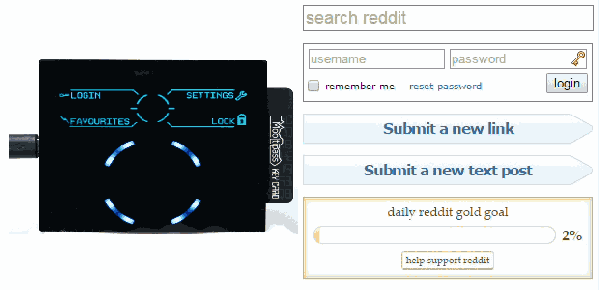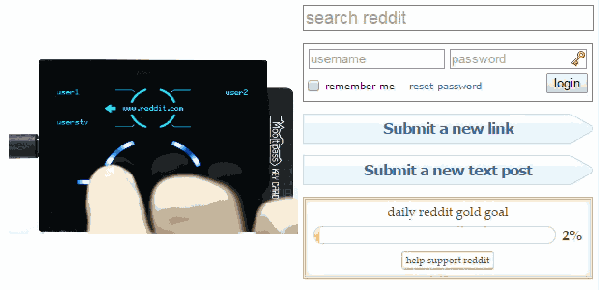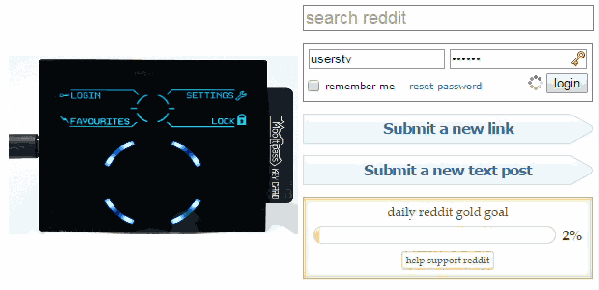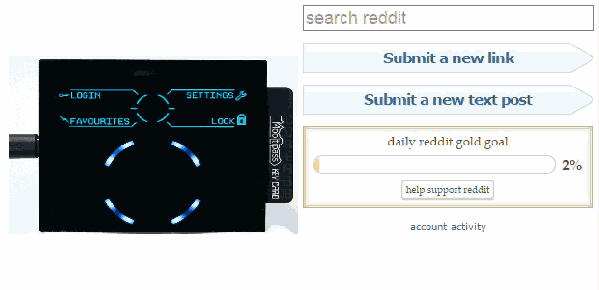
Remembering passwords is one of those things which one just cannot seem to escape. At the very least, we all need to remember a single password: namely the one for unlocking a password manager. These password managers come in a wide variety of forms and shapes, from software programs to little devices which one carries with them. The Mooltipass Mini BLE falls into the latter category: it is small enough to comfortably fit in a hand or pocket, yet capable of remembering all of your passwords.
Heading into its crowdfunding campaign, the Mooltipass Mini BLE is an evolution of the Mooltipass Mini device, which acts as a USB keyboard by default, entering log-in credentials for you. With the required browser extension installed, this process can also be automated when browsing to a known website. Any new credentials can also be saved automatically this way.
Where the Mooltipass Mini BLE differs from the original is in that it also adds a Bluetooth (BLE) mode, enabling it to be used easily with any BLE-capable device, including laptops and smartphones, without having to dig around for a USB cable and/or OTG adapter.
I have already been using the original Mooltipass Mini for a while, and the Mooltipass team was kind enough to send me a prototype Mooltipass Mini BLE for evaluation and comparison. Let’s take a look.
Continue reading “Hands-On: Wireless Login With The New Mooltipass Mini BLE Secure Password Keeper”



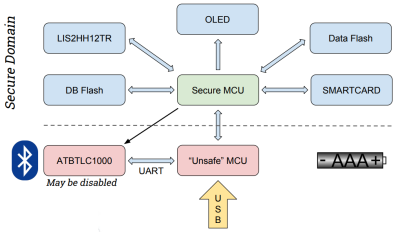 The key to the hardware is the use of a smartcard with proven encryption to store your passwords. Mooltipass is a secure interface between this card and a computer via USB. The new version will be a challenge as it introduces BLE for connectivity with smart phones. To help mitigate security risks, a second microcontroller is added to the existing design to act as a gatekeeper between the secure hardware and the BLE connection.
The key to the hardware is the use of a smartcard with proven encryption to store your passwords. Mooltipass is a secure interface between this card and a computer via USB. The new version will be a challenge as it introduces BLE for connectivity with smart phones. To help mitigate security risks, a second microcontroller is added to the existing design to act as a gatekeeper between the secure hardware and the BLE connection.