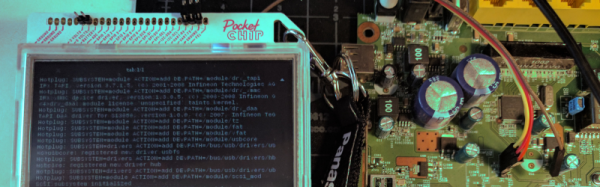
Conferences these days can be tricky places to be at – especially hardware and hacker cons. If you aren’t the one doing the hacking, then you can be sure your devices are being probed, pinged and possibly, hacked. It certainly isn’t the place to bring your precious laptop. Besides, as the day wears on and your feet start aching, regular laptops start feeling bigger and heavier. What you need is a burner laptop – one that is lightweight, cheap and that you don’t mind getting hacked. [dalmoz] wrote a short, to-the-point, tutorial on making use of PocketCHIP as a hardware-hacker’s best friend when it comes to UART connections. It’s also handy to use as a stand alone serial monitor for your projects without having to dedicate a USB port and screen real estate.
The PocketCHIP is a dock for the C.H.I.P. microcomputer and adds a LED backlit touchscreen display, QWERTY keyboard and LiPo battery in a lightweight, molded case. For $70, you get a 1 GHz ARM v7 processor, 512MB RAM, Mali 400 GPU, WiFi and Bluetooth. It’s light enough to be hung around your neck via its lanyard slot. And all of the GPIO pins are conveniently broken out, including the UART pins. Right now, it’s in the hands of Kickstarter backers, but the Next Thing Co website indicates availability sometime this month.
On the hardware side, all you need to do is add header pins to TX, RX and GND (and maybe 5 V and 3 V if required) on the PocketCHIP GPIO header and you’re good to go. On the software side, things are equally easy. The UART pins are meant to provide debug access to the CHIP itself and need to be released from internal duty. Once the UART port is identified, a single terminal command frees its status as a debugging interface. After that, use any terminal emulator – [dalmoz] recommends Minicom – and you’re all set. In the unlikely event that all you have is an Arduino lying around, [dalmoz] posted a simple sketch that can be used to make sure you have it working. Great hacking tip, ’cause it is as simple as it gets. If you’d like to know more about the CHIP project, check out its documentation and Github repository – it’s all open source.