As Tom Nardi mentioned in this week’s podcast, the Northeast US is pretty apocalyptically socked in with smoke from wildfires in Canada. It’s what we here in Idaho call “August,” so we have plenty of sympathy for what they’re going through out there. People are turning to technology to ease their breathing burden, with reports that Tesla drivers are activating the “Bioweapon Defense Mode” of their car’s HVAC system. We had no idea this mode existed, honestly, and it sounds pretty cool — the cabin air system apparently shuts off outside air intake and runs the fan at full speed to keep the cabin under positive pressure, forcing particulates — or, you know, anthrax — to stay outside. We understand there’s a HEPA filter in the mix too, which probably does a nice job of cleaning up the air in the cabin. It’s a clever idea, and hats off to Tesla for including this mode, although perhaps the name is a little silly. Here’s hoping it’s not one of those subscription services that can get turned off at a moment’s notice, though.
spying6 Articles
A TEMPEST In A Dongle
If a couple of generations of spy movies have taught us anything, it’s that secret agents get the best toys. And although it may not be as cool as a radar-equipped Aston Martin or a wire-flying rig for impossible vault heists, this DIY TEMPEST system lets you snoop on computers using secondary RF emissions.
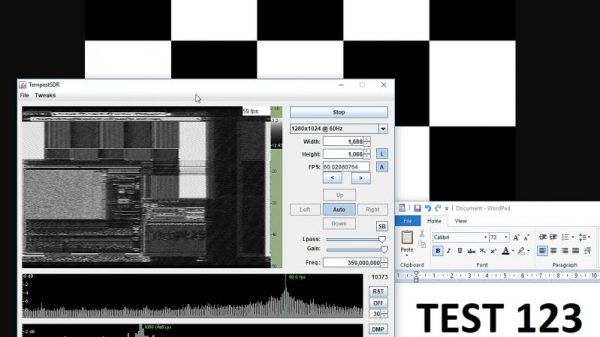
If the term TEMPEST sounds familiar, it’s because we’ve covered it before. [Elliot Williams] gave an introduction to the many modalities that fall under the TEMPEST umbrella, the US National Security Agency’s catch-all codename for bridging air gaps by monitoring the unintended RF, light, or even audio emissions of computers. And more recently, [Brian Benchoff] discussed a TEMPEST hack that avoided the need for thousands of dollars of RF gear, reducing the rig down to an SDR dongle and a simple antenna. There’s even an app for that now: TempestSDR, a multiplatform Java app that lets you screen scrape a monitor based on its RF signature. Trouble is, getting the app running on Windows machines has been a challenge, but RTL-SDR.com reader [flatfishfly] solved some of the major problems and kindly shared the magic. The video below shows TempestSDR results; it’s clear that high-contrast images at easiest to snoop on, but it shows that a $20 dongle and some open-source software can bridge an air gap. Makes you wonder what’s possible with deeper pockets.
RF sniffing is only one of many ways to exfiltrate data from an air-gapped system. From power cords to security cameras, there seems to be no end to the ways to breach systems.
Books You Should Read: The Cuckoo’s Egg
The mid-1980s were a time of drastic change. In the United States, the Reagan era was winding down, the Cold War was heating up, and the IBM PC was the newest of newnesses. The comparatively few wires stitching together the larger university research centers around the world pulsed with a new heartbeat — the Internet Protocol (IP) — and while the World Wide Web was still a decade or so away, The Internet was a real place for a growing number of computer-savvy explorers and adventurers, ready to set sail on the virtual sea to explore and exploit this new frontier.
In 1986, having recently lost his research grant, astronomer Clifford Stoll was made a computer system admin with the wave of a hand by the management of Lawrence Berkeley Laboratory’s physics department. Commanded to go forth and administer, Stoll dove into what appeared to be a simple task for his first day on the job: investigating a 75-cent error in the computer account time charges. Little did he know that this six-bit overcharge would take over his life for the next six months and have this self-proclaimed Berkeley hippie rubbing shoulders with the FBI, the CIA, the NSA, and the German Bundeskriminalamt, all in pursuit of the source: a nest of black-hat hackers and a tangled web of international espionage.
