Battlelines are being drawn in Canada over the lowly Flipper Zero, a device seen by some as an existential threat to motor vehicle owners across the Great White North. The story started a month or so ago, when someone in the government floated the idea of banning devices that could be “used to steal vehicles by copying the wireless signals for remote keyless entry.” The Flipper Zero was singled out as an example of such a nefarious device, even though relatively few vehicles on the road today can be boosted using the simple replay attack that a Flipper is capable of, and the ones that are vulnerable to this attack aren’t all that desirable — apologies to the 1993 Camry, of course. With that threat hanging in the air, the folks over at Flipper Devices started a Change.org petition to educate people about the misperceptions surrounding the Flipper Zero’s capabilities, and to urge the Canadian government to reconsider their position on devices intended to explore the RF spectrum. That last bit is important, since transmit-capable SDR devices like the HackRF could fall afoul of a broad interpretation of the proposed ban; heck, even a receive-only SDR dongle might be construed as a restricted device. We’re generally not much for petitions, but this case might represent an exception. “First they came for the Flipper Zero, but I did nothing because I don’t have a Flipper Zero…”
reverse engineering361 Articles
Generator Control Panel Unlocked With Reverse Engineering Heroics
Scoring an interesting bit of old gear on the second-hand market is always a bit of a thrill — right up to the point where you realize the previous owner set some kind of security code on it. Then it becomes a whole big thing to figure out, to the point of blunting the dopamine hit you got from the original purchase.
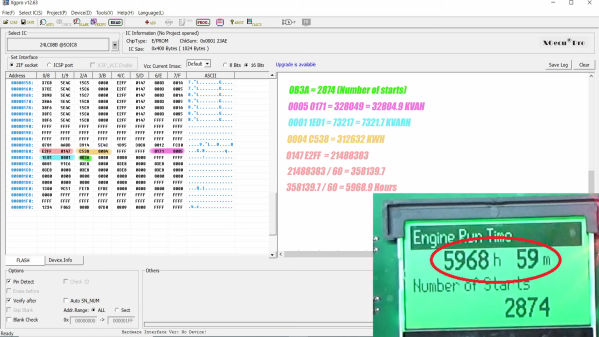
Fear not, though, because there’s dopamine aplenty if you can copy what [Buy it Fix it] did to decode the PIN on a used generator control panel. The panel appears to be from a marine generator, and while it powered up fine, the menu used to change the generator’s configuration options is locked by a four-digit PIN. The manufacturer will reset it, but that requires sending it back and paying a fee, probably considerable given the industrial nature of the gear.
Instead of paying up, [Buy it Fix it] decided to look for a memory chip that might store the PIN. He identified a likely suspect, a 24LC08B 8-Kb serial EEPROM, and popped it off to read its contents. Nothing was immediately obvious, but blanking the chip and reinstalling it cleared the PIN, so he at least knew it was stored on the chip. Many rounds of soldering and desoldering the chip followed, blanking out small sections of memory each time until the PIN was located. The video below edits out a lot of the rework, but gives the overall gist of the hack.
To be honest, we’re not sure if the amount of work [Buy it Fix it] put into this was less than taking a couple of hours to punch in PINs and brute-force it. Then again, if he hadn’t done the reverse engineering he wouldn’t have stumbled upon where the generator parameters like running time and power figures were stored. And it’s not really his style, either; we’ve seen him perform similar heroics on everything from tractors to solar inverters, after all.
Continue reading “Generator Control Panel Unlocked With Reverse Engineering Heroics”
Extracting SecOC Keys From A 2021 Toyota RAV4 Prime
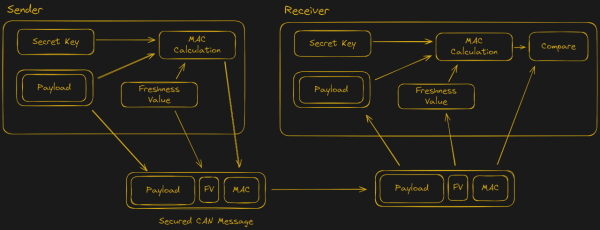
With the recently introduced SecOC (Secure Onboard Communication) standard, car manufacturers seek to make the CAN bus networks that form the backbone of modern day cars more secure. This standard adds a MAC (message authentication code) to the CAN messages, which can be used to validate that these messages come from a genuine part of the car, and not from a car thief or some third-party peripheral.
