With a proliferation of USB Flash disk drives has come a very straightforward attack vector for a miscreant intent on spreading malware onto an organisation’s computer network. Simply drop a few infected drives in the parking lot, and wait for an unsuspecting staff member to pick one up and plug it into their computer. The drives are so familiar that to a non-tech-savvy user they appear harmless, there is no conscious decision over whether to trust them or not.
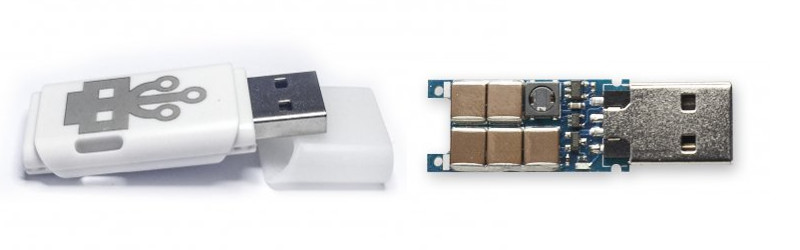
A diabolical variant on the exploit was [Dark Purple]’s USB Killer. Outwardly similar to a USB Flash drive, it contains an inverter that generates several hundred volts from the USB’s 5 volts, and repeatedly discharges it into the data lines of whatever it is plugged into. Computers whose designers have not incorporated some form of protection do not last long when subjected to its shocking ministrations.
Now the original has a commercial competitor, in the form of Hong Kong-based usbkill.com. It’s a bit cheaper than the original, but that it has appeared at all suggests that there is an expanding market for this type of device and that you may be more likely to encounter one in the future. They are also selling a test shield, an isolated USB port add-on that allows the device to be powered up without damaging its host.
From the hardware engineer’s point of view these devices present a special challenge. We are used to protecting USB ports from high voltage electrostatic discharges with TVS diode arrays, but those events have an extremely high impedance and the components are not designed to continuously handle low-impedance high voltages. It’s likely that these USB killers will result in greater sales of protection thermistors and more substantially specified Zener diodes in the world of USB interface designers.
We covered the original USB Killer prototype when it appeared, then its second version, and finally its crowdfunding campaign. This will probably not be the last we’ve heard of these devices and they will inevitably become cheaper, so take care what you pick up in that parking lot.
[via Extremetech]















I wanna know where these parking lots are that you can get dozens of free USB drives from… slight remedial action required.
Please submit your place of work:
Uhhh, I do some IT stuff for Westboro Baptist Church… yep, that’s what I do.
I would have steered them in the direction of the late Ron L Hubbard ( science fiction and fantasy writer ).
RW, what do you have against those loyal Democrats? You must be one of Trump’s deplorables.
+1
I work part-time at your nearest buy-here-pay-here car lot. We mark all our diagnostic USBs “*brand* Diagnostic”.
Maybe this will help us get the long awaited fiber optic USB/thunderbolt/whatever?
Maybe that’s why the optical bus industry is secretly behind it…..
they do exist but at the moment they are very expensive, works a treat though.
https://www.corning.com/optical-cables-by-corning/worldwide/en/products/usb-optical-cables.html
Wouldn’t the problem still exist though? Either way your peripherals will require power from somewhere, spiking the power lines with a high voltage could destroy things as well.
Next up would be transmission and subsequent harvesting of light from the host I guess. Not sure how feasible that is right now though.
The problem in question would not exist if the optical interface in a component of the computing device itself, so the optical cable is nothing but fiber (or a pair of fibers) and the mechanical termination. The neat thing is that for short lines, single mode, and moderate speeds, you can get away with a lot of sins at the terminations, so they can be inexpensive and physically robust.
Then they design an “optical port killer” that produces a 1/2 kW laser pulse to destroy the receiving hardware.
Joke aside, there is no practical way to make something completely undamageable in the face of clever people intent on causing damage.
Besides, that’s Fisher-Price’s job.
+1
Suddenly Windows XP starts to make sense, it was an attempt at protection.
Oh, I can’t wait to watch you charging your phone then :-)
You might think that a found USB drive should be treated like a hypodermic needle but I still hear advice of put your name in a text file in the root folder so it will find its way back to you from people who should know better.
I did have a “Contact” folder in a USB drive back when I went to college. I got a call from a plumber a couple days after I lost it. He found it in a parking lot.
my sticks are encrypted and backed up regularly. the hardware at this point isn’t worth anything compared to data.
I once found a USB stick when i was young, i immediately used it on my pc. Result: I had to wipe the whole HD since it broke my system. Since then i don’t even give them a second look.
Use a real OS, and there would be no problems ;-)
What if it enumerated as a keyboard, opened a terminal, and typed “sudo rm -rf –no-preserve-root /”? Are there still no problems on our real OS?
It would need the root password.
And besides, also do real backups.
