About a year ago, Zachary McCoy took a bike ride around his neighborhood in Gainesville, Florida. It may have been forgettable to him, but not to history. Because McCoy used an app to track his mileage, the route was forever etched in the Google-verse and attached to his name.
On the day of this ill-fated bike ride, McCoy passed a certain neighbor’s house three times. While this normally wouldn’t raise alarm, the neighbor happened to be the victim of a burglary that day, and had thousands of dollars worth of jewelry stolen. The Gainesville police had zero leads after a four-day investigation, so they went to the county to get a geofence warrant. Thanks to all the location data McCoy had willingly generated, he became the prime suspect.
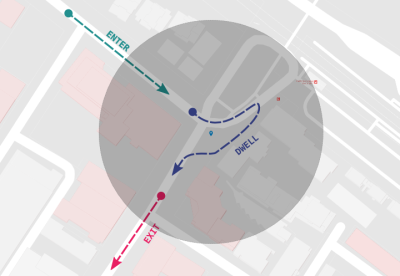
Bike Ride Inside the Geofence
McCoy had no idea about any of this until he received a vague email from Google ten months after the bike ride. The email stated that the police wanted access to all of his account information, and that Google would be turning it over to them unless he dropped everything, got a lawyer, and successfully blocked it in court within the next seven days.
The only clue in the email was a case number, which led him to the burglary report on the Gainesville Police Department’s website. Unsure what to do, he turned to his parents who hired a lawyer with money from their savings account. The lawyer quickly figured out that McCoy was being targeted because of a geofence warrant, which allows law enforcement to search Google’s vast Sensorvault archive for a list of all mobile devices that were active within a certain area during a specific time range. It’s the opposite of innocent until proven guilty, and as you can imagine, it fingers many innocent people.
The only shred of privacy left in this situation is that McCoy would remain anonymous up until the seven day period elapsed. Fortunately, McCoy’s lawyer was able to clear his name without releasing it to the police, although they certainly know it now that the case has made national news. How? The lawyer filed a motion declaring the geofence warrant null and void, which made the police backpedal. The state attorney’s office told McCoy’s lawyer that they found details that led them away from his client, and they simply withdrew the warrant.

EULA Text Walls Are Privacy Prisons
Like millions of people, Zachary McCoy has willingly sacrificed privacy in the name of convenience. Our more grizzled readers may be disappointed to learn that McCoy doesn’t read through those novel-length end user license agreements, and didn’t realize that he was allowing Google to keep a record of everywhere he’s been by turning on his location. Although it’s ultimately Google that made him have to hire a lawyer, they may not be the only bad guy in this particular equation.
The app McCoy used to track his bike rides, RunKeeper, which launched in 2008, has been around nearly as long as Android phones themselves. In 2016, the company that owns the app got in legal trouble in Europe because RunKeeper not only continues to track users when they’re not using it, it also sends user location data to a US-based advertiser.
It’s cliché at this point, but it bears repeating: nothing is free except maybe your mother’s love. If there’s no cost to you, then you are the product. Carefully consider what you join, and opt out while you can.
















We need true anonymization, but is that possible?
Leave your phone at home when doing sports.
The exact same thing would have happened if he was driving his car or walking to the store, so your advice is not very useful.
If you want anonymization, leave your phone at home when doing things.
You also might want to consider leaving your face at home.
leave your phone at home where it can listen in on your conversations, sniff your network traffic, and get pictures of all your bling so the thieves know where to look.
I leave mine in a jar by the door.
Who is it for?
The usefulness of a phone lies in having it with you. So that advice ic not very useful. But I avoid tracking apps and did not turn on the location history – although google often tries to nag you to give them more data.
You phone is your friend . . . you friend who can’t & won’t keep a secret.
………much like making a comment here and having to enter you email and a screen name . . .
With friends like those, who needs enemies?
The issue is not that he had a phone, it’s that he had a Google App RUNNING on his phone.
READ. If that doesn’t work, READ AGAIN.
Actually the article implicates RunKeeper. Not a Google app.
Runkeeper was the app demanding positioning beeing turned on, and Google took advantage of the positioning being turned on and saved all his data.
