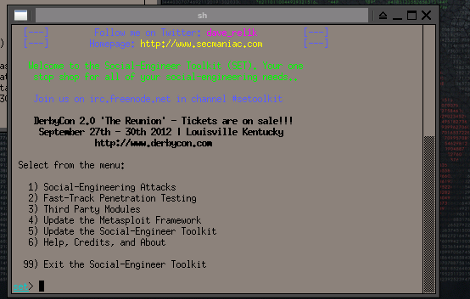
Plug in the power and Ethernet and this Raspberry Pi board will automatically collect Windows hashes from computers on the network. With a couple of RPi boards on hand [Travis] was searching for more hacks to try with them. This made a great little test to see how the board performs with the well established attack.
To start he booted into the standard Raspbian distribution. From there he loads the Metasploit framework which brings most of the necessary tools into play. It uses the Web Proxy Auto-Discovery Protocol (WPAD) to request hashes from any Windows machines listening on the network. Some version of the OS respond with LM hashes, others don’t. The importance of this and the particulars of using rainbow tables to crack the hashes is explained in this article on the subject.
We wouldn’t mind having a little hardware hack that adds a couple of LEDs to the GPIO header so you know when the RPi is done collecting the data.

 What you see here is a Raspberry Pi shoehorned into a power strip. The idea is to
What you see here is a Raspberry Pi shoehorned into a power strip. The idea is to