I gave that to the system when I last typed sudo. Humans run with elevated privileges constantly. If you can enumerate a human you can break a computer.
Um… at least my keybindings are non standard, also – sudo needs password. But yes, you make valid point.
PS. Yes, there are two kinds of people – those who do backup, and those who do not backup yet.
bash: sudo: command not found
That’s why my system is configured to lock the screen when a HID device is plugged in. Bit of a pain using the Yubikey though!
No OS is 100% secure, especially with physical access.
also just a PSA, if you leave the usbkill in your cart at usbkill.com with a logged in account, they’ll send a 15% code in a couple days asking why you haven’t finished checkout ;)
That is now my new favorite tactic at all web stores!
I’m going to try that the next time I want to purchase something and the codes update too soon.
Thanks!
Sounds like the perfect time to invent the USB isolator. :-/
Well if your curiosity is going to get the bettet of you then a cheap hub plugged into a machine with non mainstream architecture should save you from immediate expensive mistakes.
Or a killer usb port.
If you look at the design it does not damage the +5 volt line or the ground, it spikes the data lines with -110 volts DC (version 1.0) or -220 volts DC (version 2.0). So it is easy enough to create test hardware, you supply 5 volts and ground and check the data lines for -110 to -220 volts DC. Maybe even use a battery with a buck converter to supply the +5 volts DC.
How many µF do these capacitors have? The highest SMD ceremic capacitors I’ve seen so far were rated for 100V and had 1 or 2.2µF.
No idea, but you could double the voltage rating by using two in series (and unfortunately half the capacitance). Or get 5x the voltage rating by using 5 in series (and 1/5 the capacitance).
Or just take a 200V or higher rated cap. They exist up to 630V. Of course capacity goes also down at given size. In this special application I would even short time overload the caps. They charge gets dumped immediately after reaching peak voltage anyway.
Or a USB-killer-killer!
Enter the Raspberry Pi – an effectively disposable, non-Windows computer with USB ports.
Now the motherboard manufacturers will add 2 bucks worth of MOVs, increase board price for about 50 bucks and put a big sticker “USB Killer resistant!”.
It’s like they are creating their own market. With more and more of them sold, hardware manufacturers have to buy them too to test their devices.
Yep! It’s called “franchising”
Not sure what this says about the human race in general.
“‘What a piece of work is a man! How noble in reason, how infinite in faculty? In form and moving how express and admirable? In action how like an Angel? in apprehension how like a god?”
More like
“How well supplied with noble counselors,
How modest in exception, and withal
How terrible in constant resolution.”
(Henry V, II, iii)
Wouldn’t we open the cover of a found USB dongle first to have a look ? Then those caps and that coil are a dead giveaway.
That was my thought.
We would.
Joe Office Worker probably wouldn’t, and may not even recognize what he sees.
With all those caps, I would imagine it should weigh 2 to 3 times as much as a normal thumb drive.
“Ooh! This one is heavy! It must be loaded with data!”
B^)
So it will feel like a “quality” thumb drive and people will be even more inclined to pocket it and plug it in!
So what will this do to all the other IoT things (TVs, etc…) that have USB plugs on them for expansion? (Though I think I have a good idea.)
Accelerate the inevitable by 12 months… It’s, it’s a time machine!
What is special about USB that makes destroying property become acceptable? You could easily modify anything with an AC cord to star a fire or even electrocute the user but that would be considered criminal.
The Etherkiller (http://www.fiftythree.org/etherkiller/).
I don’t think anyone recommended doing this to someone else, it’s the concept that’s interesting really. If you go around getting this thing plugged into other people’s stuff, then I think we can all agree that you’re a total asshole that deserves to get caught.
>If you go around getting this thing plugged into other people’s stuff
Looking at all the *#+ humans do i think this will be the case. I don’t know why they are selling this. They say that people that designing hardware should test there products, but why? They only need to make them protected against such stuff because somebody created the USB Killer. I don’t think repetitive surges with >100V are something that can happen during normal operation (in contrast to ESD or something like this). Of course, they might be an idiot discharging a capacitor on the local photo print station but well, you can’t protect against all problems and even if you want to do, do you really need such a “test tool”? If i really want to break something i just use a hammer…
And why should pen-testers have such a thing handy? To break the hardware of they employer? Yeah, you could argue that critical hardware should be protected against sabotage like this but imho critical hardware should be protected physically. You don’t need such a thing, just wire a random PC-connector to the mains (or use a hammer as i said)…
I’m thinking a good use case could be maintenance staff “sanitizing” public charging stations at places like coffee shops. If a hacker installs spy hardware to try to break into devices plugged into it, the “sanitizer” would zap it and render the station safe again.
What is needed is a usb killer killer.
Something like a hammer? ^^
Hey, I’m on an optimization and reduction to basics kick, what if you got something like a hammer, and took off the handle, and found some kind of natural material to use…
I believe that is what is known as a rock.