Personally, I don’t have positioning on unless I need to use an GPS app, but I have denied all Google apps positioning.
Now that doesn’t help much since the position also is saved at the cellcompany, derived from signal strength from all the towers around, a crude but still working positioning.
The problem here here is that the Police can ask for the data, and the companys not protecting it.
Where I live, the police needs to identify a suspect first, and in case of a serious crime (probably only murder) the phone companys can share it.
In extreme cases, (terrorism?) they can ask for a dump of the celltowers, but they can’t use it in a trial, they can only use it sift trough the people and find other evidence against them.
The position is in no way any evidence
I go one step further and use Netguard (a sort of Android firewall app) and set it so that, when enabled, only my SSH, Tor Browser, and OpenVPN apps are allowed to access WiFi. I block all apps from accessing the cell network by default. I only disable it if I need to use cellular data or want to visit a page using the chrome app or check my email. I disable location services completely and rarely ever turn those back on. I use maps sparingly, and only to find a location. I don’t generally need to know where I am on the map, since I read it as if it was a paper map.
Even if that’s true in this case, Android keeps track of where you are without running any specific app. You’ll end up being warranted with or without. You can turn off location services but doing so completely is deceptively difficult and Google tends to make a lot of unfortunate mistakes which negate those efforts.
Yes. It is possible.
Look back “if you are old enough” to just before today’s smartphones and cloud apps took over pretty much everything.
We had navigation. Sure, most of us just went to some navigation website and printed directions which of course leaves that company with the information that we are planning a trip. There were applications which ran entirely locally however. I knew one guy that kept a laptop running on the passenger seat of his van with a GPS attached but no internet. Obviously a laptop is much less convenient and less safe to operate while driving but if his 1990 something laptop can do it then surely a modern smartphone can.
We had voice recognition. Mostly it was a toy that nobody knew what to do with but it existed and it ran locally on those same 1990 something computers. Surely we can have voice assistants that do their voice recognition locally rather than send your unintended audio to the mothership.
But what about the social aspect? Those locally run 1990s programs didn’t have that. What was the real big technology before smartphones and the cloud that we thought was the up and coming big thing? P2P!!! We can build p2p enabled apps that allow us to share speed traps, show off to our friends that we just jogged to the end of the driveway, check in at the local cafe or whatever other crap one wants to share be it useful or inane. We don’t need a central server owned by some privacy killing company to do these things.
Of course running everything locally might harm precious battery life on portable devices. Well, if we hadn’t traded away removable batteries for pointless thinness that wouldn’t be as much of a problem. Personally I used to buy aftermarket, extra-thick extended batteries for my phones, usually carried a spare and had external chargers in my home, office and car.
But it doesn’t have to happen that way either. If our portable devices can send our information back to Google or someone else for processing they can be programmed to send it to anywhere. Why not to our own servers running off of plentiful wall power back home? They aren’t going to need powerful hardware when they only process one’s own stuff.
Of course not everyone wants to be a server admin. But, if we have apps that we can self-host someone else can host them too. Sure, this brings back a lot of the same privacy concerns but a free, open source app might be hosted by several competing small companies. No one of them would own enough of the market to make their data so valuable as today’s big corporations do. And none of them would be able to survive the negative publicity of a story such as the one here. They would be safer.
But this would be harder to use! A person would have to actually install something. They would have to configure it to talk to their personal server or whatever host they chose. They might have to forward a port on their home router. They would have to actually understand how their information is flowing through their technology. Normal people don’t want to do that!
Boo hoo. So what?!?
I keep going back to the 90s and early zeros for comparison to where it looked like technology was going. That was another great thing about that time. People were getting more technical not less. The amazing possibility of the internet necessitated it, even if it dragged them in kicking and screaming. Everyone was suddenly getting a computer and learning to use it even if they never had an interest before. Remember my friend with the GPS laptop? I’m pretty sure he was in his 50s when he got his first computer. And he was loving it! Before long he was tearing them apart, building up new ones and helping his friends. Learning isn’t that hard once you drop the “I don’t want to” lazy mental block.
As a society I think we have regressed. Things were looking promising technologically and then marketing took over and killed it. It’s time for a course correction.
