Aside from wanting to play around with nitric acid, [Ben] really didn’t have a reason to decap a few 74xx and 4000-series logic chips. Not that we mind, as he provides a great tutorial at looking at a bare IC that isn’t covered in epoxy and resin.
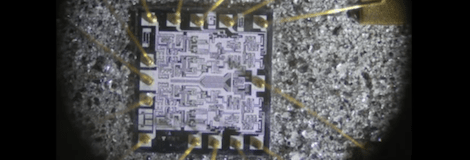
Most ICs are encased in a hard epoxy shell making it very difficult to look at the circuits within. [Ben] tried to grind this epoxy off with a Dremel tool, but didn’t have much luck until he moved over to a CNC mill to remove 0.040 – 0.050″ of epoxy without breaking the bond wires.
After carving out a nice pocket above the die, [Ben] put a few drops of nitric acid on the chip to dissolve the epoxy coating. This worked very slowly at room temperature, but after putting the chips on a hot plate the acid was able to reveal the die underneath.
After successfully removing all the epoxy and giving them an acetone bath, [Ben] took his chips over to the microscope and was able to check out the underlying circuit. He doesn’t have any idea what he could do with these decapped logic chips, but the bond wires are still intact so he could still use these chips in a build.
We’d like to see a few decapped MEMS devices, but if you have a suggestion on what [Ben] can do with his decapped chips, drop a note in the comments.
[youtube=http://www.youtube.com/watch?v=mT1FStxAVz4&w=470]
















Decap an old dram chip and use it as sensor for a camera. I remember people doing that back in the 80’ies.
Decap an old DRAM and turn it into a camera? Any IC should be fairly light sensitive.
DRAM is composed of arrays of tiny capacitors. A charge on a given cap signifies a “1”, no charge signifies a “0” (or vice versa.) These caps naturally self-discharge, and because they are so tiny, this occurs very rapidly. That’s why DRAM needs to be refreshed. In short, refresh involves periodically reading the entire contents of the array and rewriting it to “freshen” the charge on the caps. This, of course, must be done more quickly than the natural discharge rate of the caps.
Expose these caps to light, and they discharge more quickly. The RAM-chip-to-camera trick that @matseng is referring to involved exposing the DRAM die, and using a lens to focus an image on it. You’d write all “1”s to the die, wait some period of time, then read the contents. The most brightly illuminated cells will have decayed to become “0”s.
If you read the RAM repeatedly, and collected data over several frames, you could use a computer to generate a crude grayscale.
So, the DRAM trick had nothing to do with the light sensitivity of silicon PN junctions, so “any IC” wouldn’t work.
Thanks very much for the clarification. I was under the impression the storage cells in a DRAM were reverse biased PN junctions. Apologies for the duff info.
AFAIK it’s the gate capacitance of a FET, not an actual capacitor, not even a tiny silicon one. But it’s an effective capacitor. Perhaps the size of the gate in silicon makes it more light-sensitive.
I recall seeing in a video from the mid-80s, a BBC micro hooked up to a de-capped DRAM chip just like this, for a monochrome camera. Worked surprisingly well! They didn’t do the greyscale trick, but I bet it would have worked. But there was no grey in the BBC micro’s palette anyway!
Do even the cheapest 7400-series use gold wires to bond to the pads? I’d imagine even a penny worth of gold is going to count towards the costs of a 20p IC, or cheaper in quantity. Or can they use copper or something else for the cheap ones? And is this a reason they mount the bare chip on PCB (blob-top) in cheap gadgets?
I can remember back in 1982.. I brought an EPROM to a science-future-tech class in the 8th grade.
It was a large package, nearly 2″ long, with a quartz window to let the UV light in. The window allowed you to clearly see the chip and the wires, either with a naked eye or microscope.
I gave it to the teacher. Nobody else had ever seen such a thing. It was passed around each class. Everyone marveled.
