In retrocomputing circles, it’s often the case that the weirder and rarer the machine, the more likely it is to attract attention. And machines don’t get much weirder than the DEC Rainbow 100-B, sporting as it does both Z80 and 8088 microprocessors and usable as either a VT100 terminal or as a PC with either CP/M or MS-DOS. But hey — at least it got the plain beige box look right.
Weird or not, all computers have at least a few things in common, a fact which helped [Dr. Joshua Reichard] home in on the problem with a Rainbow that was dead on arrival. After a full recapping — a prudent move given the four decades since the machine was manufactured — the machine failed to show any signs of life. The usual low-hanging diagnostic fruit didn’t provide much help, as both the Z80 and 8088 CPUs seemed to be fine. It was then that [Joshua] decided to look at the heartbeat of the machine — the 24-ish MHz clock shared between the two processors — and found that it was flatlined.
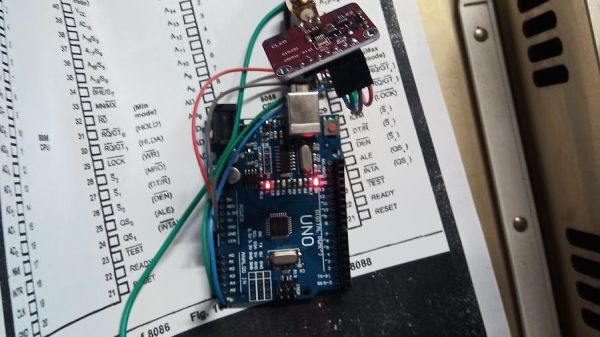
Unwilling to wait for a replacement, [Joshua] cobbled together a temporary clock from an Arduino Uno and an Si5351 clock generator. He connected the output of the card to the main board, whipped up a little code to generate the right frequency, and the nearly departed machine sprang back to life. [Dr. Reichard] characterizes this as a “defibrillation” of the Rainbow, and while one hates to argue with a doctor — OK, that’s a lie; we push back on doctors all the time — we’d say the closer medical analogy is that of fitting a temporary pacemaker while waiting for a suitable donor for a transplant.
This is the second recent appearance of the Rainbow on these pages — [David] over at Usagi Electric has been working on the graphics on his Rainbow lately.

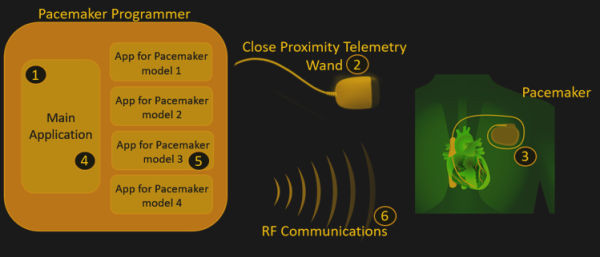
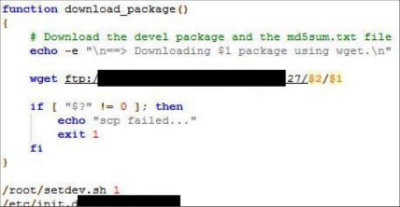 The programmers’ firmware update procedures were also flawed, with hard-coded credentials being very common. This allows an attacker to setup their own authentication server and upload their own firmware to the home monitoring kit. Due to the nature of the hack, the researchers are not disclosing to the public which manufacturers or devices are at fault and have redacted some information until these medical device companies can get their house in order and fix these problems.
The programmers’ firmware update procedures were also flawed, with hard-coded credentials being very common. This allows an attacker to setup their own authentication server and upload their own firmware to the home monitoring kit. Due to the nature of the hack, the researchers are not disclosing to the public which manufacturers or devices are at fault and have redacted some information until these medical device companies can get their house in order and fix these problems.