Although I’ve been to several DEF CONs over the past few years, I’ve never found time to devote to solving the badge. The legendary status of all the puzzles within are somewhat daunting to me. Likewise, I haven’t yet given DefCon DarkNet a try either — a real shame as the solder-your-own-badge nature of that challenge is right up my alley.
But at the Hackaday SuperCon I finally got my feet wet with the crypto challenge created by [Marko Antonic]. The challenge was built into a secondary firmware which anyone could easily flash to their conference badge (it enumerates as a USB thumb drive so just copy it over). This turned it into a five-puzzle challenge meant to take two days to solve, and it worked perfectly.
If you were at the con and didn’t try it out, now’s the time (you won’t be the only one late to the game). But even if you weren’t there’s still fun to be had.
Thar’ be spoilers below. I won’t explicitly spill the answers, but I will be discussing how each puzzle is presented and the different methods people were using to finish the quest. Choose now if you want to continue or wait until you’ve solved the challenge on your own.
Solve it in 1 Hour: Cheat!
First off, the only rule was: be the first one to email screenshots of the solution to badge@hackaday.com. In my mind that means there is no cheating, only varying levels of cleverness to accomplish a goal.
The crypto firmware wasn’t shipped on the badge, but given out as a precompiled hex file (find it in the files section of the challenge project). Even better, badge designer [Voja Antonic] hand coded this in assembly so it lacks the gibberish you’d expect to find when decompiling binaries that have been run through a C compiler. Check out the videos below and then challenge yourself to make sense of the decompiled hex. Some find this type of thing fun, others might consider it torture.
You can find both the compiled hex and the assembly source code on the challenge project page. [Sprite_TM] and [ThunderSqueak] both pulled up their decompilers right away, bypassing all challenges and getting to the final screen in under one hour. Can you do as well?
The Actual Challenges:
The challenges [Marko] laid out include five different rounds. There were some hints given when [Brian Benchoff] gave the talk (seen above) that launched the contest. Some of them were worthwhile while others were literally a red herring. He then flung thumb drives into the audience that were the first instances of the compiled hex in the wild.
https://www.youtube.com/watch?v=MmmL28WOuhk
Mastermind
The first puzzle is based on the game Mastermind. If you didn’t recognize it immediately, it shouldn’t have taken long to associate it with [Benchoff’s] clue. The game centers around guessing a combination. After each guess, the badge will tell you how many correct values you have in the right place and how many correct values you have in the long place.
For me, what took a long time is figuring out how the game is played normally, and then establishing what the badge version is telling me. You get feedback on the right after each guess and it took me well over half an hour to figure out what’s what. That established, I tried to get really good at Mastermind really quickly. This is folly. You have six chances to get the combination correct — a really high bar. I suggest you take a more mathematical approach to winning.
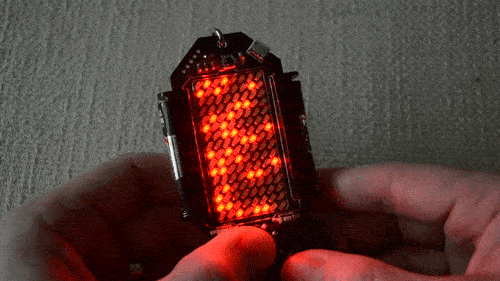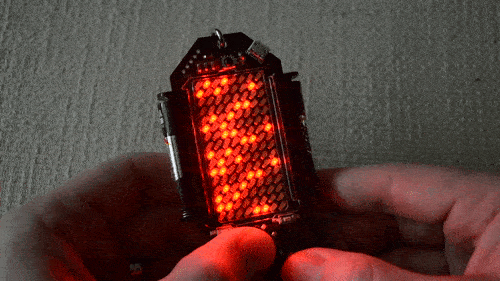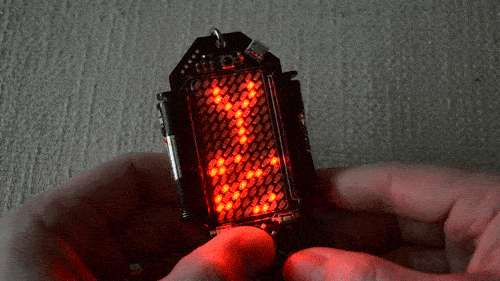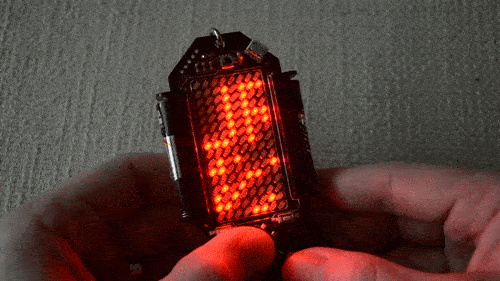
Blink, Blink Blink, Bliiiiiiink
When faced with a cluster of four LEDs blinking in unison it’s easy to figure out there’s some type of data there.
