[Josh Datko] was wandering around HOPE X showing off some of his wares and was kind enough to show off his CryptoCape to us. It’s an add on board for the BeagleBone that breaks out some common crypto hardware to an easily interfaced package.
On board the CryptoCape is an Atmel Trusted Platform Module, an elliptic curve chip, a SHA-256 authenticator, an encrypted EEPROM, a real time clock, and an ATMega328p for interfacing to other components and modules on the huge prototyping area on the cape.
[Josh] built the CryptoCape in cooperation with Sparkfun, so if you’re not encumbered with a bunch of export restrictions, you can pick one up there. Pic of the board below.

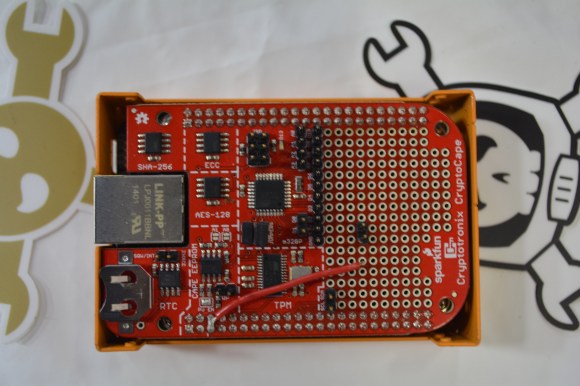















On-board is NSA Spychip #1, with innocent-sounding backdoor module #2 and special SUCKERCRYPT ROT-13 encryption.
At least software encryption is trustworthy in theory. If you understand the brain-bending maths, or trust someone who does. And even then it can take 10 years for the world’s collective geniuses to spot deliberate weaknesses in something we all trusted.
Hardware security chips need Superman’s vision and god-knows-what to defeat the countermeasures they put in “sensitive” chips.
And for anything with a set of constants, standardised by the government, you may as well use 4, 8, 15, 16, 23 and 42.
That’s one thing the release of the NSA’s hardware catalogue has demonstrated. ANY idea, from Wacky Races to The Matrix, has probably been invented and is in common use. They really will go to any length, they have the time and the money, and sub-contract out for the brains. Never assume that because something’s ridiculous, unlikely, or too much bother, than the TLAs and their friends wouldn’t bother doing it.
Yes, please explain how, other than completely trusting the HRNG, how these chips would be subverted.
By not being what they claim to be. All sorts of ways of subverting encryption, I’m not really knowledgable about how it’s done. There was a bit of a scandal a while back when the NSA wangled their way into supplying a random-number method involving elliptic curves, that was compromised. Something Snowden was involved with. That’s one method.
I’m sure there’s others. I’m not clever enough to think of any, and I’ve no idea what the API is for using the chips’ functions. Just that it’s the sort of thing they’d benefit from, and there’s ways they could do it without anyone knowing. They’ve gone to much further lengths. Spooks have influence all over the place. That’s what I know, and it indicates they’d do it. Exactly how, no idea, but it doesn’t matter for the point I’m making.
No, you aren’t really knowledgeable. Encryption and hashing algorithms are deterministic. Its either producing correct output, or incorrect output. If its producing incorrect output, your data can’t be decrypted by the recipient, and you can’t get plain-text back from what your are decrypting. Similarly with hashing. You’d notice.
And yes, the NSA got Dual_EC_DRBG pushed into a standard, but since it was pointed out that it contained a back-door, it was rarely used. It has nothing to do with crypto hardware, other than hardware can implement it and it certainly has nothing to do with Snowden (other than him leaking documents that confirmed the above).
About the only thing you can do to hardware specifically is make an hardware RNG that lies. Produces psuedo-random numbers instead of random numbers. It’d be very difficult to detect. *However*, its pretty easy to circumvent by mixing together several sources of random numbers into a pool.
Don’t go all black helicopter over someone who made a cool thing.
“At least software encryption is trustworthy in theory.”
Software, running on NSA Spychip #3, is trustworthy in theory?
You should try comedy….
Remember kiddies, if you can’t slip at least one finger between your tinfoil hat and your head – it’s too tight and you should stay in your bomb shelter until a new one can be fabricated.
Reblogged this on Beagle Blogger and commented:
Information security for everyone. Joshua Datko showing off his BeagleBone cape at HopeX.
Trust is what it is.
Maybe I’m not understanding the project, but can someone explain to me what this provides that the BeagleBone’s processor doesn’t already do? If I remember correctly, all of TI’s Sitara processors have a hardware TRNG, and cryptographic acceleration? I swear I’ve seen drivers for that stuff in the Linux kernel tree.
You’re spot on; the BBB has crypto accelerators for AES, MD5, and SHA. The CryptoCape adds RSA and ECC. Plus, I wasn’t going for acceleration so much as I was for key protection, which is the ability to generate and use the key in hardware.
My use case was avoiding the heartbleed like situation where a software vulnerability releases the private key.
The comment about trusting the hardware is a valid point. There’s really not much I can say against that. For me the choice is what’s more likely: a software bug compromising the system or a backdoor. Unfortunately, that’s a hard choice with the rise of backdoors these days, but that’s the choice IMHO.
None of this chips are particularly fast, but they do prevent the key from being leak and have some protection against DPA and glitching.
Thanks for the question.
When I use the cryptocape,I met some problems,like how can I change the PCR ,no metter what I do,the PCR never changed.
In the source code ,there’s some code can solve your problem
how can I change the PCR,the tpm_extend is not usable
how can I change the PCR