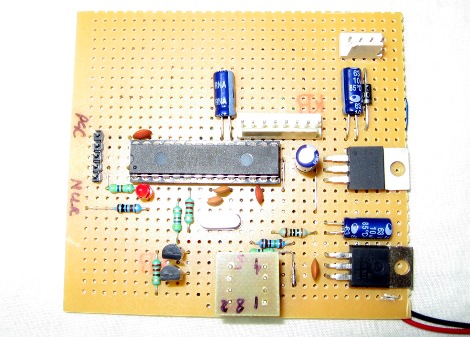
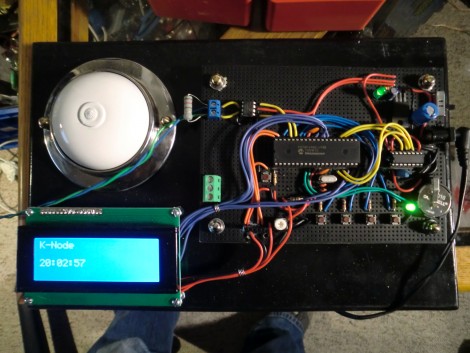
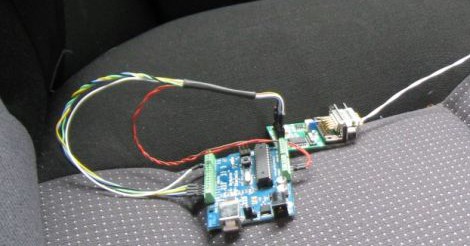
In the old days, a physical button or switch on the dashboard of your car would have been wired to whatever device it was controlling. There was potentially a relay in the mix, but still, it wasn’t too hard to follow wires through the harness and figure out where they were going. But today, that concept is increasingly becoming a quaint memory.
 Assuming your modern car even has physical buttons, pushing one of them likely sends a message over the CAN bus that the recipient device will (hopefully) respond to. Knowing how intimidating this can be to work with, [TJ Bruno] has been working on some software that promises to make working with CAN bus user interfaces faster and easier. Ultimately, he hopes that his tool will allow users to rapidly integrate custom hardware into their vehicle without having to drill a hole in the dashboard for a physical control.
Assuming your modern car even has physical buttons, pushing one of them likely sends a message over the CAN bus that the recipient device will (hopefully) respond to. Knowing how intimidating this can be to work with, [TJ Bruno] has been working on some software that promises to make working with CAN bus user interfaces faster and easier. Ultimately, he hopes that his tool will allow users to rapidly integrate custom hardware into their vehicle without having to drill a hole in the dashboard for a physical control.
But if you’re the kind of person who doesn’t like to have things done for them (a safe bet, since you’re reading Hackaday), don’t worry. [TJ] starts off his write-up with an overview of how you can read and parse CAN messages on the Arduino with the MCP2515 chip. He breaks his sample Sketch down line by line explaining how it all works so that even if you’ve never touched an Arduino before, you should be able to get the gist of what’s going on.
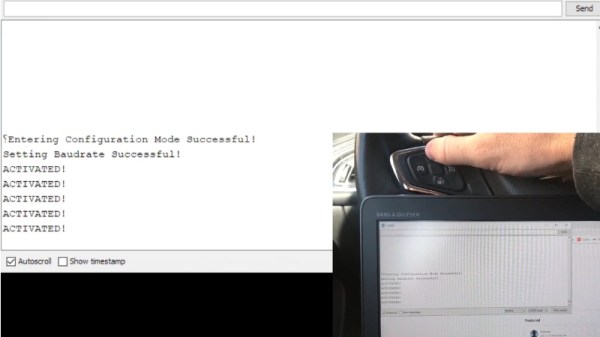
As it turns out, reading messages on the CAN bus and acting on them is fairly straightforward. The tricky part is figuring out what you’re looking for. That’s where the code [TJ] is working on comes in. Rather than having to manually examine all the messages passing through the network and trying to ascertain what they correspond to, his program listens while the user repeatedly presses the button they want to identify. With enough samples, the code can home in on the proper CAN ID automatically.
