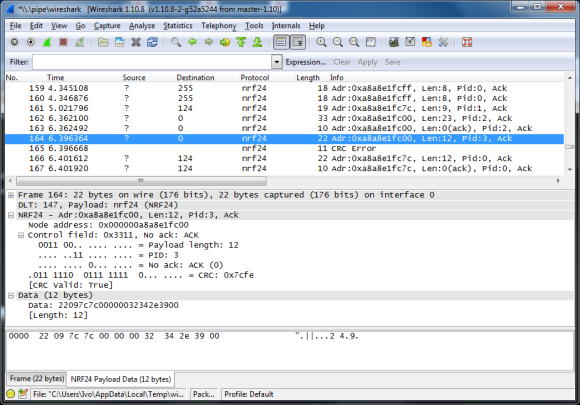
We’re sure that some of our readers are familiar with the difficult task that debugging/sniffing nRF24L01+ communications can be. Well, [Ivo] developed a sniffing platform based on an Arduino Uno, a single nRF24L01+ module and a computer running the popular network protocol analyzer Wireshark (part1, part2, part3 of his write-up).
As these very cheap modules don’t include a promiscuous mode to listen to all frames being sent on a particular channel, [Ivo] uses for his application a variation of [Travis Goodspeed]’s technique to sniff Enhance Shockburst messages. In short, it consists in setting a shorter than usual address, setting a fix payload length and deactivating the CRC feature. The Arduino Uno connected to the nRF24L01+ is therefore in charge of forwarding the sniffed frames to the computer. An application that [Ivo] wrote parses the received data and forwards it to wireshark, on which can be set various filters to only display the information you’re interested in.















Ohhh. This is SWEET!
Looks great. I will take a closer look at that this evening.
I just got these modules so this couldn’t come at a better time.
This is pretty nice. I’ve looked at the option of a RTL-SDR combined with a LO, but this is much cheaper and quite apparent. It already talks in the 2.4Ghz range, so why use something else..
Big up!
THis is really great work! I wonder if there is any module out there who might give access to the raw demodulated data…
Nice hack! I’ll definitely try this when I get back home to my lab.
NRF24_sniff:79:37: error: wrong number of template arguments (1, should be at least 2)
static CircularBuffer packetBuffer(bufferData, sizeof(bufferData)/sizeof(bufferData[0]));