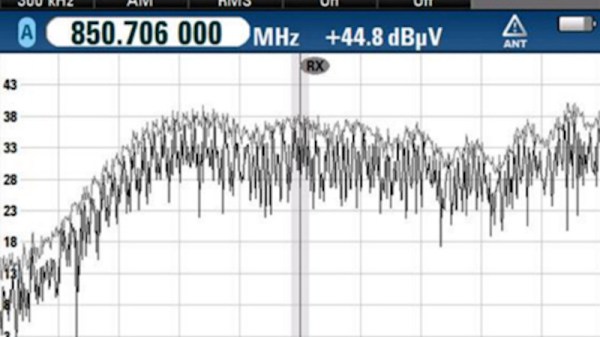
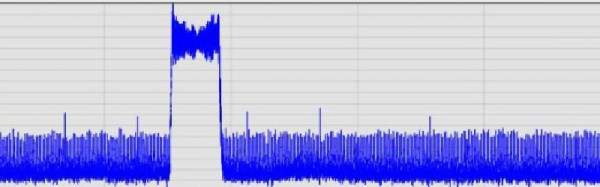
It used to be that having technical skills meant that fixing the computer problems of elderly relatives was a regular occurrence. Over the last few years this has been joined by another request on our time; friends with teenage children requesting help configuring their routers such that Internet access is curtailed when the kids should sleeping. In France a desperate parent took more extreme measures, buying a wideband frequency jammer to ensure les petits anges can’t waste the night away on social media sites through their cellular connections. It had the intended effect, but sadly it also interrupted cellular coverage over a wide area The French spectrum regulator ANFR sent in their investigators (French, Google Translate link), and now the unfortunate parent faces the prospect of up to 6 months imprisonment and €30,000 fine for owning and using a device that’s illegal in France.
A cursory search of everybody’s favourite online electronics bazaars will find plenty of these devices, so perhaps what’s surprising is that we don’t see more of these devices even if it’s not the first tale of interference tracking that we’ve seen. Judging by the strategies our friends with kids take, we’d suggest meanwhile to the unfortunate French person, that they simply equip their kids with restricted data plans.





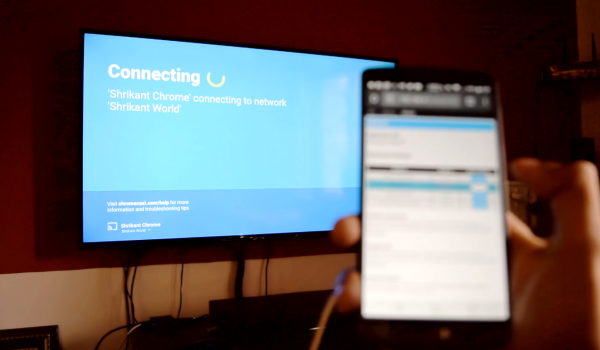
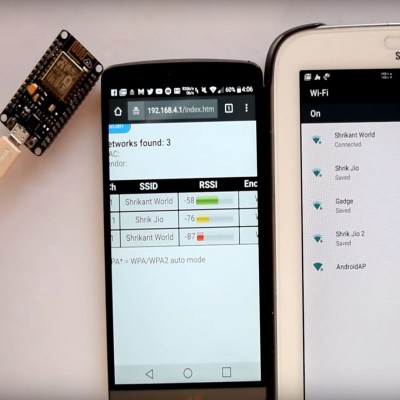 The jammer is an ESP8266 development board — running some additional custom code — accessed and controlled by a cell phone. From the interface, [Nimbalkar] is able to target a WiFi network and boot all the devices off the network by de-authenticating them. Another method is to flood the airspace with bogus SSIDs to make connecting to a valid network a drawn-out affair.
The jammer is an ESP8266 development board — running some additional custom code — accessed and controlled by a cell phone. From the interface, [Nimbalkar] is able to target a WiFi network and boot all the devices off the network by de-authenticating them. Another method is to flood the airspace with bogus SSIDs to make connecting to a valid network a drawn-out affair.