Theremin’s Bug: How The Soviet Union Spied On The US Embassy For 7 Years
The man leaned over his creation, carefully assembling the tiny pieces. This was the hardest part, placing a thin silver plated diaphragm over the internal chamber. The diaphragm had to be strong enough to support itself, yet flexible enough to be affected by the slightest sound. One false move, and the device would be ruined. To fail meant a return to the road work detail, quite possibly a death sentence. Finally, the job was done. The man leaned back to admire his work.
The man in this semi-fictional vignette was Lev Sergeyevich Termen, better known in the western world as Léon Theremin. You know Theremin for the musical instrument which bears his name. In the spy business though, he is known as the creator of one of the most successful clandestine listening devices ever used against the American government.
Continue reading “Theremin’s Bug: How The Soviet Union Spied On The US Embassy For 7 Years”
IPhone Jailbreak Hackers Await $1M Bounty
According to Motherboard, some unspecified (software) hacker just won a $1 million bounty for an iPhone exploit. But this is no ordinary there’s-a-glitch-in-your-Javascript bug bounty.
On September 21, “Premium” 0day startup Zerodium put out a call for a chain of exploits, starting with a browser, that enables the phone to be remotely jailbroken and arbitrary applications to be installed with root / administrator permissions. In short, a complete remote takeover of the phone. And they offered $1 million. A little over a month later, it looks like they’ve got their first claim. The hack has yet to be verified and the payout is actually made.
But we have little doubt that the hack, if it’s actually been done, is worth the money. The NSA alone has a $25 million annual budget for buying 0days and usually spends that money on much smaller bits and bobs. This hack, if it works, is huge. And the NSA isn’t the only agency that’s interested in spying on folks with iPhones.
Indeed, by bringing something like this out into the open, Zerodium is creating a bidding war among (presumably) adversarial parties. We’re not sure about the ethics of all this (OK, it’s downright shady) but it’s not currently illegal and by pitting various spy agencies (presumably) against each other, they’re almost sure to get their $1 million back with some cream on top.
We’ve seen a lot of bug bounty programs out there. Tossing “firmname bug bounty” into a search engine of your choice will probably come up with a hit for most firmnames. A notable exception in Silicon Valley? Apple. They let you do their debugging work for free. How long this will last is anyone’s guess, but if this Zerodium deal ends up being for real, it looks like they’re severely underpaying.
And if you’re working on your own iPhone remote exploits, don’t be discouraged. Zerodium still claims to have money for two more $1 million payouts. (And with that your humble author shrugs his shoulders and turns the soldering iron back on.)
DIY Wireless Keylogger Makes You Feel Like James Bond (In Your Own Little World)
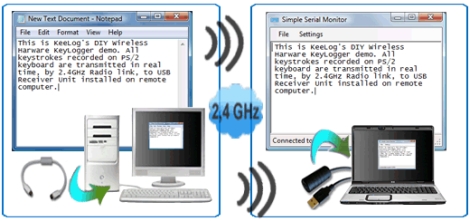
Do you need to keep tabs on the kids while they browse the Internet? How about your husband/wife – do you suspect they are dabbling in extra-curriculars on the side? Hey, you’ve got your insecurities reasons, we won’t judge. We will however, show you what [Jerry] over at Keelog has been working on lately.
While the company sells hardware keylogger kits online, [Jerry] has relied on, and understands the importance of open source. Since we all benefit from things being open, he is giving away all of the details for one of his most recent projects, a wireless keylogger. The keylogger plugs in to a PC’s PS/2 port, and wirelessly sends data to a nearby USB dongle up to 20 yards away, all in real-time.
A detailed parts list is provided, as are schematics, PCB masks, firmware, and assembly instructions. However, if you prefer the easier route, you can always buy the completed product or a DIY kit.
This isn’t the first open source keylogger he has released, so be sure to check out his previous work if you prefer a wired keylogging solution.