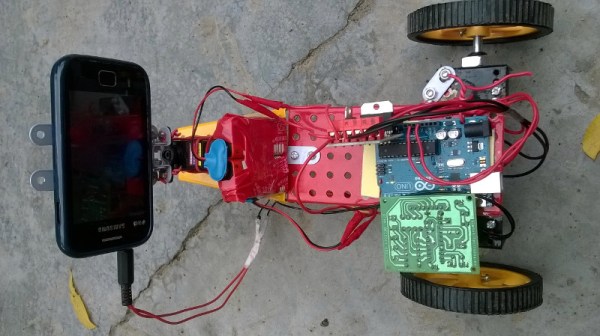
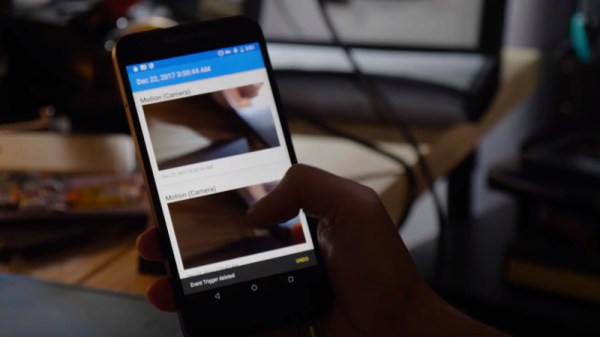
Famed whistleblower [Edward Snowden] has recently taken to YouTube to announce Haven: an Open Source application designed to allow security-conscious users turn old unused Android smartphones and tablets into high-tech monitoring devices for free. While arguably Haven doesn’t do anything that wasn’t already possible with software on the market, the fact that it’s Open Source and designed from the ground up for security does make it a bit more compelling than what’s been available thus far.
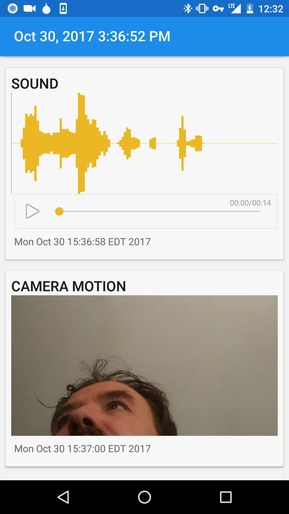 Developed by the Freedom of the Press Foundation, Haven is advertised as something of a role-reversal for the surveillance state. Instead of a smartphone’s microphone and camera spying on its owner, Haven allows the user to use those sensors to perform their own monitoring. It’s not limited to the camera and microphone either, Haven can also pull data from the smartphone’s ambient light sensor and accelerometer to help determine when somebody has moved the device or entered the room. There’s even support for monitoring the device’s power status: so if somebody tries to unplug the device or cut power to the room, the switch over to the battery will trigger the monitoring to go active.
Developed by the Freedom of the Press Foundation, Haven is advertised as something of a role-reversal for the surveillance state. Instead of a smartphone’s microphone and camera spying on its owner, Haven allows the user to use those sensors to perform their own monitoring. It’s not limited to the camera and microphone either, Haven can also pull data from the smartphone’s ambient light sensor and accelerometer to help determine when somebody has moved the device or entered the room. There’s even support for monitoring the device’s power status: so if somebody tries to unplug the device or cut power to the room, the switch over to the battery will trigger the monitoring to go active.
Thanks to the Open Source nature of Haven, it’s hoped that continued development (community and otherwise) will see an expansion of the application’s capabilities. To give an example of a potential enhancement, [Snowden] mentions the possibility of using the smartphone’s barometer to detect the opening of doors and windows.
With most commercially available motion activated monitor systems, such as Nest Cam, the device requires a constant Internet connection and a subscription. Haven, on the other hand, is designed to do everything on the local device without the need for a connection to the Internet, so an intruder can’t just knock out your Wi-Fi to kill all of your monitoring. Once Haven sees or hears something it wants you to know about it can send an alert over standard SMS, or if you’re really security minded, the end-to-end encrypted Signal.
The number of people who need the type of security Haven is advertised as providing is probably pretty low; unless you’re a journalist working on a corruption case or a revolutionary plotting a coup d’etat, you’ll probably be fine with existing solutions. That being said, we’ve covered on our own pages many individuals who’ve spent considerable time and effort rolling their own remote monitoring solutions which seem to overlap the goals of Haven.
So even if your daily life is more John Doe than James Bond, you may want to check out the GitHub page for Haven or even install it on one of the incredibly cheap Android phones that are out there and take it for a spin.
Continue reading “Edward Snowden Introduces Baby Monitor For Spies” →