Over the years we’ve seen several attempts at adding Internet connectivity to the lowly wired doorbell. Generally, these projects aim to piggyback on the existing wiring, bells, and buttons rather than replace them entirely. Which invariably means at some point the AC wiring is going to need to interface with a DC microcontroller. This is often where things get interesting, as it seems everyone has a different idea on how best to bridge these two systems.
That’s the point where [Ben Brooks] found himself not so long ago. While researching the best way to tap into the 20 VAC pumping through his doorbells, he found a forum post where somebody was experimenting with optocouplers. As is unfortunately so often the case, the forum thread never really had a conclusion, and it wasn’t clear if the original poster ever figured it out.
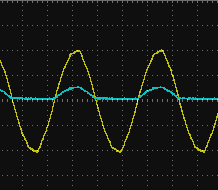
[Ben] liked the idea though, so he thought he would give it a shot. But before investing in real optocouplers, he created his own DIY versions to use as a proof of concept. He put a standard LED and photoresistor together with a bit of black tape, and connected the LED to the doorbell line with a resistor. Running the LED on 60 Hz AC meant it was flickering rapidly, but for the purposes of detecting if there was voltage on the line, it worked perfectly.
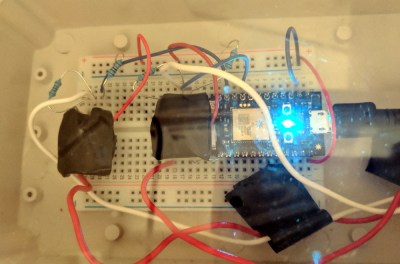
Wanting something slightly more professional for the final product, [Ben] eventually evolved his proof of concept to include a pair of 4N35s, a custom PCB, and a 3D printed enclosure. Powered by a Particle Xenon, the device uses IFTTT to fire off smartphone notifications and blink the lights in the house whenever somebody pushes the bell.
If you’re still wondering why it’s so tricky to connect a microcontroller up to your door bell, a quick look at some of the similar projects we’ve covered should give you a pretty good idea of how annoying these systems can be to modernize.