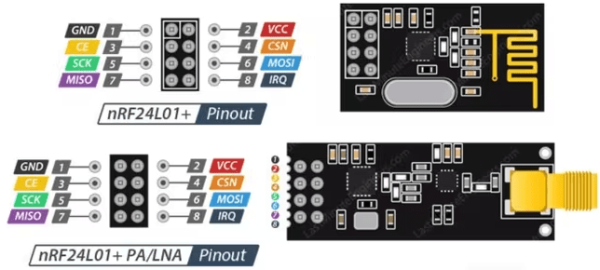
Despite the name, Bluetooth Low Energy (BLE) has very little to do with the original Bluetooth, other than its use of the same 2.4 GHz frequencies. This is where [Dmitry] got the idea to use a 2.4 GHz nRF24L01+ module to implement his very own BLE device, without the typical BLE chipset. This should be easy, since this popular IC supports GFSK modulation, 1 MHz channels and the 1 MBit data rate of BLE.
Despite of how simple BLE seems to implement, [Dmitry] quickly came across a range of issues due to limitations of the nRF24L01+. These include no support for a 24-bit CRC, a too sluggish PLL cycling for BLE’s frequency hopping, and as the coup de grâce, a lack for incoming data packets larger than 32 bytes — which destroyed any hope of accepting incoming connections.
Unperturbed, [Dmitry] set to work implementing what would work on this IC: broadcasting BLE packets. In the article he covers the entire code (in C) that allows the nRF24L01+ to send broadcast packets and any BLE-supporting device that’s listening to receive them. Admittedly not as useful as having a fully functional BLE stack, but good enough for broadcasting something like sensor data. It also raises the question of which alternative released in the intervening decade to the venerable nRF24L01+ might fill in the missing features, without making a dedicated BLE IC (or ESP32 variant) look more cost-effective.
It’s always a good day when a new project from [Dmitry] hits the tip line. We’ve previously covered his impressive efforts to add more RAM to the RP2040, and his business card that can boot Linux on an ATSAMD21.