If you want to eavesdrop on GSM phone conversations or data, it pays to have deep pockets, because you’re going to need to listen to a wide frequency range. Or, you can just use two cheap RTL-SDR units and some clever syncing software. [Piotr Krysik] presented his work on budget GSM hacking at Camp++ in August 2016, and the video of the presentation just came online now (embedded below). The punchline is a method of listening to both the uplink and downlink channels for a pittance.
[Piotr] knows his GSM phone tech, studying it by day and hacking on a GnuRadio GSM decoder by night. His presentation bears this out, and is a great overview of GSM hacking from 2007 to the present. The impetus for Multi-RTL comes out of this work as well. Although it was possible to hack into a cheap phone or use a single RTL-SDR to receive GSM signals, eavesdropping on both the uplink and downlink channels was still out of reach, because it required more bandwidth than the cheap RTL-SDR had. More like the bandwidth of two cheap RTL-SDR modules.
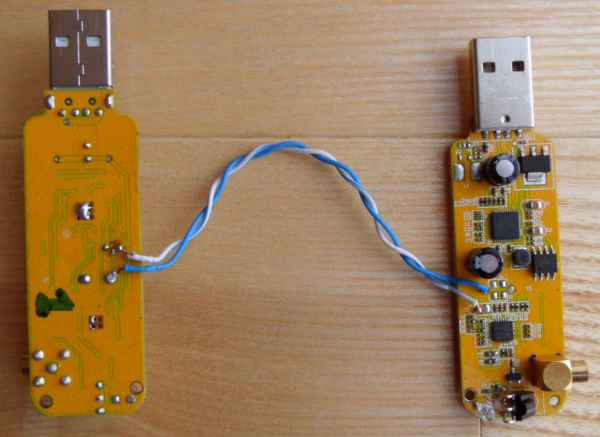
Getting two RTL-SDR modules to operate in phase is as easy as desoldering a crystal from one and slaving it to the other. Aligning the two absolutely in time required a very sweet hack. It turns out that the absolute timing is retained after a frequency switch, so both RTL-SDRs switch to the same channel, lock together on a single signal, and then switch back off, one to the uplink frequency and the other to the downlink. Multi-RTL is a GnuRadio source that takes care of this for you. Bam! Hundreds or thousands of dollar’s worth of gear replaced by commodity hardware you can buy anywhere for less than a fancy dinner. That’s a great hack, and a great presentation.
Continue reading “GSM Sniffing On A Budget With Multi-RTL”







 In his latest build he has produced
In his latest build he has produced 









