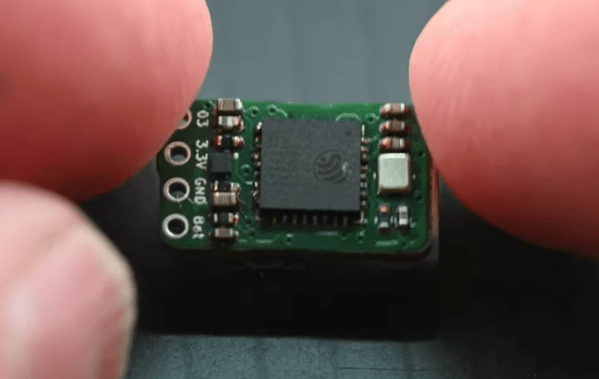
At its core, the ESP32 chip is not much more than an integrated circuit, a huge mass of transistors sealed inside an epoxy resin package with some leads. Of course, most of us won’t buy discrete ESP32 chips with no support circuitry since it’s typically easier and often not that much more expensive to get them paired with development boards of some type for easy access to things like USB and GPIO. But these tiny chips need little in the way of support to get up and running as [Paul] demonstrates with this tiny ESP32 board.
The project started as a challenge for [Paul] to build the smallest ESP32 that would still function. That means carving away nearly everything normally found accompanying one of these chips. There is no charging circuitry, only one of the GPIO pins is accessible, and it even foregoes the WiFi antennas which eliminates the major reason most people would reach for this chip in the first place. But at this form factor even without wireless capabilities it still blows other chips of this stature, like the ATtiny series, out of the water.
Even though [Paul] built it as a challenge, it goes a long way to demonstrate what’s really needed to get one of these chips up and running properly. And plenty of projects don’t need a ton of I/O or Wi-Fi either, so presuming these individual chips can be found cheaply and boards produced for various projects its an excellent way to minimize size and perhaps even power requirements. You can make these boards even smaller than a USB-A connector if you want to take this process even further, too.