The upside to all this is that you can activate aftermarket functions or hardware with your vehicle’s existing controls. Need an example? Check out the forward-looking camera that [TJ] added to his his 2017 Chevy Cruze using the same techniques.
Continue reading “Developing An Automatic Tool For CAN Bus Hacking”


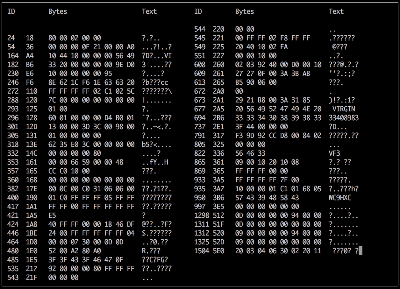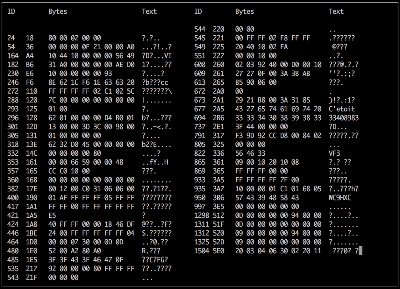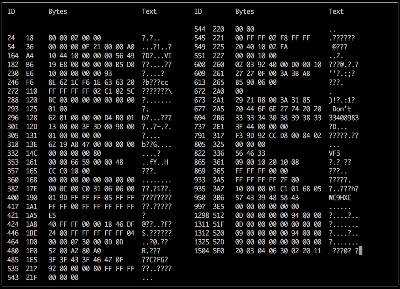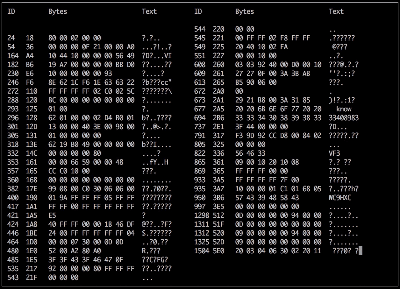 Adding the camera was the easiest part of the exercise when he found an after-market version specifically meant for his 207 model. The original non-graphical display had to make room for a new HDMI display and a fresh bezel, which cost him much more than the display. Besides displaying the camera image when reversing, the new display also needed to show all of the other entertainment system information. This couldn’t be obtained from the OBD-II port but the CAN bus looked promising, although he couldn’t find any details for his model initially. But with over 2.5 million of the 207’s on the road, it wasn’t long before [Alexandre] hit jackpot in a French University student project who used a 207 to study the CAN bus. The 207’s CAN bus system was sub-divided in to three separate buses and the “comfort” bus provided all the data he needed. To decode the CAN frames, he used an Arduino, a CAN bus shield and a python script to visualize the data, checking to see which frames changed when he performed certain functions — such as changing volume or putting the gear in reverse, for example.
Adding the camera was the easiest part of the exercise when he found an after-market version specifically meant for his 207 model. The original non-graphical display had to make room for a new HDMI display and a fresh bezel, which cost him much more than the display. Besides displaying the camera image when reversing, the new display also needed to show all of the other entertainment system information. This couldn’t be obtained from the OBD-II port but the CAN bus looked promising, although he couldn’t find any details for his model initially. But with over 2.5 million of the 207’s on the road, it wasn’t long before [Alexandre] hit jackpot in a French University student project who used a 207 to study the CAN bus. The 207’s CAN bus system was sub-divided in to three separate buses and the “comfort” bus provided all the data he needed. To decode the CAN frames, he used an Arduino, a CAN bus shield and a python script to visualize the data, checking to see which frames changed when he performed certain functions — such as changing volume or putting the gear in reverse, for example.