The ESP32 is Espressif’s new wonder-chip, and one of the most interesting aspects of its development has been the almost entirely open-source development strategy that they’re taking. But the “almost” in almost entirely open is important — there are still some binary blobs in the system, and some of them are exactly where a hacker wouldn’t want them to be. Case in point: the low-level WiFi firmware.
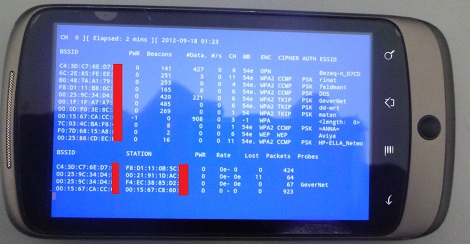
So that’s where [Jeija]’s reverse engineering work steps in. He’s managed to decode enough of a function called ieee80211_freedom_output to craft and send apparently arbitrary WiFi data and management frames, and to monitor them as well.
This ability is insanely useful for a WiFi device. With low-level access like this, one can implement custom protocols for mesh networking, low-bandwidth data transfers, or remove the requirement for handshaking entirely. One can also spam a system with so many fake SSIDs that it crashes, deauth everyone, or generally cause mayhem. Snoop on your neighbors, or build something new and cool: with great power comes great responsibility.
Anyway, we reported on [Jeija]’s long distance hack and the post may have read like it was all about the antenna, but that vastly underestimates the role played by this firmware reverse-engineering hack. Indeed, we’re so stoked about the hack that we thought it was worth reiterating: the ESP32 is now a WiFi hacker’s dream.


 Enter the
Enter the