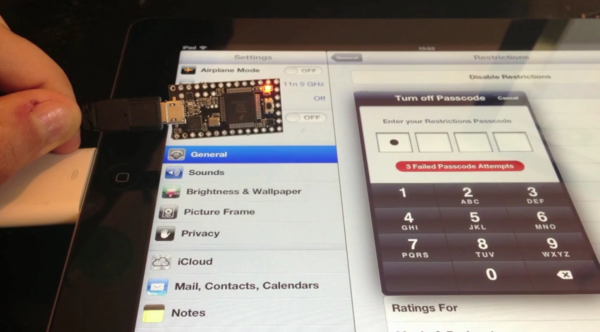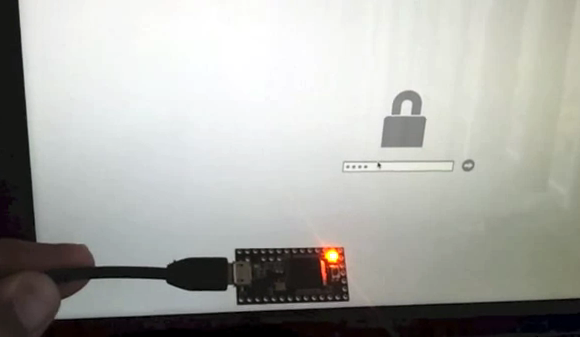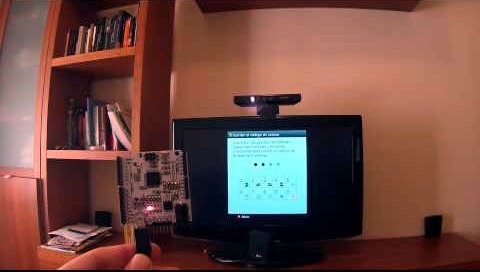
The Xbox 360 has the option of parental controls. It limits the rating of games which can be played on the system. [Oscar] didn’t really need to remove the lock-out. It was simply an interesting proof of concept for him. In the image above he’s holding up a Vinciduino board. It has an ATmega32u4 chip that can brute-force attack the Xbox 360 parental code (translated).
We’ve seen quite a few of these attacks lately. Like the recent iPad pin attack this uses the microcontroller to emulate a keyboard. As you can see in the video, [Oscar] first navigates the menu system to the unlock code screen, then plugs in his device.
The unlock screen calls for a four-digit numeric PIN. That’s a total of 10000 possible combinations. It looks pretty slow in the demo, but according to his calculations the worst case scenario would still break the code in less than seventeen hours. Apparently there’s no lock-out for the max number of wrong codes.
Continue reading “Brute Force Attack Xbox 360 Parental Controls”