I don’t think anyone is going to produce commercial software that works this way. There is just too much money on the table for someone who owns everyone’s data. The only hope is open source P2P software that starts taking back some of the functionality that has been abandoned to “the cloud”. Let’s go write it!
Completely agree. And yes it possible.
What’s “Geofence”?
I’m oblivious to it, so what’s the point of the story?
That means at the very least you should be explaining what this “Geofence” thing is.
A geofence is a virtual border around a geographical location. In this story it means that whoever was present in a certain area a couple of times automagically became the prime suspect in a case that was dead in the water. Apparently there was something in the EULA of the app that the suspect used that allowed Google to keep a permanent private-until-not record of it.
“The lawyer quickly figured out that McCoy was being targeted because of a geofence warrant, which allows law enforcement to search Google’s vast Sensorvault archive for a list of all mobile devices that were active within a certain area during a specific time range. ”
Even if you can’t parse that geofence is obviously a combination of “geographic” and “fence”, that sentence makes it pretty obvious.
A geographical fence is pretty real. Like a mountain range or river canyon or coastline. Maybe veofence is better for a virtual. Or even (Gasp!) “virtual fence”.
A geofence is a virtual perimeter for a real-world geographic area.
The cops had no leads so they were trying the “shotgun method” or broad search and see if anything sticks. They were wanting all the information of every user in the area for a set distance and time. That is why the privacy is mentioned. In the US you are supposed to be innocent till proven guilty but theses searches assume everyone is guilty and you have to prove your innocence.
Begs the question, the ‘suspect’ had to hire a lawyer, and one assumes he had to pay for that lawyer.
If you are innocent, but can’t afford that lawyer, your name gets put into a database (if he wasn’t quick, his name would have ended up there too) to be forever held as “a person of interest” when something happened in his neighbourhood.
So, what recompence does an innocent suspect have for [a] direct costs (eg: lawyer), and [b] indirect costs (eg: stress, time & reputation damage)?
It raises the question. See “begs the question” on Wikipedia.
When referring to an object or a fact, “begs” becomes synonymous with “raises” because the object or fact is not trying to make an argument. Only arguments or persons can beg questions in the sense of the fallacy.
Like, “This candle on the table begs the question, who brought it here?”, is perfectly valid. The presence of the candle is so surprising that it not only raises, but begs the observer to ask the question. It has nothing to do with the fallacy.
See, I told y’all that it wasn’t as obvious as “Mapwall”, nobody ever listens ;-)
I would have chosen “area search” if I was making up the words. An “area search warrant.”
the abbreviation is better “ar se warrant”
Pretty much everything if “free” unless they are 100% open source, record and track something. Google, Sony, Ubuntu, Microsoft, Apple record everything that you have searched for be it remotely or locally on “your” machine because you did agree to the EULA once, didn’t you or could it have been your dog/cat/snake/… that stepped/slithered on the mouse button at just the wrong time. As far as I’m aware no one, anywhere worldwide, has ever challenged in court of law that a click (possibly by an animal?) is a legal binding contract.
Even when you pay for things, they track you.
Even when you pay to opt out of the tracking, they track you.
I have an app that I paid for years ago that recently stopped working when I was on my home network. It turns out that the newest version was sending some tracking data to an ad network before launching the app. In the unpaid version, that meant a full-screen ad, but in the paid version that full screen ad was not displayed…and if the ad network was blocked (pi-hole) then…..the app just crashes.
And it worked fine for years before, so this was a deliberate change made by the developers in the last update.
Some time ago I was interested in buying an E-reader.
Glanced through the eula of kobo. Then went on to select another brand.
My Kobo is opensource and can easily run custom firmware. Perhaps you should have done a bit more research.
Nope.
Just because the software is open source does not mean they write a decent eula. It was something like: We push all the shit down your throat that we like, and everything you do with it will be sent to us if we like. I’ts part of their “user experience”.
I will not support companies that behave in that manner by buying their products. I’m not buying new hardware just to hack it to work in a decent way.
I have a Kobo, I switched off wifi immediately and blocked its MAC address in the router.
Ohh, good idea. That’ll stop my off-brand German Kobo from irritating me with adverts from their (useless, to me) store.
