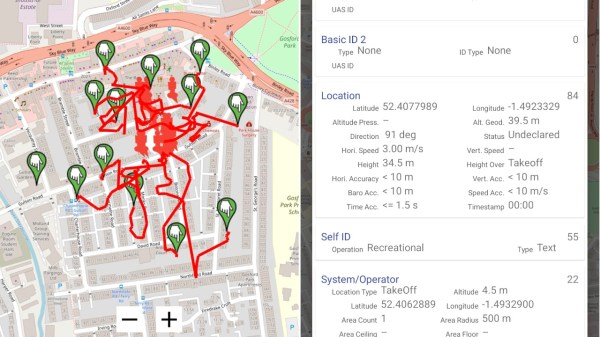
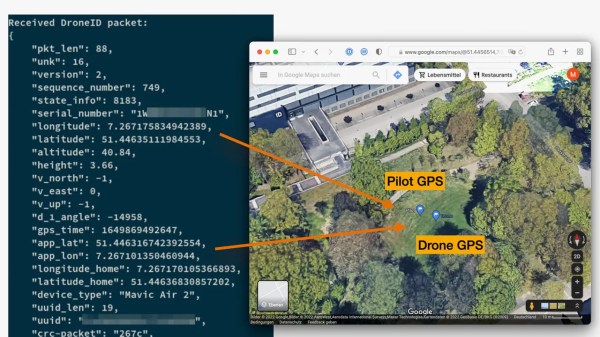
We have been alerted to a fun tool, a DJI DroneID spoofer software for ESP8266/ESP32 and some other popular MCUs. Last year, we’ve told you about DJI DroneID — a technology DJI added to their drones, which broadcasts data including the drone operator’s GPS position, which, in turn, appears to have resulted in Ukrainian casualties in the Ukraine war. The announcement tweet states that DJI has added mechanisms from downgrading firmware. Hence, the spoofer.
There’s no other hardware needed, well other than an ESP8266 or ESP32 devboard, anyway. After the break you can find a video tutorial from [Joshua Bardwell] that shows you how to upload the code using Arduino IDE, and even going through coordinate tweaks. If you ever reminisced about the concept of throwies and were wondering what kind of useful, well, there’s your answer: clone the Git repo, compile it, program some interesting coordinates in, and witness the imaginary drones fly.
All in all, we get a lovely addition to our shenanigan toolkits. Surely, someone could use a neural network to distinguish real drones from fake ones, but it’s nothing that can’t be solved with a bit of code. Looking for a less daring hack? Well, you can always add some automation to your DJI drone by poking at the RGB LED signals.
Continue reading “Can’t Disable DJI Drone ID? Spoof It With An ESP!”