To check that it isn’t possible to circumvent SecOC, [Willem Melching] and [Greg Hogan] got their hands on the power steering (EPS) unit of a Toyota RAV4 Prime, as one of the first cars to implement this new security standard.
As noted by [Willem], the ultimate goal is to be able to run the open source driver assistance system openpilot on these SecOC-enabled cars, which would require either breaking SecOC, or following the official method of ‘rekeying’ the SecOC gateway.
After dumping the firmware of the EPS Renesas RH850/P1M-E MCU via a voltage fault injection, the AES-based encryption routines were identified, but no easy exploits found in the main application. This left the bootloader as the next target.
Ultimately they managed to reverse-engineer the bootloader to determine how the update procedure works, which enabled them to upload shellcode. This script then enabled them to extract the SecOC keys from RAM and send these over the CAN bus. With these keys the path is thus opened to allow any device to generate CAN messages with valid SecOC MACs, effectively breaking encryption. Naturally, there are many caveats with this discovery.
Continue reading “Extracting SecOC Keys From A 2021 Toyota RAV4 Prime”
Mapping The Nintendo Switch PCB
As electronics have advanced, they’ve not only gotten more powerful but smaller as well. This size is great for portability and speed but can make things like repair more inaccessible to those of us with only a simple soldering iron. Even simply figuring out what modern PCBs do is beyond most of our abilities due to the shrinking sizes. Thankfully, however, [μSoldering] has spent their career around state-of-the-art soldering equipment working on intricate PCBs with tiny surface-mount components and was just the person to document a complete netlist of the Nintendo Switch through meticulous testing, a special camera, and the use of a lot of very small wires.
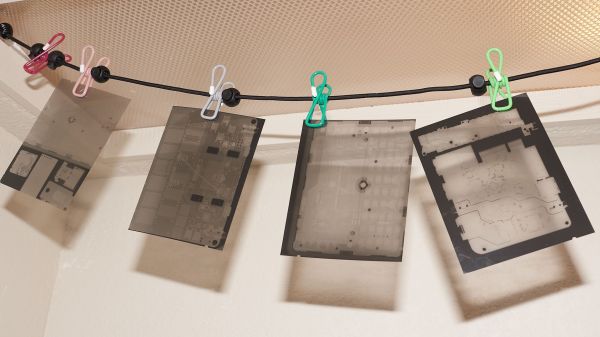
 The first part of reverse-engineering the Switch is to generate images of the PCBs. These images are taken at an astonishing 6,000 PPI and as a result are incredibly large files. But with that level of detail the process starts to come together. A special piece of software is used from there that allows point-and-click on the images to start to piece the puzzle together, and with an idea of where everything goes the build moves into the physical world.
The first part of reverse-engineering the Switch is to generate images of the PCBs. These images are taken at an astonishing 6,000 PPI and as a result are incredibly large files. But with that level of detail the process starts to come together. A special piece of software is used from there that allows point-and-click on the images to start to piece the puzzle together, and with an idea of where everything goes the build moves into the physical world.
[μSoldering] removes all of the parts on the PCBs with hot air and then meticulously wires them back up using a custom PCB that allows each connection to be wired up and checked one-by-one. With everything working the way it is meant to, a completed netlist documenting every single connection on the Switch hardware can finally be assembled.
The final documentation includes over two thousand photos and almost as many individual wires with over 30,000 solder joints. It’s an impressive body of work that [μSoldering] hopes will help others working with this hardware while at the same time keeping their specialized skills up-to-date. We also have fairly extensive documentation about some of the Switch’s on-board chips as well, further expanding our body of knowledge on how these gaming consoles work and how they’re put together.