Time to flood the tracking with junk data and make it far less useful?
i try to avoid using software that cant be used anonymously (that is without a logon). but i doubt that is effective, as even your cpu spies on you, as well as the os.
I’m a software dev. My contract with one client specifically states that any click-wrap or similar I deploy in software I give them is invalid.
Thankfully, I don’t have to collect GDPR consents within the app…!
“… nothing is free except maybe your mother’s love”
Incorrect. There are no exceptions. Even a mother’s love eventually comes with an invoice that will be paid.
The problem is not with Google are whatever app you were foolish enough to install, or whatever you configuration/setup your equipment has/defaulted to. The problem is with law enforcement. As the victim of a violent crime, I can tell you that the police and the district attorney simply cannot and do not care about you as a victim or the offender or any ‘innocent’ bystanders or anyone outside of their tribe.
https://www.phoenixnewtimes.com/news/google-geofence-location-data-avondale-wrongful-arrest-molina-gaeta-11426374
https://www.abc15.com/news/region-west-valley/avondale/valley-man-suing-avondale-police-for-false-arrest
So it was his car and a phone in his name…I mean that’s pretty strong evidence TBH. Of all the things I can get worked up about, this one really does fall in to the “honest mistake” category.
Yeah, that pretty much sounds like some good investigative work.
Are you daft, illiterate or just plain stupid? It wasn’t his car or his phone. It was a SIMILAR car, and a different device that he used some time ago, a device owned by someone else.
“Molina says he later learned data provided by Google showed him in two different locations that night. His Google account logged in to two different devices: his phone, and someone else’s he’s logged into in the past. Molina admits he never thought that would tie him to murder.”
I see your point, but I still see it as bad policing. That “honest mistake” caused that man to lose his job, andf probably sent his life into free fall.
“… police say they have probable cause to arrest Marcus Cruz Gaeta, Molina’s mom’s ex-boyfriend, who Molina says would take his car without permission on several occasions…”
His account AND his car AND the arrest and interrogation led to the actual murderer. Sounds like good policing that solved an otherwise unsolvable murder.
It was a car that looked like his but wasn’t confirmed, and the phone was not his – it was another person’s phone who he had been using some time ago logged in to google, which then retained the login and reported to Google of “his” presence. You can read in the article that Google’s data showed him in two different locations on that day – but the police didn’t see the other location because it didn’t show up inside the warrant area.
This also shows how dangerous the whole thing is. If someone steals your google login, they can pretend to be you and get you in jail without anyone questioning why.
According to this https://www.howtogeek.com/411387/how-to-stop-googles-sensorvault-from-sharing-your-location-with-law-enforcement/ the person identifiable data stored by google that is accessed by law enforcement in these cases is the data stored when “location history” is turned on in Google setting. How-To Geek describes how to pause location history and also how to remove previously collected location history from a google account.
It tends to turn itself back on occasionally, like the setting where Google gets to collect your wifi network names.
What do you mean “it turn itself back on”? How? Isn’t Android open source? Shouldn’t that be an easy fix?
Other software that Google demands the manufacturers to put on your phone, and apps you might download, may request a change in settings whereby it turns silently back on. At best you get a generic permission request that says nothing about what settings are being turned on.
These settings are coupled with others, such that if you want to use AGPS in coordination with GPS to improve location resolution, it automatically turns the wifi discovery on as well and sends nearby SSIDs to Google. There are at least half a dozen different “services” that will send your location data to Google, that have to be turned off individually. For example, if you have “find my phone” enabled, your location is still being sent to Google every time you enable the GPS. There is no master switch that disables all tracking, and that’s by design – turning it all off is deliberately made difficult. Some of the settings are accessible on your phone, others require you to actually make a Google account and enter their website.
And the location history is a Google privacy setting. It has nothing to do with the Android OS.
After reading this I’m very confused… what this article (which is about another article from another source) is trying to suggest is that apparently you can be arrested for being in the neighborhood of a crime scene? I find this very hard to believe.
Requesting information doesn’t automatically mean you’ll be convicted? If your phone is near a crime scene, it doesn’t mean that the owner is at the crime scene and it certainly doesn’t mean that the owner of the phone has committed a crime.
