’t really a problem. [I’m trying to stay out of the philtrums of the NBA!]
What I tried first was just the in house window$ format.
The thing I tried was to wipe it and repartition as a single partition as FAT16
(same FAT as camera formats to)
with the rest of the card as unallocated space,
by using Partition Wizard home edition 8.1.1 (freeware)
Anyone got a better utility to recommend ??
and Yes I’m sadly stuck with a “ghetto” budget :p
–
@Tom- I wodered about any difference of communication methods between the micro SD cards and a regular one, I only have micro SD cards in anything larger than the 2 gig size at the moment.
So I couldn’t try the partition util on a regular SD card.
Would you figure a larger cap SD card would
communicate in the needed protocol to fool
the camera about card size?
@Steve- Yeah the idea of making a large card show as multiples somehow,
would just be bonus awesomesauce!
Typo: should have said that “the next method I tried was using the Partition Wizard …”
As Tom said, the SD card format was only ever specified as far as 2GB. Presumably some field only had so many bits. SDHC was an extension to the format, and the protocol is different. Since the protocol is programmed in at the factory, it’s presumably hard coded to only speak SDHC, whatever size the onboard flash is. It wasn’t designed to be back-compatible, unfortunately. So it’s not the size, it’s the protocol. Formatting won’t help.
They make 2GB micro-SD though. I think they still make them for the sake of all the old equipment that won’t take SDHC. Apart from a couple of pins missing, micro / mini / normal SD are the same. The size adaptors are just bits of plastic that run the contacts through, nothing active in them. A collection of micro-SDs and an adaptor should be fine for you, often you can buy a micro-SD plus the adaptor for a couple of dollars extra. 2GB cards are really dirt cheap anyway.
It’s not that big a deal, since older cameras don’t generate files big enough to fill 2GB easily anyway.
Does the camera recognize the card?
If so, have you tried formating the card with the camera?
Based on Greenaum statements. that would be a no. :-)
Thanks for the feedback everyone.
alas, card spoofing would of been sweet.
…and as for filling a card with an older camera?
just hand someone with ADD ( like me)
who doesn’t like shooting at less than max resolution,
a 5 meg sensor that catches reds, purples and bright
highlights pretty well.
Now then throw in exposure bracketing and a some good rechargeable “AA” cells
and just stand back for a couple of hours! X^D
Sometimes the simplest hack is to your wallet… pretty cheap though. http://www.ebay.com/itm/New-2GB-microSD-micro-SD-Flash-Memory-SD-Card-Generic-/251406123331
Bookmarked that page for when the “Piggy Bank”
gets a bit fatter. {..seems it’s the most petty crap that complicates ones life :( }
& just to be flippant a sec…
I hope that the company name of “BREED”
isn’t a euphemisti forewarning
as to what they want to do to my wallet ;^)
So you take a 16 gb card make it copy data from 8 gb data space to an 8gb hidden partition then market it to parents and wives to put on their children / spouses android phones
I want to see continuation of this research, but aiming at USB drive controllers (Alcor and the like).
Travis Goodspeeds Facedancer is a good start – it lets you write your own firmware for USB device. I would like this to go a step further and open all the billions of USB stick controllers to hacking.
Yes, we are here and having a good time at the CCC
Maybe the wrong place to ask, but are there any reverse engineered documents on the elusive SD bus modes?
This hack was done in SD mode (ie. not SPI mode). Hence, these researchers knew how to use it, so details must be available somewhere – check your local FTP server full of warez and you may just find the required documentation.
Somebody know how do it in SD mode?
SPI is trivial, SD mode is not documented
If you can make a converter from USB to MicroSD (not MicroSD to USB (MicroSD adapter)) you will have done what I have wanted so much in life.