A couple thoughts on this:
If they made some that just explode, more people would learn not to plug in computer gadgets from unknown sources or they would learn to use their other hand until they did it again. Unknown sources being anything made in China. And what is the point in one of these things? Do they test them at the factory? If one of these did fail (to discharge into the computer) what would it do to the person holding it? People worry about a Zombie Apocalypse. I worry about hordes of stupid people looking for the next stupid thing to do.
Maybe the Zombie Apocalypse already happened but the infection is just a lot more subtle than in the movies. I seem to be constantly encountering people who look healthy enough but appear to have as much sense as a Zombie.
I’m starting to suspect that the world actually did end in December 2012 and all this is hallucination as the oxygen depletes from my last few brain cells…
That is a good idea, or perhaps it could just contain a heating element and a wax that has a really foul smelling substance embedded in it. It stink out the office and make a powerful point without doing any damage. Could be a useful security audit tool to check if policies at a given site were being followed.
Nice idea
If you are admin on a site though, you can probably figure out how to have usb sticks you scattered yourself email you with date time and user when they get plugged in.
Most people won’t bother with this. It’s not cheap and if you leave it in a parking lot you are not getting it back. Unless you know someone in the building you may not know if it ever worked.
i miss the time when HaD was good
not a hack
OP is
Nice ambiguity. ;)
I’m genuinely curious what you mean. I’ve thought some of the recent articles written by HAD staff on microprocessor programming, electronics, special printing filaments and history have been excellent. When do you think it was better? Alternatively, where do you hang out that you like better? I’d like to read such a site too. I’m not trying to be an ass, I’m just curious what you mean.
Old USB connector, they should get with the times and make a micro or lightning port version.
Or better yet ‘A propriety port killer’ .
Yeah just a mains cord with two probes on it, labelled “universal data signal rejuvenator, triples speed of any interface”
When I was a student, I was part of my university’s sound-and-light provider. We had a special offering just for those people who would come in and ask for “A cable”. It was a 1/4″ jack-to-240V mains plug, albeit one made with just the outer insulation of a piece of mains flex, no wires.
It was amazing how many people took it away without looking at what they’d been given.
Sysops are wondering about a special version… that they can slowly deploy throughout the network… and activate with a password the day they are fired.
You are not thinking that through enough. It would be a better design decision to have them automatically trigger once every 12 months, if they do not get the countermand signal to reinitialise the timer before the countdown period has fully elapsed. Some companies, in certain industries, have HR policies to escort people from the premises the day they hand in their notice.
the fact that that is even necessary says it all really.
Yeah, I’ve heard of that kind of dead man switch done in software.
I will gladly sell you a hammer, with a “LAPTOP KILLER” label affixed, for $30. SO HIPSTER
Comment section killer
##
Wow, that was close!
Careful what you read!
I admit, I worry about the amount of vandalism that might arise from these. The type of middle-school kid who used to take magnets to CRTs back in the day, is the type who will happily destroy property with one of these. Especially since it can be done so quickly, and with so little evidence. (“Honest, I just sat down and it stopped working.”)
Beyond filling USB ports with epoxy where applicable, I have no idea for a solution.
(No, I’m not suggesting they be banned from sale. And yes, I know that CRTs could be degaussed, though depending on the “damage,” it could take a pretty strong coil and a lot of effort.)
USB locks are available and have been for at least ten years. Not fully secure as they can be removed even without the key but that would take time and keep the casual paser by from f****** up your presuppose life(computer)
As an admin I’d leave front ports open but unplugged from mobo, so when user complains, you can tear them a new one.
Though perhaps a nice idea is to apply this idea in reverse… Wire up the case ports so they fry any device inserted… Then that’s one less device that will cause you shit another day.
Worse would be a brand name wall adaptor gutted with the AC prongs soldered directly to the data lines of the USB female connector. Left in a public place, a lot of grief would follow!
I would like to know where are those parking lots, at least i would make a battery/bank to supply rc toys or things like that.
Am I the only one who would like one of these that could be configured as a “dead man’s switch”? :)
Oh, just thought of a point unmade thus far I think. (Hey, sorry if I missed your oblique referral in a comment nest)
The slaughter of a cheap commodity desktop office PC might not be the point….
The point might be that you order another one, which is intercepted in transit, or even at source, and equipped with a full on suite of nasties to dig deep into your network and business, and inevitably, personal life and anything audible in the room that computer is in, possibly Van Eck intercepts from nearby systems, penetration of nearby air gapped systems etc etc.
The point might otherwise be that you call in external hardware support, who you let access your premises, with all the possibilities above, and bugs and wifi penetrators and the like that he might drop or install in ceiling or power sockets while he’s “lost” on the way to the bathroom.
A 5lb hammer does not require sudo.
Now we have USB Killer type-C
https://habrahabr.ru/post/310442/
so now someone has to invent a USB condom- a board to go between unknown usb drives and your computer that can monitor and protect the data lines