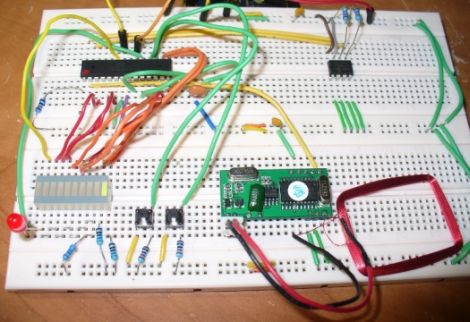
A few months back, [John] was reading an article about a simple RFID security system kit, and decided he would like to build one himself. While many of the system’s details, including full schematics were provided, he was dismayed to find that the source code for the project was not published as it was held under copyright by the manufacturer. Believing that open source is better, he modified the original design, replacing their PIC controller with an ATmega328 armed with an Arduino bootloader.
His system replicates all of the original kit’s functionality, while offering plenty of opportunity for modification beyond the initial design. The article contains a complete parts list, wiring schematic, and the Arduino code required to get things up and running. He even has a video of his clone at work, demonstrating the acceptance and rejection of RFID tags as well as the system’s learning mode.
















If you were to use this for access control, it is susceptible to someone sniffing your RFID tag and cloning it.
Is there anything you could do with this module and rf tags to avoid this?
I definitely want to port that project to my pc.
Some RF ID systems have a pin entry option so if your id tag is lost or cloned, the pin is needed.
More advanced systems use over the air encryption but most of these have been broken as the time needed to handshake is limited and onboard processor are not up to the job, as well as sloppy implementation.
When your RFID tag is stolen: Report it. The ops team can turn it off and give you a new one.
To prevent it from being cloned keep it in an RF resistant wallet. They are short range to begin with, so unless someone has access to your wallet you should be okay.
Correct me if I’m wrong.
With regards to the RFID entry system I built for my hackerspace (hsbne.org) we’re of the opinion that if you actually bother to sniff and clone a card to gain entry (as opposed to just breaking in via a window or something), you belong inside anyway :)
Now I just need to get around to finishing the IRC bot that will provide remote administration access…
@Mikey: Absolutely right about reporting a stolen card. However, regarding sniffing – AFAIK it’s not the card itself that gets “read”, it’s what the legit reader sends to the card. Since most cards are unpowered, readers do put out some amount of energy into the air to power the card when they talk to it, and _that_ can be read from somewhat further away with the right equipment (and yes, you can guess the ID by just listening to what the reader sends, go figure…). So look behind you when you use your card… ;)
There is a rather devious way around this, which is to deliberately send out “jamming” random numbers at apparently random but predictable by the software points during the receive cycles which are then picked up by the intercepting device.
You could quite eaily fox most RFID-sniffers this way :-)
This works because most common readers are “smart” enough to decode the streams from several chips at once because they send their signals out of sequence.