Classes back then often watched boring “film strips”. They weren’t even movies. That chip was the most “future” thing those kids saw in that entire semester. I wonder how many years it was passed around among students? Back then, it was almost like “the chip” in Terminator 2 ;-)
You should NEVER combine nitric acid with acetone. This can easily become a lethal combination
That is VERY GOOD advice.
I’ll be more worried using methanol than acetone.
Although having followed Ben for some time now I’m sure that he did read all relevant MSDS safety data related and extensively researched the procedure to avoid a possible explosion or the formation of toxic compounds.
Some other interesting reads:
http://uvicrec.blogspot.com
http://siliconpr0n.wikispaces.com/
http://www.sparkfun.com/news/384
Dude, this dude’s lab setup is crazy boss.
We did it wih static ram chips, the idea is the mem array is in a grid to use as a camera. Any ic might be light sensitive, but you cant read data out in a sensible way
‘to remove 0.040 – 0.050″ of epoxy’ -.. lol hackaday just my 2 cents – don’t support mental retardation -> for god’s sake stop using imerial units
Did you mean “imperial”? If your going to call someone else retarded you should at least spell check first. lol
Improper spelling doesn’t invalidate his point.
lol true… though seriously the imperial system is for retards – it’s not only worse than metric – it’s also more difficult to use
oh yes, we all know that the imperial system is what cause the downfall of the British empire
you’re* !!
Learn to conversion. Also to spelling.
“Learn to convert. Also to spell.”
While I would love for hackaday to embrace the metric system, or at least offer measurements in both major systems in an article, the vision of arrogant jerks is not an image I would want them to associate with aficionados of the metric system.
I believe you will have far more success in your quest to convert people to the system of your choice, if you don’t denigrate them, but instead try to convince them of the superiority of your preferred units.
every person who has ever used metric will tell you that…
no need to be overly sensitive and forgiving – you and comments like yours makes them retards feel it’s ok to use imperial
it is okay to use imperial unit, just not ideal. Although, it is almost worth the inconvenience to see all you superior minds freak out over it.
That settles it. If I ever do a HaD post, I’ll use the most obscure units I can dig up: output pin spacing of 5.556 * 10^-3 cubits (2.54 mm)…
Because numbers are just numbers, but insults diminish us all.
decap, cut bonding wires, and build your own VLSI chips ;)
@nes
True, but I doubt a random IC has a neat grid of transistors side by side like DRAM. Maybe this grid provides some sort of pixels. However, I haven´t read or heard about this use before; its just what my intuition tells me.
String a lot of them together to make a very inefficient photovoltaic panel. It works with UV erasable EPROM chips, no need for milling machines, nitric acid and acetone.
Just 12 hours before this article went out, me and my brother did decap one of that plastic-blob IC’s from an old alarm clock and stayed the whole night looking at the microscope trying to figure out the circuit. We did use a file and some acetone for the work.
Decapping a MEMS IC? easy, get your soldering iron, set it to hotter then usual and desolder the metal top of your ADXL accelerometer, and peep inside.
Don’t some PN junctions generate light during operation? It would be awesome to be able to put an infrared camera on this chip while in operation in a circuit, with outside light blocked out…
…strip down an old webcam, invert the sensor, and just lay it on the die? You wouldn’t even need an IR filter if you immured the lot in black epoxy to keep out stray photons, though I dunno how well (or whether) it’d work — you might need to fool around with whatever filtering logic there is between the CMOS sensor and the USB interface. Might be worth a try for someone with the equipment and time to mess around with it, tho.
Next step is to reverse engineer the silicon
http://www.youtube.com/watch?v=Pp4TPQVbxCQ
to a. morita: manufactures like samsung toshiba siemens texas sony must do the clasical chips 741 555 565 with all transistors connections accessibly via pins in the BGA package.
Here are a few things I learned from reverse engineering 1980s vintage ICs and studying the circuits under the microscope. Most of these were ceramic packages where the de-lidding was trivial (an exacto knife), but a few DRAMS needed the fuming Nitric Acid treatment. The feature size was large enough to actually see the transistors.