From the way I see it, the police would like to get in touch with the owner of the phone that was near the location at the day of the crime, not to arrest the owner, but to ask some very intelligent questions. Like did you see anything suspicious. Perhaps this action could have resulted with a decent talk with people that could have been a possible eyewitness that had some useful info that was really helpful and could have lead to actually solving the crime…
Screaming… you can’t have my data, I’m innocent, doesn’t really help anybody, does it?
As I read it, it is a sensational story about nothing.
Some burglary happened and police is doing their job in sifting through possible leads to check whether they could lead to anything, and some guy panicking because he lives in a country where privacy is an illusion, just as most everywhere in this computerized world. It’s just that 1984 arrived a few years later then predicted.
Apart from that, when I go burglaring, I always leave my phone at home. This proves I could never have done it.
Haha!
“Did you have your phone with you when you burgled your neighbour?”
“Objection!”
So getting arrested, spending six days in jail, and losing your job as result of bad policing, is sensationalism?
Cops are maybe a half step above prison guards on the evolutionary ladder. Convicts are many, many steps above cops.
Ha! Appropriate that it looks like it was the prison guards that F’d up. The police asked to release him the next day, once they corroborated the details of his interrogation. It took 4 more days for him to actually get released.
>From the way I see it, the police would like to get in touch with the owner of the phone
How it works, Google informs the owner of the phone that they’re under a warrant and their information will be released in 7 days. During that time, you’re supposed to prove your own innocence or the police will get your information, at which point they can arrest you for investigation at their discretion. They don’t even have to give you a reason why you’re being jailed.
It’s basically arbitrary detention, which is a violation of human rights, but that is decided after the fact when you’re released. Then you have to sue them and go to court, where the judge will decide whether they had a just cause for the arrest.
In effect, unless you manage to prove yourself not guilty, and the police up and decides you’re guilty, you will be punished by detainment without a fair trial.
Of course this doesn’t apply to middle class white people – for them the police just wants to have a chat. The poor and the minorities are another question entirely. Some dude who got his phone stolen can easily end up in jail for no reason.
What do you mean arrest you and jail you? Could this guy have been jailed just like that? I mean, on what grounds? I thought that one goes to prison after the trial, and one can go to jail before the trial only if one is a fly risk or poses an imminent threat.
Yeah, he could be jailed, just like that. If he can’t make bail, then he stays there, whether he is a risk or not. Now he could hire a lawyer or get a public defender to get the bail reduced or eliminated, but that costs money and a public defender in many jurisdictions may not be provided for 30 days.
Much as I hate Google’s attitude to privacy, sounds like the real failure here is the US legal system.
At least in the UK there’s a legal aid solicitor on call 24/7.
Jail is not the same as prison. You don’t have to be tried to go to jail – the police can throw you in jail without telling you why for a limited amount of time, and whether they had any right to do so is decided only after the fact.
But you have to sue them for it. Welcome to the system.
I’m not sure I follow, what about “innocent until proven guilty”?
in reply to “what?”
In the US the legal system is so convoluted we have to hire people to understand it but.
It’s technically innocent until proven guilt. This would be under (to the best of my knowledge) the they are “detaining” you while they do their investigation not arrest but detainment which is a different legal status.
He was arrested pending charges, which usually have to be filed within 72 hours or they release you. The police requested his release the next day after they corroborated his allibi, but it took 4 more days for him to actually get released, for some reason.
Sorry, I was referring to the Arizona case. in my previous comment. This guy was never arrested or charged. A warrant was issued for his data so the police could identify him, likely so that he could be interviewed. There is no arrest at the the police’s discretion. They have to have probable cause. Google data alone is probably not probable cause in most cases.
“From the way I see it, the police would like to get in touch with the owner of the phone that was near the location at the day of the crime, not to arrest the owner, but to ask some very intelligent questions.”
Intelligent questions? Pull the other one. ESPECIALLY in the case of relatively minor crimes like this one, police are like used car salesmen except their question is “How can I put you in a jail cell TODAY?”
Did you even read the article? The police and DA were given solid evidence, alibis, and a more likely suspect. All of which they purposefully chose to ignore until the DA realized there was no viable case.
