Sometimes you just have parts lying around and want to make something out of them. [Tymkrs] had a robot paper cutter, so naturally they made punch cards. But then, of course, they needed a punch card reader, so they made one of those too. All with stuff lying around the shop.
The Silhouette Portrait paper cutter is meant for scrapbooking, but what evokes memories of the past more than punchcards? To cut out their data, rather than cute kittens or flowers, they wrote some custom code to turn ASCII characters into rows of dots. And the cards are done — you just have to clean up the holes that didn’t completely cut. These are infamously known as hanging chads.
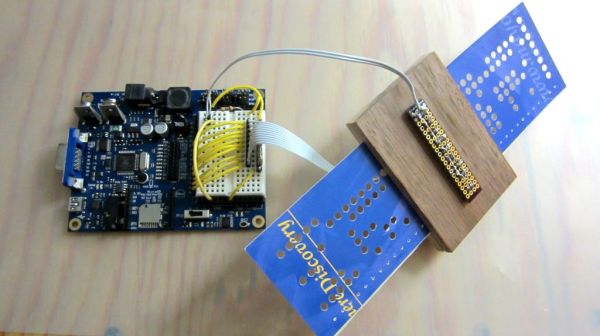
The reader is made up of a block of wood, with a gap for the cards and perpendicular holes drilled for LEDs and photoresistors. This is cabled to a Propeller dev board with some simple firmware. We would have used photodiodes or phototransistors, because that’s what’s in our junk box (and because they have faster reaction time), but when you’ve got lemons, make lemonade.
OK, now that you’ve got a punch card reader and writer, what do you do with it? Password storage comes to mind.
Continue reading “DIY Punch Card System Despite Hanging Chads”