Anytime you’re having more than a handful of people over to your place for a wild rager or LAN party (or both), you’ll generally need a way to make sure everyone can get their devices on the network. Normally, this would involve either putting your WiFi password into more phones than you can count or yelling your password across a crowded room. Neither of these options suited [NicoHood] and his partner, however, so he came up with another more secure solution to the WiFi-in-a-crowded-room problem.
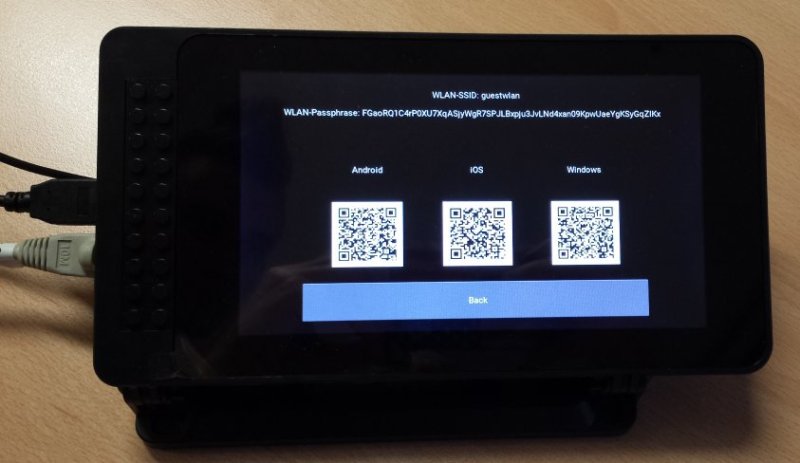
He calls his project “guestwlan” and it’s set up to run on a Raspberry Pi with a touch screen. When a potential WiFi user approaches the Pi and requests access to the network, the Pi displays a QR code. Within that code is all of the information that the prospective device needs to connect to the network. For those who have already spotted the new security vulnerability that this creates, [NicoHood] has his guest WiFi on a separate local network just to make sure that even if someone nefarious can access the Internet, it would be more difficult for them to do anything damaging to his local network. As it stands, though, it’s a lot more secure than some other WiFi networks we’ve seen.
[NicoHood] also released his software on Git but it has been configured for use with Arch. He says that it would probably work in a Debian environment (which the Raspberry Pi-specific OS is based on) but this is currently untested. Feel free to give it a try and let us know how it goes.
















While on the topic of network security, my local pinstripes uses their public wifi network for all of their printers, point of sales terminals, computers, etc. It was fun poking around it :)
I’ve heard a similar idea done with those NFC tags.
which is fine for Android and WIndows phones, but Apple locks down the NFC for use with Apple Pay only.
Friend don’t let friends use apple
One MORE reason to avoid the rotting fruit. (Damaged (bitten) fruits tend to start rotting soon.)
What if they are trying to connect something without a camera.
See that 60+ characters passphrase ?
Well, you better not miss an uppercase when you type it.
This!
This solution is pointless for conference situations where everybody bring their business-laptops with no QR-Code reading software on it. We also have a sheet with a Wifi-Guest QR-Code hangig in the conference room. Almost nobody is using it, because the top most use-case is laptop, not smartphone.
You should not be using a Raspberry Pi as an access point for your conference.
Thank you for pointing out the obvious situation no one would ever use this in.
You grab your cellphone, take a photo, turn on data, upload to cloud, turn on cellphone AP, connect laptop to said cloud, download image, throw it into an online qr code reader, copy paste the result and its done.
You wont even need an USB cable!
I was thinking someone along those lines.
I have no problem with an USB cable, but I would not want to have to use cloud. Of course it is no problem:
Scan and decode with cellphone, store as text. Copy to Laptop via Bluetooth or WiFi direct and copy/paste result to network login.
My “hack” is to run an open AP. No extra hardware required!
With many ISPs that is a violation of the contract…
Well then I guess it qualifies as a real hack! I should write an article.
Then you can still use an easy 4-6 character PW. Or does the contract specify a required password complexity? If yes, it still can’t be very high. My ISP uses 8 character (upper case and numbers) PWs printed on the bottom of the router/modem.
This leaves individual connections unencrypted. Better to just set a passphrase to 12345678 and be done with it.
I have considered this but decided against it for several reasons.
Such a password is trivial to crack and offers a false sense of security for users who aren’t educated about this stuff.
Open wifi (sometimes with captive portals, another false sense of security) is a widely accepted risk by the public.
I don’t mind if the neighbors and passer-by’s use the connection, but I don’t want to be on the hook for technical support should there be any problems. Sharing the password requires revealing who I am to every user, and sharing it in a public manner defeats the encryption as well.
I block services (such as FTP and SMTP) that are likely to leak passwords. Additionally I’ve found that these days, an amazing majority of the traffic is HTTPS. Normally all I see are HTTPS connections to Facebook, Google, and Netflix.
Finally, wifi is inherently based on trust. Until there is a solution to the pineapple attack, every time you use wifi you are trusting every device in radio range. Obviously it’s still a good idea to use a password for your personal network but the marginal benefit is not very big.
What’s the advantage of this over push-button connect (PBC) authentication? My understanding is that unlike PIN-based WPA methods, PBC doesn’t have any known vulnerabilities.
Except for the core concept of it. What if the attacker leaves a device in range of the network that acts like it gets its button pushed every 2 minutes so it is constantly waiting for the router’s button to be pressed? Then it’s purely by chance which device will be accepted into the network. Sure, if the legitimate device gets left out, the owner may notice it, but the default reaction is still “stupid thing didn’t work the first time, I’ll just keep spamming the button until it works”.
The protocol design mitigates this by failing to authenticate if it detects multiple in-progress connection attempts.
I use the write to tag thing for my phone.
A hack yes, but a solution in search of a problem. For temporary setups, I use a separate wifi router unlocked, or locked with the wifi password posted next to the conf room monitor.
An interesting solution to the problem of having a secure public wifi without bothering with setting up a captive portal.
you could generate a simple two word combo passphrase that expires after a certain amount of time too. today’s password is chickenclock.
The idea sounds nice, but is really bad in sense of security. If you know the wordlist that is used (or just try your own) the number of possible passwords is very low. The password can be hacked very fast. Even if you switch it every day. You can a) decrypt the traffic afterwards and b) you might be able to hack into the wifi fast enough if the wordlist is really small.
A comparison:
It takes 3 hours on my i7 laptop to crack an 8 digit password: 10^8 = 100000000
Now if you have a wordlist with 10k entries it would take the same time: 10000^2 = 100000000
You definitely do not want to use this approach. And that is also the reason why “word passwords” are not a good idea in any case.
I just create a temporary guest network with a simple pass-phrase on my router
Interesting but it should also be set to reset guest passwords after period X (1 day or so) and recreate a new one that is now displayed.
German router company AVM had this implemented long ago. Its routers have a second, isolated guest WLAN integrated with a generator for a QR-Code that holds the access info.
Just use you pi to connect to a vpn privacy service and share that link out wide-open, separate from any other network you have. That way it makes it easy for visitors to connect and you don’t have to worry about your IP being associated with “questionable” internet traffic. You can cap bandwidth or just turn the thing off when you don’t have company. Its best to keep it as simple as possible for guests.