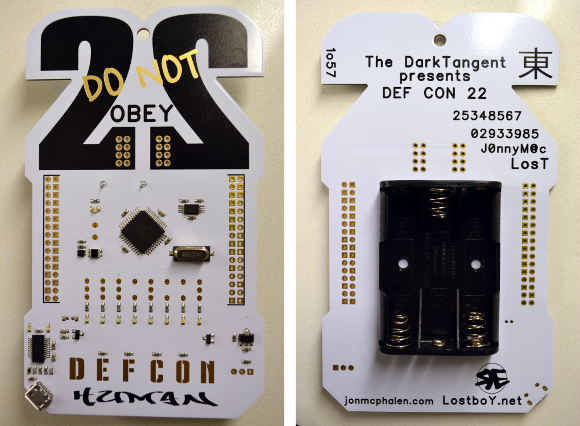
If you go to DEFCON next year (and you should), prepare for extreme sleep deprivation. If you’re not sleep deprived you’re doing it wrong. This was the state in which we ran into [LosT] and [J0nnyM@c], the brains behind the DEFCON 22 badge and all of the twisted tricks that torture people trying to solve the badge throughout the weekend. They were popular guys but wait around until late into the night and the throngs of hint-seekers subside just a bit.
Plans, within plans, within plans are included in the “crypto” which [LosT] talks about in the interview above. We were wondering how hard it is to produce a badge that is not only electrically perfect, but follows the planned challenge to a ‘T’. This includes things like holding off soldering mask from some pads, and different ones on a different version of the badge. Turns out that you just do as well as you can and then alter the puzzle to match the hardware.
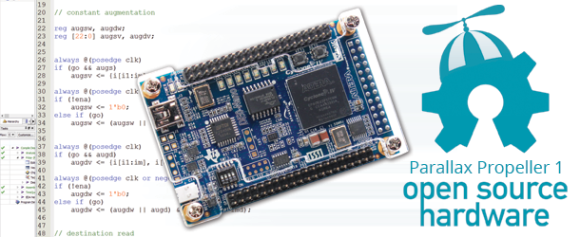
Speaking of hardware. A late snafu in the production threw the two into a frenzy of redesign. Unable to use the planned chip architecture, [J0nnyM@c] stepped up to transition the badges over to Propeller P8X32a chips, leveraging a relationship with Parallax to ensure they hardware could be manufactured in time for the conference.
If you haven’t put it together yet, this is that same chip that Parallax just made Open Source. The announcement was timed to coincide with DEFCON.