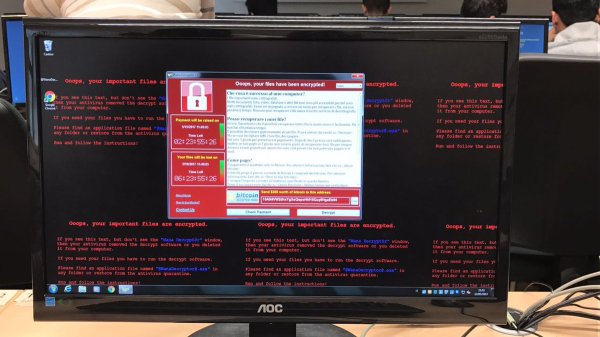
A massive ransomware attack is currently under way. It was first widely reported having crippled the UK hospital system, but has since spread to numerous other systems throughout the world including FedEx in the US, the Russian Interior Ministry, and telecommunications firms in Spain and Russia.
The virus is known by names WannaCrypt, WannaCry, and a few other variants. It spreads using the ExternalBlue exploit in unpatched Windows machines older than version 10. The tools used to pull off this attack were likely from an NSA toolset leaked by the Shadow Brokers.
So far the strongest resource for technical information that we’ve found is this factsheet hosted on GitHub.
NHS Services at a Standstill in the UK
NHS services across England and Scotland have been hit by the ransomware attack, crippling multiple hospitals and doctor’s practices. The UK has universal healthcare — the National Health Service — covering Doctors, Hospitals and generally everything medical related is free at the point of service. but today they have had to turn away patients and cancel consultations.
NHS is unable to access medical records of patients unless they pay £230 ($300) in bitcoin for infected machines. There is no evidence patient data has been compromised, NHS Digital has said. The BBC has stated that up to 39 NHS organisations and some GP practices have been affected.
The National Cyber Security Centre (NCSC) was “working closely” with the NHS and that they will protect patient safety. We are aware that a number of NHS organisations have reported that they have suffered from a ransomware attack.
-Prime Minister Theresa May
Infected Systems Throughout the World
Computers in regions across the globe have been under attack today, including Telefonica (O2 in the UK), with at least 45,000 computers compromised in Russia, Ukraine, India, and Taiwan alone. There’s no indication of who is behind the attack yet.
The ransomware’s code takes advantage of an exploit called EternalBlue, made public in April by Shadow Brokers which was patched by Microsoft in March, It comes as a shock that an organisation the size of the NHS seem not to have kept their computers updated. This is perhaps just a taster of what is to come in the future as cyber crime and warfare become more and more commonplace.
[Ransomware screenshots via @UID_]