You have chosen a path of willful ignorance; or have close or emotional ties to LE. Neither will serve you well in making a rational analysis.
DA’s are political creatures. It is the stepping stone to State Attorney General, then the Governor or the US Senate or House. They just want convictions and opinions that get them press coverage and the attention of party leaders.
And people think I’m paranoid for always leaving my phone at home.
i simply don’t have one. i do not like carrying hundreds of bucks worth of tech on my person at any given time, and since my home computers have large screens and a full keyboard, makes the smartphone a little obsolete for my usage scenarios.
where it can listen to all your conversations, sniff your home network traffic, take pictures of yourself, your family, your possessions.
Yes, but are you paranoid enough?
probably not…
“If there’s no cost to you, then you are the product.”
While valid, I’m getting a little sick of this admonition. Almost no cloud services are available _at any price_ with a promise to maintain your privacy.
The only recourse is to not use _any _services—including your basic phone—if you wish to avoid tracking, etc.
You can use the F-Droid app store to install an openstreetmaps based app with routing features. You just download the map info, and then your data can be on your device.
There is only a server log of what maps you downloaded, not where you went.
The “if there is no cost” only applies when it is a service from a company. But there are other ways to get the services, even free services that respect privacy because they were donated.
With free software supported by ads, you’re still being used as a product to sell the ad companies. Then they get the excuse to charge other people the money for your app use, and it eventually circles back to you where you pay more for bread at the grocery store because someone else likes to play Candy Crush.
With free software supported by sponsors, you basically do what the sponsor wants you to do. If that means routing the search queries through Google, or forcing you to use Cloudflare as a DNS, etc. then you do that.
With free software paid by nothing, just relying on the good will of the author or donations, you usually get what you pay for. These software are typically incomplete, buggy, and abandoned just before applying the final polish because it gets too boring to develop.
Welcome to the surveillance economy.
If you’re not paying, you are the product.
Even if you are paying, you may still be the product… If you buy a device that depends on a free vendor cloud in order to operate or in order to provide all of its features (e.g. Nest), then guess what… Yep, you’re the product. The vendor is supporting their vendor cloud expenses by selling your data.
apparently on hackaday we are all products, maybe you should heed your own advice.
If they’re going to make you the product, what about (at least to them) make yourself a crappy product? As in generate fake data to show them how much you dislike that.
It doesn’t matter if the data is real or fake few of their clients will bother to notice the difference. They only care about volume and generating more data is actually helpful to them. Even worse your fake data increases your chance of being sent a real warrant leading to a real arrest.
What happen to P-Droid? wasn’t the only way to avoid tracking?
I see something odd in all this (but it’s hind sight now). Wouldn’t the same data prove the man’s innocence? A bike ride has a series of points that take a given time. Unless he stopped in front of the home for a given time he would have be riding at a given rate which would show were he was.
Of course at the time he probably need a lawyer to fight this until he could his hands on the data.
But it is a good example of unintended consequences of the user. But as is noted, even when you pay for a service you are still a product in another service.
They only asked for the data that showed him within close range of the house, so they didn’t have the other data that showed the rest of the ride. I’m willing to bet they’d somehow manage to claim that the other data was inadmissable, but the data showing him near the house was admissable, because that’s how the law works.
How this is different from Police checking traffic cameras and CCTVs in vicinity of a crime to find potential suspects then checking them opne by one and narowing down?
Data showed him passing 3 times near certain house its the same as traffic cam showing car with license plate XXXX and this guy behind wheel passed this spot three times during hours possible suspect would pass it. Normal procedure should be visit from Police and short talk maybe some digging to see if he should be investigated closer or excluded from suspect list.
that’s not actual evidence. And it’s a violation of our rights under the constitution. Everyone in this country has the ‘right to travel’ which means, traveling to and from anywhere cannot, and will not be cause for any sort of warrant, search, seizure, arrest, etc. It’s literally people like you that ruin our rights, because you don’t know what the f**k you’re talking about.
Actually it is very easy to stop this. You can install /e/ OS on your Android phone. It is unGoogled Android which doesn’t send any data to Google. I don’t even have a google account. I can still run android apps and that is all that matters. It’s a must for privacy.