Playing with the buttons reveals alphanumeric input is possible. Decode this flashing, enter the correct answer, and you’ll work your way through to get the passcode for this challenge.
GO!
This one took me the most time, even though I cheated. A few days before the conference [Voja] had shown me the win screen for this one and it was still pretty hard.
The board is set up with the word GO. When you play around with the keys you find that there are four pairs of collumns that can be moved up and down. Align them all just right and you’ve solved the puzzle.
I knew what I was looking for so I just kept trying. But my initial thoughts were to transcribe all of the columns and write a script to show me every possible iteration. I figured if you put 40 of these on a page at a time, the fantastic pattern-recognition of the human eye would make the right one jump out at you — looks like [John Park] went that route too. However, there are something like 50 rows in each column for a total of 6.25M combinations.
So it’s not brute-forceable… how would you solve this?
Little Boxes
This challenge presents you with a clever little spinning cursor. Play around with it and you find you can set or clear any box in a 4×4 grid. There are no other instructions or feedback. But flip the badge over and you’ll notice what’s printed on the back silkscreen is a set of icons built on a 4×4 grid.
I think everyone does the obvious thing at this point. Try to enter each of the icons. This does nothing, but I spoke with [whosawhatsis] because I knew he was already working on challenge 5. His hint to me was that it isn’t depend on order that you enter.
Next I began writing some Python code to work on logical operations based on the glyphs. [Voja] walked by and saw me doing this. When we talked I mentioned I was going to try logical operations on each row of symbols. He gave me a clue that you’ll want to use more than just one row in those tests.
With these two shoves in the right direction it didn’t take me long to pass this challenge.
?
The final screen! Well, getting to that screen is a trick in itself. SPOILER: the stock firmware that came with the badges has a ball-bearing gravity demo that uses the accelerometer. It also has a dice roll when you shake the badge violently. I never discovered this even though I had the badge on hand for months. And that’s why I never would have found the fifth screen which is exposed by shaking the badge if someone at SuperCon hadn’t told me about it.
When you do get there you are greeted with a question mark. Playing with the keys lets you enter text. Each challenge gave me a code and I wrote them down along the way. I tried entering them here but I had 12 letters and challenge 5 takes only 8 letters.
In speaking with [Krux] about this he suggested that it was probably a cipher and pointed me to the Cipher Tools of Rumkin.com. This was fantastic advice, not only did it allow me to learn about different ciphers, but has the tools for you to try them out. About 20 minutes of poking around and I had it!
Many succeeded at solving the challenge but were slow to claim the top spot. That honor went to [Jonathan Dahan]. We’ll share more about his victory when we cover the badge hacking later this week.
A New Challenge: Emulation
So, you don’t have a badge, but you still want to play? Here is a new type of challenge for you. You have the compiled binary, you also have the sourcecode (both found on the challenge project). Who will be the first to port the challenge so that you play it virtually, without need for hardware?
If it helps, I already have an emulator that takes arrow inputs and shows a graphical representation of the screen. But this uses the SDL2 library and is meant for portable C code. You’ll need to do some work to get [Voja’s] assembly code to work elsewhere. But if you do, you’ll have done something truly unique so email badge@hackaday.com and let us know about the accomplishment. Post your emulator with enough details about how you did it and you may find yourself on the front page for the gnarly hack.
If you are hacking on the crypto challenge, we want to know about it. Please Tweet your progress @Hackaday with the #SuperCon hashtag.

















If I would have started on the challenge during the SuperConference with these clues, I would probably still be trying to solve it today.
So I guess I’m glad I gave up pretty quickly :-)
===Jac
Badges in the Hackaday store, or it didn’t happen…
None of your “Badges, we don’t need no stinkin’ badges!”.
You are not alone in this desire.
forgive my ignorance but would tina v10 not be able to emulate a PIC18LF25K50