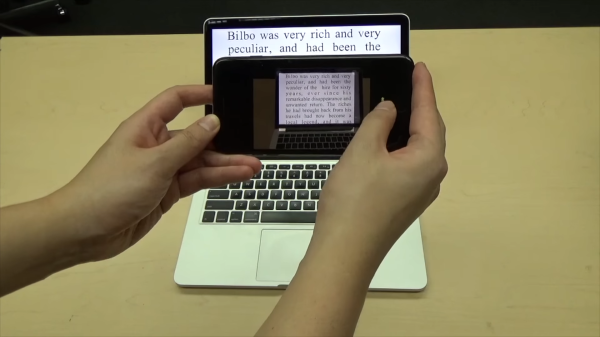
Getting bounced to a website by scanning a QR code is no longer an exciting feat of technology, but what if you scanned the ingredient list on your granola bar and it went to the company’s page for that specific flavor, sans the matrix code?
Bright minds at the Columbia University in the City of New York have “perturbed” ordinary font characters so the average human eye won’t pick up the changes. Even ordinary OCR won’t miss a beat when it looks at a passage with a hidden message. After all, these “perturbed” glyphs are like a perfectly legible character viewed through a drop of water. When a camera is looking for these secret messages, those minor tweaks speak volumes.
The system is diabolically simple. Each character can be distorted according to an algorithm and a second variable. Changing that second variable is like twisting a distorted lens, or a water drop but the afterimage can be decoded and the variable extracted. This kind of encoding can survive a trip to the printer, unlike a purely digital hidden message.
Hidden messages like these are not limited to passing notes, metadata can be attached to any text and extracted when necessary. Literature could include notes without taking up page space so teachers could include helpful notes and a cell phone could be like an x-ray machine to see what the teacher wants to show. For example, you could define what “crypto” actually means.