Not compatible with my phone, and without access to Google’s Appstore I wouldn’t be able to install my online banking and identification apps.
So, useless.
So your bank relies on a paid third party service (device + data plan)?
How would you do mobile banking except with a mobile phone with data plan? Online banking on the PC is another thing.
The most amazing part of this story is that the police even bothered to investigate the burglary. Normality if your stuff is stolen the police come out, take a report and that’s the end of it. Sometimes they won’t even come over, they’ll take the report over the phone.
Hey, a fellow Lincolnite I see.
I remember back in the 1970’s 1977-78 to be exact, New York experienced the summer of Hell.
The city experienced it’s second blackout since 1965, and David Berkowitz, the Son of Sam, was shooting
women with a 44 caliber revolver. He was caught using a precursor to this geo-fence technology.
Using police work, they checked all the parking tickets in the general area of one of the murders, and his
Ford Galaxy had been ticketed for parking in front of a fire hydrant.
When they went to his apartment to ask him if he had seen anything etc., his first words to the police were:
“You got me, I’m the Son of Sam”. My father worked for WNBC/NBC news at the time and I can still remember
him grabbing my cassette recorder and tearing out of the house with it. Berkowitz lived less than a mile from my house.
So, in today’s world, I’m not surprised that the police would use location data to see what cellphones were in the area.
With kids today having cellphones at younger and younger ages, although I’m not sure how many actually ride a bike
anymore. The technology has its good points too. Ham radio operators use APRS to track their own location.
In one case a ham operator was using APRS in his car, and the car got stolen. He told the police, I know exactly
where it is. They did catch the thief. There’s a good and bad side to technology.
As far as true anonymity, unless you move way out into the woods, build your own cabin, power it with solar/wind,
grow your own food, and never contact another human being, that’s the only way you’ll be truly anonymous.
For decades it worked for the Unabomber. He never used technology which is why it took so long to get him.
I see a difference: This guy was caught, because he left a track with an offense (minor crime, misdemeanor), I am not sure what’s the correct US term for a traffic violation. The guy on his bicycle did not do anything wrong, at least in the sense of the law. He just generated too much unnecessary data.
Btw., here you can happily and legally park in front of a fire hydrant. Our fire brigade uses hoses, which are flexible enough to be not hindered by cars. Do they use rigid pipes in the US?
I know of a student who was in US more than 25 years ago and got such a stupid ticket for something which is perfectly legal here and US$ 50,- was at least at that time very much money for a student. Luckily the the due date for the ticket was after the flight home to Europe. AFAIK the person never heard anything again.
GPS on phone devices are pretty accurate now to a few feet. Not sure what app the guy was using, but most record time for averaging and the GPS data of the path you take. The police that reviewed the data should’ve seen that he didn’t veer off of his path (like ride up to the house that was robbed) or stopped for any period of time. I would say the police weren’t diligent in analyzing the data properly.
“Nothing is free except your mother’s love” How do you explain open source and free software. Isn’t this ubiquitous monetization the whole reason it came into being?
I don’t know if it is true but I’ve heard Italian authorities are handing out fines to cyclist for breaking corona quarantine based on online training trackers
It is unfortunate that this is ending up so far downthread where nobody will see it…
I was working on a now defunct project, the Neo900 which was a FOSS redesign and latest iteration of the well known(in FOSS circles) OpenMoko in a Nokia N900 form factor.
One of the defining features was hardware and software switches for all radio. More important was on the hacker-bus a planned POCSAG pager module. It would have been possible to toggle off all radios and run silent waiting for a page. Some simple UI software would let you quiclky boot up the cellular radio and call back in near real time but only if you felt like being on the air, location opt-in only mode. It was so revolutionary that even RMS, the guy who would not own a mobile phone said he would consider it(though he did not like the upgradeable firmware of the cellular modem).
Sadly the project lead had to exit and the project died.
I call on you all to finish your COVID-19 hacks and then get to work making us a modern FOSS computer-phone which includes an option to use existing one way pager networks to protect our privacy.
How far was that project, what is still missing and what are the resources needed? If people are to start working on this as you suggest, then they should be lead and organised for purpose.