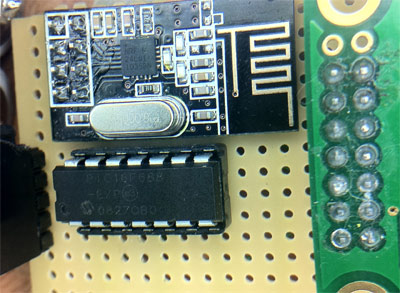
The Nike+ hardware is obviously an interesting device. We haven’t heard a whole lot about hacking one until now, but [Dimitry] has decided to change that. Many would assume that the data transmitted off of these sensors is quite simple, however there’s a bit more than meets the eye. Amongst other challenges, all the data packets coming out of the transceiver are encrypted. [Dimitry] claims to have decoded this data stream and made use of it.
This hack also outlines how one can use this without the stock iPod receiver using a 2.4 GHz chip from Sparkfun. A lot of work has been done to figure out how these packets are decoded and the process one goes through to do this is well outlined in this post. This could serve as a good example for those wanting to figure out similar devices.
One thing [Dimitry] hasn’t done yet is release the source code for this hack. He cites some ethical issues that might not seem obvious on first glance, including the ability to follow someone in a crowd or simply jamming their data. He does add though that if you have a good reason for wanting it, to simply email him. We’re looking forward to what [Dimitry] comes up with in the future using this setup!















He has posted the code just now, let the track… hacking begin!
The code was released as of yesterday, the page has been updated.
The ‘encryption’ can be decrypted with methods in all the crypto history books..specifically the oldest ones..
it’s a byte based caesar cipher..the proto is on microwave though so it takes buying stuff to reverse.
Please do read the code. It is not nearly as simple as you say (sort of why nobody’s managed to deal with it all these years despite trying [links in my article] )
And do note: the code IS posted on the bottom, contrary to what the article text says
I did..it only doesn’t use a fixed integer which is the only reason you need the extra routine..
I’ve reversed things way more complex..spare me the sensationalism..
http://en.wikipedia.org/wiki/Caesar_cipher
http://library.thinkquest.org/C0126342/ceaser.htm
Reading is a skill…
As is googling…
Caesar isa SHIFT cypher (addition modulo arithmetic). It is a simple map (C -> C where C is the same alphabet, and if c1->c2 in position X, c1->c2 in position Y, for y != X). Their cypher is XOR-based (and thus exactly NOT a shift cypher). Furthermore in their cipher position maters. A123 encrypted with Caesar and B123 encrypted with Caesar will both have last 3 chars of cyphertext equal. with their cipher that i snot the case.
If you would like a link to some good crypto books to read, let me know, I have a few recommendations. However I’d love to see this “way more complex” stuff you’ve reversed, what with your amazing knowledge of crypto :)
Reading is a skill…
As is googling…
Pleas google “caesar cipher” and read
Caesar is a SHIFT cypher (addition modulo arithmetic). It is a simple map (C -> C where C is the same alphabet, and if c1->c2 in position X, c1->c2 in position Y, for all Y != X). Their cipher is XOR-based (and thus exactly NOT a shift cipher). Furthermore in their cipher position maters. A123 encrypted with Caesar and B123 encrypted with Caesar will both have last 3 chars of cyphertext equal. With their cipher that is not the case.
If you would like a link to some good crypto books to read, let me know, I have a few recommendations. However I’d love to see this “way more complex” stuff you’ve reversed, what with your amazing knowledge of crypto and all:)
Would you mind sharing those books? I find it to be quite interesting and would love to read more about it.
whoops, forgot to add email (if necessary) tr202 at gmail dot com
shifting bytes based on an integer field is a caesar..Try to make me look uneducated some more..your knowledge is amusing..
P.S. I read all the books in my teens over a decade ago..before I did mathematics prerequisites for computer engineering and computer science which actually tested my skills before I went on to be a consultant and senior level engineer for a chip maker..
XOR is NOT a shift. a numeric shift for caesar is of form shift(x) { (x + shiftNum) % alphabetSz; }
Thus a shift satisfies the condition of shift(a) + 1 = shift(a + 1) in “mod alphabetSz” arithmetic. XOR can be easily shown to not satisfy this requirement. eg: if XOR value is 0x55 and “a” is 0xcc.
0xcc XOR 0x55 is 0xFF, (0xcc + 1) XOR 0x55 is 0xFE. 0xFF + 1 is 0x00 in “mod 256” arithmetic. and 0x00 is most certainly not equal to 0xFE
Perhaps it is time to review those books you read so long ago? “Senior engineers” who do not remember basics? I reject such job candidates in phonescreens – they do not even get to on-site interview (luckily)
ugh, i meant 0xAA instead of 0xCC. Should have had coffee first :)
Reminds me of some work Travis Goodspeed did a while back.
Same Dmitry Grinberg from the Palm old times, where he hacked tons of useful low-level utilities for PalmOS ?
The one and only :)
No quite the first to decode it
http://knz-blue.cocolog-nifty.com/memo/2010/02/linux-program-f.html
Noob…….
READ his work, the start bytes are completely different just for a start.
@Me(October 14, 2011 at 1:34 pm): that is a different product with a different protocol and no encryption…
You know what……
The guy put the work in, and all the bitches are complaining….
This is exactly the shit Hackaday was supposed to be clamping down on.
This stuff is amazing and exactly why I love going to hackaday! Good job Dmitry!
nice writeup dimitry! was a cool read!
kudos to disassemble the code ;)
Very impressive. Personally I would give up if I had to disassemble apple firmware :/
This is the kind of hack that I really like to see.
Always good when people reverse engineer proprietary stuff to make it more useful.
Why is a pedometer using an encrypted output stream? This is the little gem that doesn’t need a shoe sensor, right?
This is the reverse engineering of the protocol used by the wireless shoe sensor, the nike amp+ wireless ipod controller and the wireless polar heart strap compatible with nike+
I think Nike uses the ANT+ Standart (ultra low power RF modules for sensors). See http://www.thisisant.com
That is incorrect. Please refer to the data dumps I posted and to ANT spec to see the many differences. The data dumps are correct because I am able to both receive data from the sensor and parse it, as well as send data to iPhone, pretending to be a sensor and have it accept it and use it.
Well, it was only a guess (the T3 ANT modules uses a nRF24L01 chip and I read somewhere Nike has ANT+ sensors). Sorry for irritation.
Dmitry, I’ve been following your work since the Palm days. Great to bump into your work again. Respectfully, Andrew.