Plasma speakers

Apparently if you run AC and DC currents through a welding torch flame you can use the resulting plasma as a loudspeaker. [Thanks Cody]
Power metering

The Google Power Meter API is no longer in development but that didn’t stop [Pyrofer] from finishing his metering hardware. It uses a reflectance sensor to read the meter instead of using clamp-based current sensing.
Music videos from inside the instrument

Filming from inside of a guitar creates the camera effect seen above which looks like the waveform you’d see on an oscilloscope. [Thanks Philleb]
Hidden messages in audio files
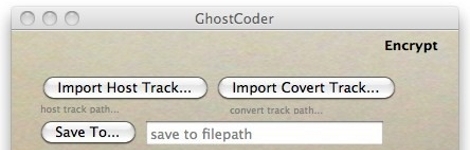
GhostCoder lets you encrypt and hide audio files within other audio files. The thought is, you can piggyback your own data into Torrents that are circling the interwebs.
2×4 Chair

If you’re skilled with a Skill saw you can make a chair out of one 2 by 4. You can see the pattern you’ll have to cut out from the board in the image above, wow!