[Dev] sent in an interesting blog series on hacking Amazon’s kindle. [Igor] has documented getting a console, the bootloader and more. Even if you don’t have a Kindle to hack on, it’s a good overview of hacking similar devices. He used a cell phone cable to build his interface, but I suggest getting familiar with the MAX232 family of semiconductors for cheap rs-232 to ttl converters.
Month: February 2008
I’m Still Out Of Town Extra

I received some good stuff via the tips line while I’ve been making an extra stop after Shmoocon. I spent the day helping my less project endowed family run some new wiring (and made some awesome sparks in the process.)
[Damian] sent in his customized version of the classic Atari 2600 adventure game.
[iraqiGeek] sent in his efforts to use the six-axis controller. He used lib-usb and PPJoy to create his own app.
[HP Friedrichs] sent in this interesting post on building military style power supplies. Good stuff if you’re into building your own gear and like interesting chassis designs.
[John] sent in his version of the new KITT’s light bar. (You know you watched it.)
Got something good to share? Use the tips line.
Do Math To Turn Off Your Alarm Clock

[nickjohnson] sent in what might just be the most incredibly evil alarm clock ever. It’s a fairly simple pic project with a PIC, LCD and input buttons. When the alarm goes off, you have to solve math problems before it will shut off. If you answer correctly, you make it stop. In my case, I’d probably add a mute button that can be held down while you do the math. Source, schematics and pcb layout are provided.
The 2008 Shmooball Gun

I caught up with [Larry] from pauldotcom.com and got a quick walk-through of his Shmooball gun. After several less successful attempts, this one worked pretty damn well and featured a distinctive sound that caused a notable glimmer of fear in the eyes of the speakers. *cough*[renderman]*cough*. Read on for the secrets of the Shmooball gun.
ShmooCon 2008: Hard Drive Highlights

Today wrapped up with a talk on recovering data from solid state hard drives by [Scott Moulton]. The talk focused on the differences in data storage between SSD and platter technology. I did come away with a few interesting bits of knowledge. In an effort to extend device life, flash based drives store changed data to a new location, leaving the old data intact until a garbage removal subroutine gets around to clearing it out. Probably the best way to recover data from them will be altering or replacing the controller chip so you can access old data.
Yesterday I caught an interesting talk on recovering passwords from drive images by [David Smith]. He found that he could take a system image, strip out all the strings that were stored by various programs and use them to build a dictionary of possible passwords. By limiting string lengths and matching for known password policies, he was able to further filter his dictionary for likely passwords.
Toaster Oven Reflow Controller
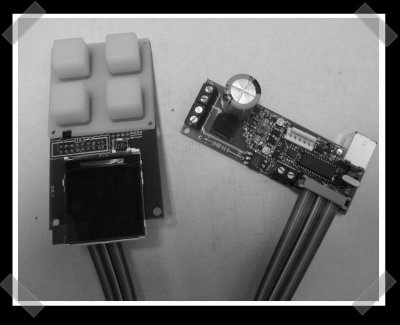
[Nathan] sent in his toaster oven reflow controller. He’s using a Triac to drive the heating elements, a thermocouple to monitor temperature and a PIC controller to run the show. I’m giving him extra points for style on the control pad. Hopefully he’ll have time to put out a complete write up when he’s got it finished. You can check out the project photos here.
ShmooCon 2008: Unauthorized Phishing Awareness Exercise

[Syn Phishus] presented a pretty interesting talk. At $former_company he prepared and executed a rogue internal exercise designed to heighten awareness of phishing scams. (That is, attempts to gather personal information from users with trickery.) After noting a certain lack of effort on the part of security policy implementation, he put together an official looking email, set up a simple phishing site that didn’t actually store any collected information and set loose the dogs of war. OK, he actually sent it to a select group within the company without warning anyone else ahead of time. He purposely didn’t store any of the results to protect the foolish, but he estimates that maybe 10% of the recipients fell for it.











