Many a hacker has dug an old flash drive out of the bottom of a backpack, and peeled apart the damaged plastic case to look inside. More often then not, you’d expect to see some SMD chips on a PCB along with a few passives, an LED and a USB port. [Gough] found something else entirely, and documented it for the interested public.
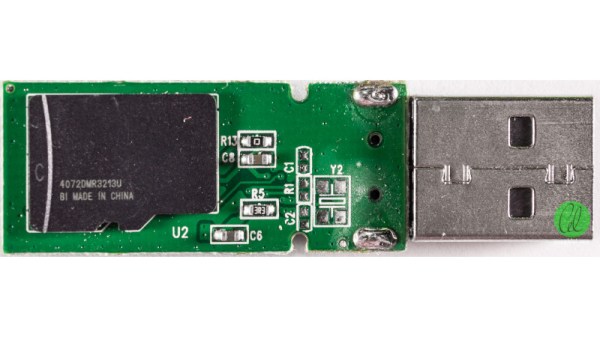
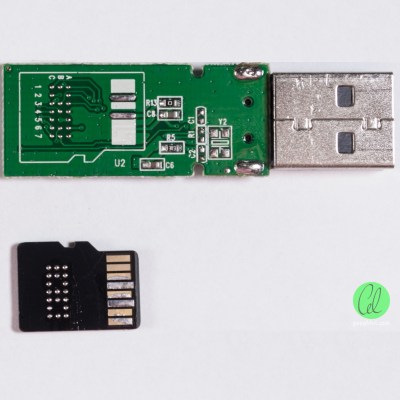 Inside the Comsol 8GB USB stick, [Gough] found an entire microSD card. One might be led to think this is a card reader and microSD masquerading as a normal flash drive, but the reality is far different. Instead, the drive contains a Flash memory controller which addresses the microSD card as raw NAND, through test points normally covered up on consumer-grade cards. The drive appears to be manufactured from factory second microSD cards that don’t pass the normal tests to be onsold to the public.
Inside the Comsol 8GB USB stick, [Gough] found an entire microSD card. One might be led to think this is a card reader and microSD masquerading as a normal flash drive, but the reality is far different. Instead, the drive contains a Flash memory controller which addresses the microSD card as raw NAND, through test points normally covered up on consumer-grade cards. The drive appears to be manufactured from factory second microSD cards that don’t pass the normal tests to be onsold to the public.
Armed with software obtained through spurious channels, [Gough] is able to dive deeper into the guts of the flash drive. The engineering tools allow the card to be optimised for capacity or speed, and different levels of error correction. It’s even possible to have the flash drive emulate a U3 CD ROM drive for OS installs and other purposes.
It’s a great dive into how USB drives work on a low level, and how the firmware and hardware work together. We’ve seen other flash drive hacks before too – like this simple recovery trick!