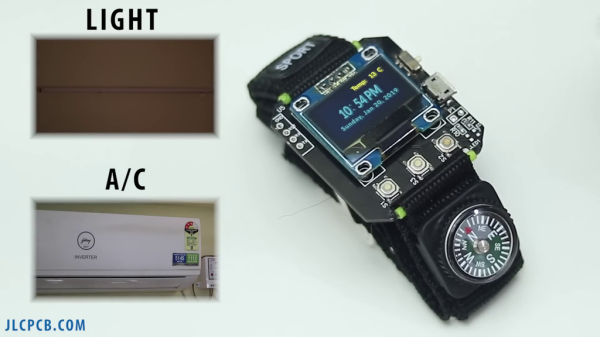
These days, we live in a post-Dick Tracy world, where you can make a phone call with your fancy wristwatch, and lots more besides. [akashv44] has gone a simpler route, designing their own from scratch with a bare PCB design.
The build is based around the ESP-12E microcontroller, providing useful wireless connectivity that lets the watch interface with the outside world. The firmware makes queries of NTP servers and Yahoo’s weather API to collect time and weather data for display. It’s also capable of interacting with Blynk relay modules for controlling other equipment, which [akashv44] uses with lights and an air conditioner. The watch uses a small OLED display and a handful of small surface-mount tactile buttons for control. Power is courtesy of a small lithium-ion pouch cell, with charging handled by a TP4056 battery management IC.
It’s a simple smartwatch, but nonetheless one that teaches all kinds of useful skills in embedded development and design. It’s also funny to think how simple it is to build. A decade ago, before the ESP8266 was released, getting wireless connectivity in such a small package was a major engineering challenge. Even the Apple Watch didn’t come out until 2015! Food for thought.