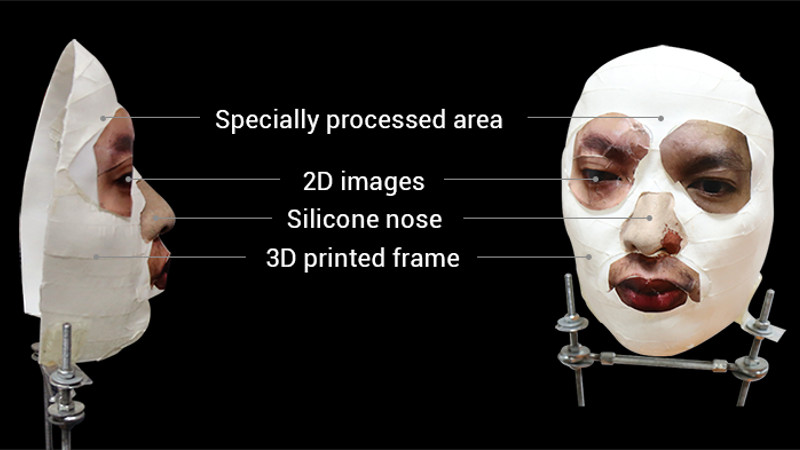
Information about this one is still tricking in, so take it with a grain of salt, but security company [Bkav] is claiming they have defeated the Face ID system featured in Apple’s iPhone X [Dead link, try the Internet Archive]. By combining 2D images and 3D scans of the owner’s face, [Bkav] has come up with a rather nightmarish creation that apparently fools the iPhone into believing it’s the actual owner. Few details have been released so far, but a YouTube video recently uploaded by the company does look fairly convincing.
For those who may not be keeping up with this sort of thing, Face ID is advertised as an improvement over previous face-matching identification systems (like the one baked into Android) by using two cameras and a projected IR pattern to perform a fast 3D scan of the face looking at the screen. Incidentally, this is very similar to how Microsoft’s Kinect works. While a 2D system can be fooled by a high quality photograph, a 3D based system would reject it as the face would have no depth.
[Bkav] is certainly not the first group to try and con Apple’s latest fondle-slab into letting them in. Wired went through a Herculean amount of effort in their attempt earlier in the month, only to get no farther than if they had just put a printed out picture of the victim in front of the camera. Details on how [Bkav] managed to succeed are fairly light, essentially boiling down to their claim that they are simply more knowledgeable about the finer points of face recognition than their competitors. Until more details are released, skepticism is probably warranted.
Still, even if their method is shown to be real and effective in the wild, it does have the rather large downside of requiring a 3D scan of the victim’s face. We’re not sure how an attacker is going to get a clean scan of someone without their consent or knowledge, but with the amount of information being collected and stored about the average consumer anymore, it’s perhaps not outside the realm of possibility in the coming years.
Since the dystopian future of face-stealing technology seems to be upon us, you might as well bone up on the subject so you don’t get left behind.
Thanks to [Bubsey Ubsey] for the tip.
















SO for someone to be able to get into your phone they would have to have a 3d sculpt of your face, with precise highres pictures of your face printed out. Don’t feel like the security of the device has diminished at all.
All it takes to get a decent 3D model of something is several pictures from different viewing angles, something you can easily get from Facebook, Instagram and the like nowadays. And the face model can be 3D printed, there are companies that can take care of that for you without all the hassle. Therefore, I believe that such kind of hack in principle could be performed by anyone.
Agreed. Facebook + Instagram = an ample source to generate a point cloud for most people. 3d printers are ridiculously inexpensive these days, and Hydro Dipping should provide a simple way to transfer the high-res photo onto the inexpensive 3d print.
As the write-up mentions we’re missing a lot of details about how the attack allegedly works. While the above sources would definitely be enough to build a relatively low-poly mesh (or, more likely, to choose blend target weights between a few representative face models) it may not be high enough fidelity to succeed.
With sufficient technical means both fingerprints and Passcodes are broken on smart phones. For example a video camera can infer a pass pattern on an android. It doesn’t even need to see the front side: just watching your elbows move is enough. Likewise finger print scanners can be forged too.
At least with a camera you can actually take a picture of the person and surroundings where the unlock is taking place .