Standard Microsystems COM8116 Baud Rate Generator: Uses a small 16 entry ROM to convert a 4-bit Baud Rate selection into a number to drive the Baud Rate counter. The ROM decoder was “folded” into the ROM array to make for an even more compact design. The Baud Rate counter was implemented using a Polynomial Counter (which consists only of flip-flops and a few xor gates). Each time the counter reaches the “zero” state, it preloads the counter from the ROM Baud Rate look-up table. This greatly simplified the counter design.
NEC uPD765 Floppy Disk Controller: Internally this is a microcoded part with a primative controller of NEC’s own design. Testing microcode embedded in a part can be troublesome. The uPD765 had a few extra gates associated with the DMA Request and DMA Ack pins. Presenting a certain illegal combination here places the part into a “test” mode and allows the sequencer microcode to be output on the normal Data pins. The sequencer microcode is responsible for high level commands such as Read Track, Recalibrate, Format Track, or Write Data. There is a similar test mode for the nano-code array which serializes data at the floppy disk head.
Motorola 68000 Microprocessor: This is a heavily microcoded Microprocessor with a large main array approximately 70 bits wide. It would be difficult to test the microcode by a series of microprocessor instruction, so instead a special combination at the Interrupt pins places the chip into a test mode and the microcode data is output on the chip’s 23 address lines. This is done as three passes for a total of 69 bits. (Internally there may have been an “A0” pad so that would have been 24 address lines x 3 = 72 bits.)
upd765 microcode, now that’s interesting. Would you mind sharing the magic trick to dump it? It would be extremely useful for when you want to do a really precise simulation…
OG.
…an additional note on the Motorola 68000: The data bus extends the entire width of the chip encompassing both the register array, and ALU, and barrel shifter. Driving such a long (capacitive) bus is programatic. In the 68000 the bus was split in half with a sense-amp style coupler isolating the two halfs. Thus a single transistor (from a register or ALU) need only drive half the bus. Once the sense-amp detects the transition, the *sense-amp* takes over and rapidly drive *both* sides to completion.
Just go out an buy a top end gaming mobo, decap all the chips on it and then recap them in clear epoxy resin, resolder to the mobo and voila, the coolest gaming mobo ever!
Stick it on Ebay and let it pay for itself and the time invested ;)
Yes, it would be very nice, but you forgot that the dies are 1mm-3mm in size. So not that beautiful to the naked eye…
Well, what to do with this hack ? Here is few idéas grabbing from days i’m working in a smartcard evaluation lab :
First, how to improve the decap procédure (for smatcards) : cover the card (chip) with parafin by putting him in molted parafin, then cut a little window in this parafin with a cutter just a the area you want to decap, finally put the protected card in nitric acid to disolve only the passivation layer.
– You can observe chip structure via a CCD cam, and localize interesting areas like eeprom, crypto-chip, etc …
– silicium absorb infrared light, so it is possible to hack (crack?) running code in time by using IR laser flash. See here :
http://www.cl.cam.ac.uk/~rja14/Papers/faultpap3.pdf
– by using an hold hard drive head coupling with a oscilloscope (via some high freq op amplificator) it’s possible to gather information leaking from the workin chip. You need to use very first generation hard drive head (more and more difficult to find) that was made by a ferrite U piece with a tiny gap between magnet poles. See here :
http://www.pcguide.com/ref/hdd/op/heads/techFerrite-c.html
– Now the global attack lab consist of : a home made rs232 card reader leaving the de-coated chip side wievable connected to a PC (to send/receive commands with the card), a hard drive head putted close to the chip and connected to a high freq working and deep memory storage oscilloscope, a sheme electronic generator (used to generate IR flash at precise time). Additionnal leaking informations can be grab by measuring electric chip consumption durring normal work (p.e. when the card activate the crypto processor the current consomption incrase …=)
That it ! Perform some google research with words ‘smartcards, fault attack, etc … for more on such topics.
Trasher
PS : sorry for my bad english writing, i’m a frenchy.