One of the simplest ways of keeping a computer system secure is by using an air gap — that is, never actually connecting the system to the network. This can often include other peripherals like USB drives and other removable storage as well, so getting information to and from secure (or compromised) systems behind air gaps can often present a challenge. But assuming you have local access to the computer and your parts bin handy, these optical solutions from [Nikolay] can allow data transfer to or from such off-line computers.
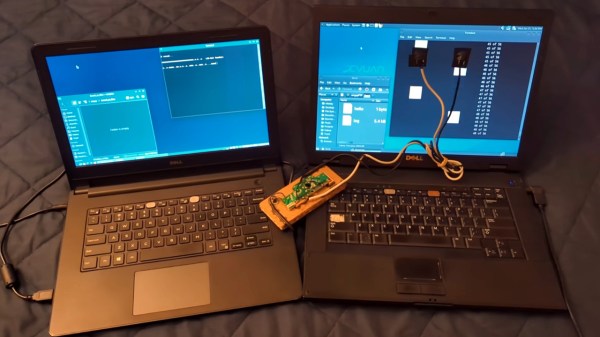
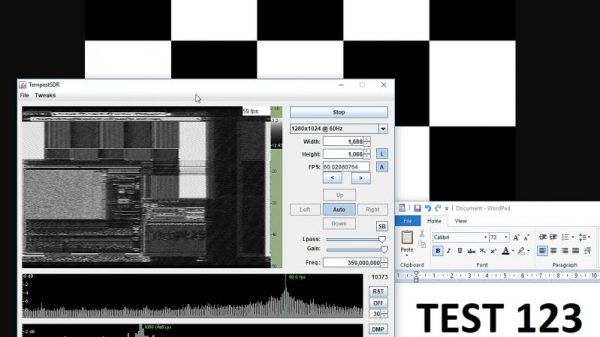
[Nikolay]’s specific use case for this project is to transfer small amounts of information to or from computers that may be compromised in some way, or computers that might otherwise be dangerous to connect to other equipment. There’s actually several methods described in the project, the first involves temporarily attaching a photoresistor to the computer’s screen which has been wired into the remains of a USB keyboard. A script running on the compromised machine translates data into a series of white and black squares. The sensors can detect these patterns much like playing Duck Hunt on an old CRT television and transmit the data across the air gap with reasonable certainty nothing harmful crossed with it.
Continue reading “Photoresistors Provide Air Gap Data Transfer, Slowly”