This story is kind of fun from a hacker perspective of can you do it but not interesting from a security perspectives
Actually, all it takes for someone to take a sufficiently high resolution 3d scan of your face is apparently now just an iPhone, so no, it’s really not an excessive amount of effort.
Most biometric systems have always been less secure than passwords – just more convenient. It turns out that many human features don’t have nearly the same uniqueness-to-variability ratio as a secure password. And most of them can be copied by fairly casual observation…
https://www.youtube.com/watch?v=FhbMLmsCax0
Couldn’t you generate a 3D image of a face (using pictures from Facebook etc.), use that to project IR dots to a flat surface (2D picture of the face) according to the model, and cover up the built in IR projector?
You could try COLMAP to do pose recovery and re-build a 3D surface
Simulate the IR projection point-source as cylinders
Project the union 3D interaction back onto a 2D plane (using the viewing cameras physical pose offset)
Invert the 2D black & white image to make the IR filter
Laser print the constellation on transparency
Hold it up to the sun (or try an IR LED out of a TV remote) to unlock
I don’t own an iPhone, but couldn’t they pull the raw image off the same sensor to print the point map?
uhh… you discreetly walk by and record someone’s face on your Iphones IR-camera + projector.
You then playback this on the screen to unlock their phone.
I will soon sell a app for 4.95 USD that will do this. Ooh… maybe apple don’t like it?
There are loads of apps which track your face, not a big deal to extend those to do some photogrammetry and extract a mesh. Now, whether AAPL lets you do that in an app is another issue :)
If it’s a high value target you’d get 2 replica phones, one that you’ll leave on the bar next to them, that runs custom software that will record their face biometrics when they try to unlock it, mistaking it for theirs, and another that’s “dead” or messed up… so you use the first one, get their data, then some while later after they’ve confirmed that they have their phone now, you switch for the broken one, so they are not immediately aware that their phone is missing and think their phone has broken, then you run out the back or hand off to other operator who takes it to the “UPS” van out the back where you use collected data to unlock it, dump the data before they can iCloud lock it.
Or they are whacked with a crowbar and their phone is pointed at their face.
I thought it was a $5 wrench.
Pfft… A Cannon LP17 print-head guide bar from the scrap heap… Them things are free (if you know where they get scrapped and if you don’t price your own time*) and they pack a punch!
*For those who do price their every second minute and hour: Sleep is a big money loss! Have fun never sleeping again :)
A 3D scanner is fooled by a 3D copy of the object to scan? No wayyyyy, who would have guessed…
Did you miss the part where other groups have tried to fool it with 3D faces and failed?
Face ID is supposed to be “smart” enough not to be fooled by this kind of thing. Apple specifically said it had been tested against Hollywood-level masks and makeup and was supposed to be good enough that inorganic materials and that sort of thing would be rejected.
If this is real, then it shows Apple was at least partially BSing during the Face ID unveil. Or maybe worse, they actually believed their own claims and were just wrong.
They can also detect breathing, heart rate and eye movement in principle (ignoring patents). So a mask shouldn’t really fool it.
Maybe have machinery behind the mask to simulate the varoius pulses, twitching and maybe simulate eyes in there also…. Hmm, does this face-ID still work when the user changes her(sometimes his for culture reasons) make-up?
They can, but they don’t do it.
If they did, the mask wouldn’t work.
Did they try with the lights off?
As it also works in the dark(?). You can remove one more layer of security (color).
This is just stage 1 though. If it can successfully recognise a 3d model of the owner, you can then add distortions to find out just how accurate the model actually needs to be. Potentially leading to a (set of) generic face model(s) that attackers need just paste photograph fragments onto.
I think they said their face ID learns the changes to the face over time: i.e. facial hair, weight-loss etc.
So one could slowly change someone else’s face to be more like their own.
Adding distortions could be used to trick the face-ID adaptability into recognizing you as the original owner.
“We’re not sure how an attacker is going to get a clean scan of someone without their consent or knowledge,”
Photogrammetry. Collect as many images of the person’s face as can be found, from many angles, ideally with lighting from many directions. Scale using objects of known or findable dimensions in the images.
So a high definition video of them riding public transport for a while should do? :D
Or have them use your own iPhone for a moment, with some stealthy app scanning their face.