Hands On: Bus Pirate 5
If you’ve been involved with electronics and hardware hacking for awhile, there’s an excellent chance you’ve heard of the Bus Pirate. First introduced on the pages of Hackaday back in 2008 by creator Ian Lesnet, the open hardware multi-tool was designed not only as away to easily tap into a wide array of communication protocols, but to provide various functions that would be useful during hardware development or reverse engineering. The Bus Pirate could talk to your I2C and SPI devices, while also being able to measure frequencies, check voltages, program chips, and even function as a logic analyzer or oscilloscope.
The Bus Pirate provided an incredible number of tools at a hobbyist-friendly price, and it wasn’t long before the device became so popular that it achieved a milestone which only a few hardware hacking gadgets can boast: its sales started to get undercut by cheap overseas clones. Of course, as an open hardware device, this wasn’t really a problem. If other companies wanted to crank out cheap Bus Pirates, that’s fine. It freed Ian up to research a next-generation version of the device.
But it turns out that was easier said than done. It’s around this point that the Bus Pirate enters what might be considered its Duke Nukem Forever phase. It took 15 years to release the sequel to 1996’s Duke Nukem 3D because the state-of-the-art in video games kept changing, and the developers didn’t want to be behind the curve. Similarly, Ian and his team spent years developing and redeveloping versions of the Bus Pirate that utilized different hardware platforms, such as the STM32 and ICE40 FPGA. But each time, there would be problems sourcing components, or something newer and more interesting would be released.
But then in 2021 the Raspberry Pi Pico hit the scene, and soon after, the bare RP2040 chip. Not only were the vast I/O capabilities of the new microcontroller a perfect fit for the Bus Pirate, but the chip was cheap and widely available. Finally, after years of false starts, the Bus Pirate 5 was born.
I was able to grab one of the first all-new Bus Pirates off the production line in January, and have been spending the last week or so playing around with it. While there’s definitely room for improvement on the software side of things, the hardware is extremely promising, and I’m very excited to be see how this new chapter in the Bus Pirate story plays out.
Reviving A Sensorless X-Ray Cabinet With Analog Film
In the same way that a doctor often needs to take a non-destructive look inside a patient to diagnose a problem, those who seek to reverse engineer electronic systems can greatly benefit from the power of X-ray vision. The trouble is that X-ray cabinets designed for electronics are hideously expensive, even on the secondary market. Unless, of course, their sensors are kaput, in which case they’re not of much use. Or are they?
[Aleksandar Nikolic] and [Travis Goodspeed] strongly disagree, to the point that they dedicated a lot of work documenting how they capture X-ray images on plain old analog film. Of course, this is nothing new — [Wilhelm Konrad Roentgen] showed that photographic emulsions are sensitive to “X-light” all the way back in the 1890s, and film was the de facto image sensor for radiography up until the turn of this century. But CMOS sensors have muscled their way into film’s turf, to the point where traditional silver nitrate emulsions and wet processing of radiographic films, clinical and otherwise, are nearly things of the past. Continue reading “Reviving A Sensorless X-Ray Cabinet With Analog Film”
Bus Pirate 5 Now Shipping
It’s happened to all of us at one time or another. There’s some component sitting on the bench, say an I2C sensor, a new display, or maybe a flash chip, and you want to poke around with it. So you get out the breadboard, wire it to a microcontroller, write some code, flash it…you get the idea. Frankly, it’s all kind of a hassle. Which is why [Ian Lesnet] created the Bus Pirate: a USB multi-tool designed to get you up and running with a new piece of hardware as quickly as possible.
Now, after years of development, the Bus Pirate 5 is available for purchase. Completely redesigned to take advantage of the impressive I/O capabilities of the RP2040, the new Bus Pirate also features a 240 x 320 IPS LCD that can show real-time voltage data and pin assignments. But despite the new display, and the bevy of RGB LEDs lurking under the injection molded enclosure, the primary interface for the device remains the VT100 terminal interface — now with the addition of a color status bar running along the bottom.