As home automation grows more and more popular by the day, the free market is taking notice and working to supply the demand. The Wink Hub is a part of this current trend. It’s a device that allows many of your wireless devices to talk to one another. Things like lights, thermostats, door locks, garage doors…and many other devices can all connect to the hub. Typically, you use a program on your phone or tablet to control these devices. But because this is a closed source gadget, it can’t connect to everything, until now. A hacker was not only able to root the device, but he also gained the ability to connect to devices it was never designed to connect to.
[Michael] was able to get root and take control of some of the devices used with one of Wink’s main competitors – SmartThings. The process is not for the faint of heart and requires at least a yellow belt in Linux-Fu. [Michael] points out that you should use a Wink Hub that you don’t care about as the possibility of bricking it is there if something goes wrong.
We’ve seen a few instances of rooting the Wink and are happy to see these hacks maturing. It’s a shame the thing is locked down since the multiple radios make the hardware capable of being a great cross-platform hub. For legacy and better user experience, cross-platform operation is paramount. The industry isn’t moving in that direction… Phillips recently removed support for devices outside the Hue family. But the community wants this functionality and their push back led to a hasty reversal of Phillips’ changes. Hackers like [Michael] are showing what your home could be like if connected devices were free to interact with one another.



 The specs I’m quoting come from the LG Optimus Exceed 2, which is currently available from Amazon in the USA for $20. The same package has been available for as little as $10 from retail stores in recent weeks. The Exceed 2 is just one of several low-cost Android prepaid phones on the market now, and undoubtedly the list will change. How to keep up with the current deals? We found an unlikely place. Perk farmers. Perk is one of those “We pay you to watch advertisements” companies. We’re sure some people actually watch the ads, but most set up “farms” of drone phones which churn through the videos. The drones earn the farmer points which can be converted to cash. How does this all help us? In order to handle streaming video, Perk farmers want the most powerful phones they can get for the lowest investment. Subreddits like
The specs I’m quoting come from the LG Optimus Exceed 2, which is currently available from Amazon in the USA for $20. The same package has been available for as little as $10 from retail stores in recent weeks. The Exceed 2 is just one of several low-cost Android prepaid phones on the market now, and undoubtedly the list will change. How to keep up with the current deals? We found an unlikely place. Perk farmers. Perk is one of those “We pay you to watch advertisements” companies. We’re sure some people actually watch the ads, but most set up “farms” of drone phones which churn through the videos. The drones earn the farmer points which can be converted to cash. How does this all help us? In order to handle streaming video, Perk farmers want the most powerful phones they can get for the lowest investment. Subreddits like 

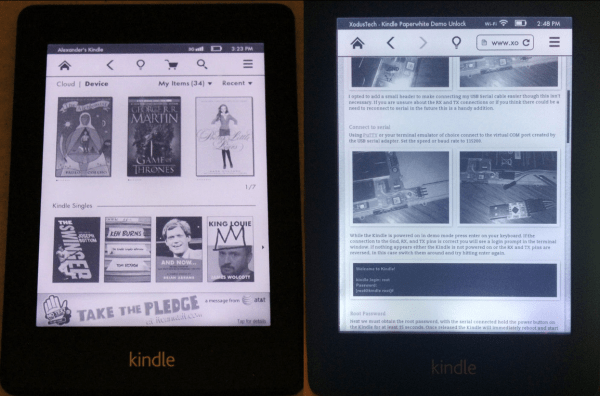
 The first step was to crack open the case and locate the serial port. [WarriorRocker] soldered a small three pin header to the pads to make it easier to work on his device as needed. He then connected the Kindle to his PC using a small serial to USB adapter. Pulling up the command prompt was as simple as running Putty and connecting to the correct COM port. If the wires are hooked up correctly, then it just takes a press of the enter key to pull up the login prompt.
The first step was to crack open the case and locate the serial port. [WarriorRocker] soldered a small three pin header to the pads to make it easier to work on his device as needed. He then connected the Kindle to his PC using a small serial to USB adapter. Pulling up the command prompt was as simple as running Putty and connecting to the correct COM port. If the wires are hooked up correctly, then it just takes a press of the enter key to pull up the login prompt.