Nope, WAY easier than that. Hack an iPhone X’s camera and sensor system to just scan a face, collect the data, and Tada! Should take less than a second to get all the data you need once the system has been accessed.
To expand on this, I mean _any_ iphone X. Use it as a generic face scanning system. Just walk up to someone and say “what do you think of this cool picture”, they look at your phone, and boom, face scanned, picture taken, data collected. Or, since the actual hardware that does the scanning on the iphone X is so small, rip it out, and put it on a pair of glasses and scan faces all day long!
Another poster on another site pointed out the absurdity of using publicly available information to lock your phone… at least with a finger print, you’d have to get a close photo of their finger. But with a face? How do you hide that from scanning?
So…we should scan something else? Unlocking your phone in public could become quite embarrassing.
All biometrics are essentially just a long password, that may or may not eventually be able to be derived from a DNA sample, which you basically shed everywhere, that you can’t change WHEN it gets compromised.
True, but determining a 3D face profile from a DNA sample will probably stay science fiction for some more years or even decades. Combining some footage from a surveillance camera video seems to be already possible. AFAIK this is also one feature of the algorithms for autonomous cars to calculate a 3D representation of their surroundings from sequential images of ONE camera (not stereo), which gets different viewing angles due to the motion.
What about a locking system that is automaticaly unlocked and studies your behavior and locks you out if you deviate from your normal schedule? It’d only discriminate against people who use their phone irregulaly.
As in “User doesn’t normally wake up at 3AM and attempt to call 911, access denied.” :-D
i wonder why the screen is not turning on as he pulls the cloth off the mask.
normally when the scanner detects a face the screen turns on (you can see this when he points the phone on his face), instead he had to push the button to activate the screen and wipe up.
even tho he does a surprised “WHOA!” i am not convinced.
The clue is in the IR scanner, it’s not firing. You can see the blinking. I suspect it’s activated by the raising of the phone during normal use, or a combination of events can trigger it.
Notice it doesn’t start blinking until he raises the phone to his own face until the last moment. Not sure exactly what triggers it, but it’s plain to see that it’s not “super automatic” just because a face is in front of the phone. (as I have heard claimed)
I can imagine the battery drain required to scan for faces every second, all the time would be pretty bad. There needs to be an intermediate trigger to start the scanning.
Fondle-slab. Love it!
I believe The Register coined that term, some 5 years ago now, probably.
This one is a one-line proof:
Your face is not secret. Passwords must be kept secret to work as proof of identity. Thus, your face is not a password. QED.
The rest is implementation. Clever image recognition can make it hard to spoof, but it’ll never make it impossible. [Starbug] (and others) have proven time and time again that the “hard” part is never as hard as it seems.
The fact that these high-profile systems are broken within the first few weeks of their release into the wild is not coincidence.
The real trouble with this one is that Apple’s like “no government back doors” and then designs an unlock system that’s breakable with something that the government has in abundance — images of your face under controlled conditions. Let the conspiracy theories run wild!
Yes, don’t forget to exert your rights as a pastafarian to have your driving license photo taken with a colander on your head, so you can fit it with LEDs that wash out shadows and contours.
That’s it! Full tin foil balaclava!
Then We’d feel like all three a burglar, a conspiracy theorist and a hacker!!
You’re true to the point, bio-metrics can be bypassed as long as people find out what the software really is looking for.
It’s probably possible to use an FPGA or fast micro to emulate the camera and feed the phone the data in a form it expects and skip making a mask.
The NSA probably already has something like this implemented.
At first I thought this was about face identification in general, and expected a 3D printed mask that looks like a face to avoid survelience without letting people know you’re in a mask.
Look at the lock top center of the screen? when he uses the mask it doesn’t appear to change to the unlock symbol, which you can clearly see when he uses his actual face. Either that or my eyes are broken?
obtaining a “clean scan” should be fairly simple. all one needs is a couple of GoPros walking around with the auspice of shooting in public. any potential target would gaze directly into them without much thought. a second is all it takes and holds a wealth of data. weave the two images together for your depth data, and with minor scaling tweaks, send that off to your 3D printer.
Hence again Apple proved to be wrong and by integrating FaceID to ApplePay it’s just a disaster considering the security can be breached just with a 3D mask. FaceID is nothing but just another fun little thing integrated only to increase price of the iPhone this is not a security measure, at-least not yet.
David
https://tutuappx.com/